Pakistan-linked Malware Campaign Evolves to Target Windows, Android, and macOS
Operation Celestial Force, linked to threat actors with ties to Pakistan, has been an active malware campaign since at least 2018. This campaign utilizes GravityRAT, an Android malware originally designed for Windows, and HeavyLift, a Windows-based malware loader. Both tools are managed through GravityAdmin, a standalone command-and-control tool. Cisco Talos, a cybersecurity firm, attributes these activities to an adversary group known as Cosmic Leopard (aka SpaceCobra), which shares tactical similarities with the Transparent Tribe group. GravityRAT, which has evolved to target Android and macOS systems, is used to collect sensitive information from infected devices. HeavyLift, an Electron-based loader, targets Windows systems by gathering system metadata and periodically polling C2 servers for new payloads. GravityAdmin facilitates these operations with multiple user interfaces for specific campaigns, such as ‘FOXTROT’ and ‘CRAFTWITHME.’ The adversaries use spear-phishing and social engineering tactics to build trust with their targets before directing them to download malicious software. Cosmic Leopard’s focus has primarily been on Indian defense, government, and technology sectors, highlighting a sophisticated and persistent threat. The campaign’s success underscores the importance of robust cybersecurity measures, including regular updates, multi-factor authentication, and advanced threat detection.
Campaign Overview
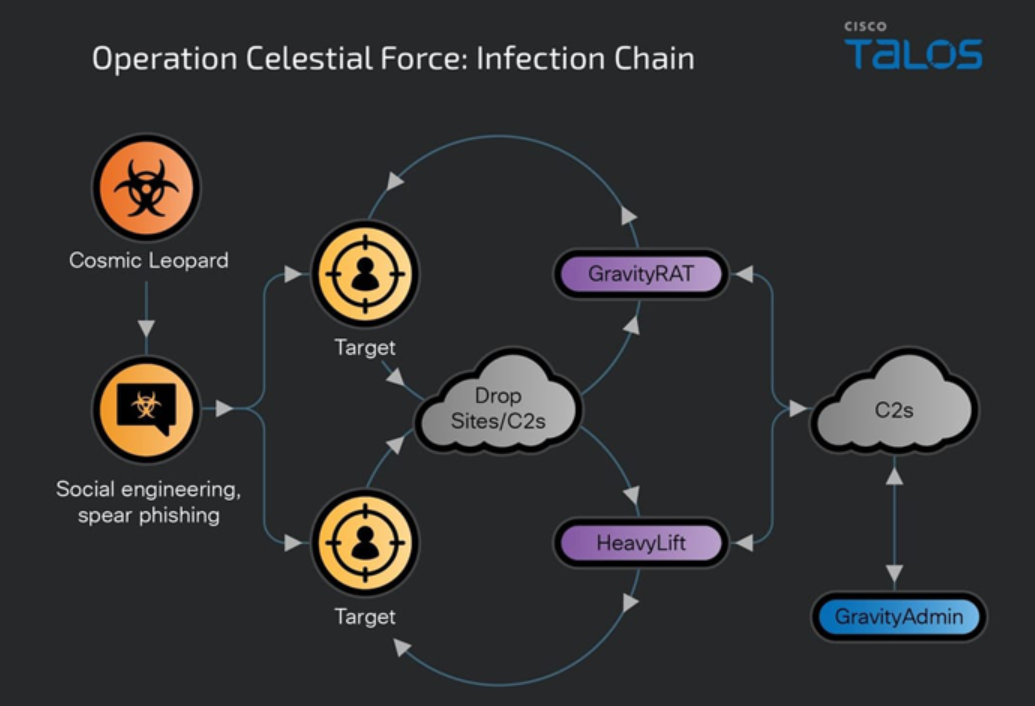
Operation Celestial Force has demonstrated considerable success in targeting users within the Indian subcontinent, reflecting its persistence and efficacy. Security researchers, in a detailed technical report, note that this campaign has continuously evolved and expanded its suite of malware tools over the years. This evolution includes the use of GravityRAT, initially a Windows malware, which has been adapted for Android and macOS platforms, and HeavyLift, an Electron-based malware loader for Windows. These tools are managed through GravityAdmin, a comprehensive command-and-control interface with multiple user-specific modules, like ‘FOXTROT’ for Android and ‘CRAFTWITHME’ for Windows. The adversary group, identified by Cisco Talos as Cosmic Leopard (also known as SpaceCobra), exhibits tactical overlaps with the Transparent Tribe group. Their methods predominantly involve spear-phishing and social engineering to gain the trust of targets, subsequently leading them to download malicious software. The campaign has primarily focused on sectors such as defense, government, and technology within India, leveraging sophisticated techniques and an ever-evolving malware arsenal to maintain its effectiveness. This highlights the critical need for robust cybersecurity measures, including regular software updates, multi-factor authentication, and advanced threat detection systems to counter such advanced threats.
Technical Details:
- Multi-Platform GravityRAT: Initially a Windows malware, GravityRAT now also targets Android and macOS devices, harvesting sensitive data.
- HeavyLift Malware Loader: An Electron-based loader targeting Windows, gathering and exporting system metadata to C2 servers.
- GravityAdmin Command Tool: Manages attacks via multiple UIs corresponding to specific campaigns like ‘FOXTROT’ and ‘CRAFTWITHME’.
