Record-Breaking DDoS Attack on UAE Financial Institution by BlackMeta
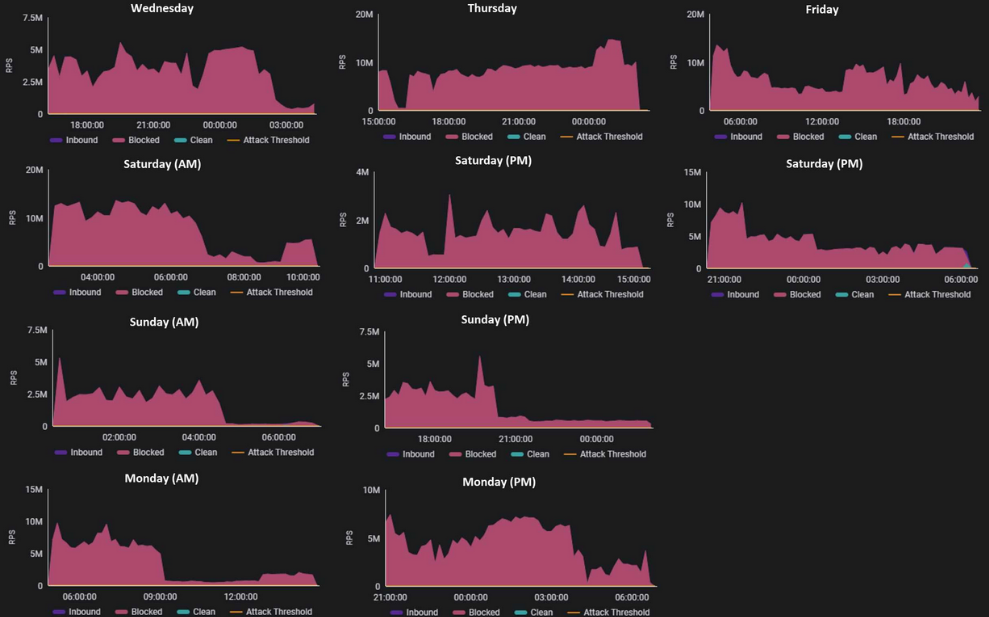
A financial institution in the United Arab Emirates experienced a record-setting distributed denial-of-service (DDoS) attack, notable for its unprecedented duration and sustained volume of requests. Attributed to the pro-Palestinian hacktivist group BlackMeta, also known as DarkMeta, the assault persisted for six days and included multiple waves of web requests. These waves varied in length from four to 20 hours each. The attack, which averaged 4.5 million requests per second (RPS), was significantly more prolonged and intense compared to typical hacktivist DDoS campaigns, which usually last between 60 seconds and five minutes. BlackMeta, a group that emerged in November 2023, has previously targeted organizations in Israel, the United Arab Emirates, and the United States. Prior to this operation, the group announced its intent on Telegram, overwhelming the financial institution’s website and reducing legitimate web traffic to as low as 0.002%. The attack leveraged the InfraShutdown service, which charges $500 to $625 per week to flood targeted sites. Primarily motivated by a pro-Palestinian ideology, BlackMeta also holds anti-Western views and may have links to Russia, often using Arabic, English, and Russian in their communications. The attack underscored the difficulty of mitigating application-layer DDoS attacks, which target specific web pages with randomized queries that appear legitimate, complicating defensive measures like rate limiting.
Key Insights
- The web DDoS attack campaign lasted six days and peaked at 14.7 million RPS.
- It featured multiple attack waves totaling 100 hours of attack time.
- The attack sustained an average of 4.5 million RPS.
- It targeted a financial institution in the Middle East.
- The average ratio of legitimate to malicious web requests was 0.12%.
- Radware attributed the attack to SN_BlackMeta, a pro-Palestinian hacktivist group with potential ties to Sudan and possible operations from within Russia.
