Samba bug allows remote attackers to execute arbitrary code as root
Introduction
Recently, 3 new vulnerabilities have been discovered in the Samba software. Samba is a free software re-implementation of the SMB (server message block) networking protocol. Samba delivers file and print services to a variety of Microsoft Windows clients, and it can work as a domain controller or a domain member within a Microsoft server domain.
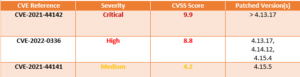
The CVEs identified are as follows:
- CVE-2021-44142:out-of-bounds heap read/write vulnerability in VFS module vfs_fruit allows code execution,
- CVE-2021-44141:information leak via symlinks of existence of files or directories outside of the exported share,
- CVE-2022-0336: Samba AD users with permission to write to an account can impersonate arbitrary services.
Cause of the flaw:
1.CVE-2021-44142
When opening files with smbd, a specific issue exists in the parsing of EA metadata. To exploit this flaw, you’ll need to log in as a user with write access to a file’s extended attributes. If such users are permitted write access to file extended attributes, this may be a guest or unauthenticated user. The issue in vfs_fruit is caused by the fruit VFS module’s default configuration, which uses fruit:metadata=metatalk or fruit:resource=file. The system is unaffected by the security flaw if both options are set to different values than the defaults. CVE-2021-44142 is the greatest among all the CVES mentioned above and impacts all the versions of samba before 4.13.17 and concerns an out-of-bounds heap read/write vulnerability in the VFS module “vfs_fruit” which provides compatibility with apple SMB clients. Samba prior to 4.13.17 is vulnerable to an out-of-bounds heap read/write vulnerability that allows remote attackers to execute arbitrary code as root on affected samba installations that use it.
2. CVE-2021-44141
Clients with write access to the exported part of the file system via SMB1 unix extensions or NFS can construct symlinks to any files or directories on the server disc. Clients can then examine error codes given by the smbd server to see if the target of the symlinks exists or not using SMB1 unix extension information queries. There is no way to access these files or directories; all you can do is check if they exist. If SMB1 is disabled and only SMB2 is utilized, or if unix extensions are disabled, there is no method to determine whether or not a symlinks points to a valid target using SMB2. As a result, even if symlinks are established via NFS, there is no method to exploit this flaw if the Samba server does not support SMB1 with unix extensions. Finding out what files or folders exist on a file server can aid attackers in determining system user identities, operating system versions, and applications running on the server hosting Samba, all of which can aid in mounting additional assaults. A malicious client can use server symlinks to discover if a file or directory exists in a section of the server file system not exported under the share definition in all versions of Samba prior to 4.15.5. In order for this attack to work, SMB1 with unix extensions must be enabled. Since Samba version 4.11.0 and forward, SMB1 has been deactivated. This bug has not yet been exploited in the wild.
3. CVE-2022-0336
When adding service principal names (SPNs) to an account, the Samba AD DC performs checks to ensure that SPNs do not alias with those already in the database. If an account modification re-adds an SPN that was previously present on that account, such as one introduced when a machine is linked to a domain, some of these tests can be evaded. By introducing an SPN that matches an existing service, an attacker with the ability to write to an account can launch a denial-of-service attack. Furthermore, an attacker who can intercept communications can imitate existing services, compromising confidentiality and integrity.
Recommendations:
1. SMB1 should not be enabled (SMB1 is disabled by default in samba from version 4.11.0 and onwards). This stops SMB1 from creating or querying symbolic links. Add the parameter: “unix extensions = no” to the section of your smb.conf and restart smbd if SMB1 must be enabled for backwards compatibility. SMB1 clients are unable to create or read symlinks on the exported file system as a result of this setting.
2. NFS clients can construct symlinks that allow SMB1 with unix extensions clients to discover the existence of the NFS created symlinks targets if the same area of the file system is also exported, allowing write access via NFS. We propose just exporting parts of the file system through SMB2 or NFS, not both, for non-patched versions of Samba.
3. To address the issue and stop any potential attacks using the vulnerability, Samba administrators are advised to update to these releases or deploy the patch as soon as possible:
- For fixing CVE-2021-44142, users can download the version from 4.13.17. All the versions prior to 4.13.17 are vulnerable to this CVE.
- For fixing CVE-2021-44141, users can download the version 4.15.5. All the versions prior to this version are vulnerable to this CVE.
- For fixing CVE-2022-0336, users can download these versions 4.13.17, 4.14.12 and 4.15.4.