- Spear-Phishing Tactics: Employs social engineering to establish trust with targets, leading to the download of malicious programs.
- Cosmic Leopard Group: Tracked by Cisco Talos, this group shows tactical overlap with the Transparent Tribe threat actors.
- Campaign Targeting: Focuses on Indian defense, government, and technology sectors, using evolving malware suites and sophisticated techniques.
GravityRAT: A Multi-Platform Threat
Initially detected in 2018, GravityRAT emerged as a Windows-based malware intended to infiltrate Indian organizations through targeted spear-phishing campaigns. Known for its dynamic capabilities, GravityRAT continually evolves to efficiently gather sensitive data from compromised machines. Its adaptation over time includes expansion to Android and macOS platforms, effectively transforming it into a versatile, multi-platform tool. This strategic shift underscores GravityRAT’s developers’ efforts to widen its operational scope beyond Windows, amplifying its threat across diverse operating systems. GravityRAT’s ability to persistently update and extend its functionality highlights its ongoing relevance and potential impact on cybersecurity landscapes globally.
HeavyLift: A New Addition
A recent addition to the threat actor’s arsenal is HeavyLift, a malware loader family built using Electron. It is distributed through malicious installers specifically targeting the Windows operating system. Notably, HeavyLift shares characteristics with Electron-based versions of GravityRAT previously identified by Kaspersky in 2020. Upon activation, HeavyLift initiates the collection and exportation of system metadata to a predetermined command-and-control (C2) server. It maintains regular communication with this server, periodically checking for new payloads that it can execute on compromised systems. Furthermore, HeavyLift is engineered to extend its functionality to macOS, indicating a capability to operate across multiple platforms and potentially increasing its impact and threat surface.
GravityAdmin: The Command Center
Since at least August 2021, GravityAdmin has been utilized as a binary designed to hijack compromised systems by establishing connections to the command-and-control (C2) servers associated with GravityRAT and HeavyLift. This tool incorporates multiple built-in User Interfaces (UIs) tailored to specific codenamed campaigns orchestrated by malicious actors. For example, campaigns targeting Android-based GravityRAT infections are dubbed ‘FOXTROT,’ ‘CLOUDINFINITY,’ and ‘CHATICO.’ Meanwhile, attacks employing HeavyLift are identified by names such as ‘CRAFTWITHME,’ ‘SEXYBER,’ and ‘CVSCOUT.’ GravityAdmin serves as a crucial component in these operations, facilitating remote control and monitoring of infected systems across various targeted campaigns.
Tactical Overlap with Transparent Tribe
Cosmic Leopard primarily relies on spear-phishing and social engineering techniques to build rapport with potential targets. Once trust is established, the actors send a link to a malicious website, directing the target to download what appears to be a harmless program. Unbeknownst to the target, this program installs either GravityRAT or HeavyLift, depending on the operating system in use. This tactic underscores Cosmic Leopard’s strategy of using deception to deliver sophisticated malware, enabling them to compromise systems and potentially harvest sensitive information from unsuspecting victims.
Historical Context and Evolution
Early Detection and Expansion
GravityRAT is believed to have been active since 2016. Recent investigations by Meta and ESET over the past year have uncovered the continued use of its Android version, specifically aimed at military personnel in India and the Pakistan Air Force. The malware is concealed within seemingly harmless applications like cloud storage, entertainment, and messaging tools. These discoveries underscore GravityRAT’s persistent presence over an extended period and its deliberate focus on targeting sensitive military organizations in the region through deceptive app disguises. This highlights ongoing cybersecurity challenges and the critical need for robust defenses against such targeted attacks in sensitive sectors.
Multi-Year Operation
Over the course of several years, this ongoing operation has persistently aimed at Indian entities, focusing on individuals associated with defense, government, and technology sectors. The campaign’s effectiveness can be attributed to its continuous enhancement and broadening of the malware suite, alongside the application of sophisticated social engineering tactics. By constantly evolving its tactics and expanding its malware capabilities, the operation has managed to maintain relevance and efficacy in targeting high-value sectors within India. This strategic approach underscores the threat actors’ concerted efforts to adapt to changing cybersecurity measures and exploit vulnerabilities in targeted sectors. The use of advanced social engineering techniques further enhances their ability to deceive and manipulate targets into unwittingly compromising their systems. Overall, the operation’s longevity and success highlight the persistent and evolving nature of cyber threats faced by critical sectors in India and underscore the importance of robust cybersecurity defenses and awareness among potential targets
Remediation Steps:
- Update and Patch Systems: Regularly apply security patches and updates to all software and operating systems to close vulnerabilities.
- Implement Multi-Factor Authentication (MFA): Use MFA to enhance account security and prevent unauthorized access.
- Conduct Security Awareness Training: Educate employees about spear-phishing and social engineering tactics to reduce the likelihood of successful attacks.
- Deploy Advanced Threat Detection Tools: Utilize endpoint detection and response (EDR) tools to identify and mitigate malware activity.
- Regularly Back Up Data: Maintain frequent backups of critical data and ensure they are stored securely and separately from the main network.
- Monitor Network Traffic: Continuously monitor network traffic for unusual patterns that may indicate a breach or ongoing attack.
- Limit User Privileges: Implement the principle of least privilege by restricting user access rights to only what is necessary for their job functions.