- The attack likely leveraged the InfraShutdown premium DDoS-for-hire service.
Attack Characteristics
Duration and Volume
The DDoS attack endured for over 100 hours in total, with individual waves of requests lasting between four to 20 hours. The attack sustained an average of 4.5 million requests per second (RPS), as reported by cybersecurity firm Radware in an advisory published this week.
Comparison to Previous Attacks
Pascal Geenens, Director of Threat Intelligence for Radware, noted the significant departure from the standard hacktivist DDoS attacks, which typically last between 60 seconds and five minutes. In contrast, this attack campaign persisted for six days, with the targeted financial institution being hit 70% of the time by an average of 4.5 million requests.
Background of BlackMeta
BlackMeta, also known as SN_BlackMeta, emerged in November 2023 and has claimed responsibility for attacks against organizations in Israel, the United Arab Emirates, and the United States. Past attacks include a multiday DDoS assault on the San Francisco-based Internet Archive in May and an attack on the Israel-based infrastructure of the Orange Group in April. The group has also targeted entities in Saudi Arabia, Canada, and the UAE.
DDoS Attacks for Hire
Announcement and Impact
Prior to the operation, BlackMeta announced its intent to attack the financial institution on Telegram. The cyberattack overwhelmed the financial firm’s website with requests, causing the share of legitimate requests to drop to as low as 0.002%, with an average of 0.12%. The attack persisted for 70% of the six-day period.
Use of InfraShutdown Service
The attackers utilized a cybercrime service known as InfraShutdown, which enables attackers to target sites for $500 to $625 a week, according to Radware’s advisory.
Motivations and Affiliations
BlackMeta is driven primarily by a pro-Palestinian ideology but also holds an anti-Western stance. The group has potential links to Russia and communicates in Arabic, English, and Russian. Radware’s advisory highlighted that BlackMeta positions its attacks as retribution for perceived injustices against Palestinians and Muslims. Their typical targets include critical infrastructure such as banking systems, telecommunication services, government websites, and major tech companies.
Financial and Operational Aspects
Rebranding and Financial Gain
BlackMeta is likely a rebrand of Anonymous Sudan, a group known for collaborating with the pro-Russian Killnet group. Anonymous Sudan targeted Israeli organizations and Telegram in 2023. A comparison of claimed attacks by month over the past year and a half shows a decline in Anonymous Sudan’s activity as BlackMeta’s activity increased.
Anonymous Sudan previously advertised its InfraShutdown DDoS attack service, suggesting that BlackMeta is financially benefiting from its hacktivism. Radware’s advisory indicates that if BlackMeta is related to Anonymous Sudan, the premium InfraShutdown service is likely behind the 14.7 million RPS, 100-hour attack campaign.
Technical Challenges
Difficulty in Mitigation
Rate-limiting the bandwidth during such attacks is ineffective for sustained application-layer attacks. Differentiating between the 1.5 billion legitimate requests and the 1.25 trillion malicious requests over a six-day period is challenging. According to Geenens, the shift to Layer 7 (the application layer) complicates defense, as attackers can target specific pages and randomize queries to mimic legitimate traffic.
Remediation Steps
- Implement Web Application Firewalls (WAFs): Deploy WAFs to filter and monitor HTTP traffic between web applications and the internet.
- Use DDoS Protection Services: Utilize cloud-based DDoS protection services to absorb and mitigate large-scale attacks.
- Rate Limiting: Apply rate limiting to reduce the impact of high request volumes on specific endpoints.
- Traffic Analysis and Anomaly Detection: Continuously analyze traffic patterns to detect and respond to anomalies promptly.
- Geo-Blocking: Implement geo-blocking to restrict traffic from regions not relevant to your business.
- Redundancy and Failover Strategies: Establish redundancy and failover mechanisms to maintain service availability during attacks.
- Regular Security Audits: Conduct regular security audits and update security measures to address emerging threats.



