Cybercriminals Deploy 100K+ Malware Android Apps to Steal OTP Codes
A newly uncovered, extensive malicious campaign has been exploiting Android applications to illicitly access users’ SMS messages. This sophisticated operation has been active since at least February 2022. The primary objective of the attackers is to intercept one-time passwords (OTPs) sent via SMS, which are commonly used for verifying online accounts. By capturing these OTPs, the cybercriminals can bypass security measures and gain unauthorized access to users’ accounts. This method has led to widespread instances of identity fraud, as the stolen OTPs allow the attackers to impersonate the victims and carry out fraudulent activities. The scale and persistence of this campaign highlight the growing threat of mobile-based cyberattacks and underscore the need for enhanced security measures to protect sensitive information transmitted via SMS.
Overview of the Malicious Campaign
The campaign encompasses over 107,000 distinct malicious app samples specifically designed to intercept one-time passwords (OTPs). These apps are engineered to monitor SMS messages from more than 600 global brands, many of which have user bases numbering in the hundreds of millions. According to mobile security firm Zimperium, over 99,000 of these malicious applications were previously unknown and not available in common app repositories. This extensive operation underscores the significant threat posed by these apps, as they can covertly access sensitive information and facilitate unauthorized access to user accounts, leading to widespread identity fraud and other malicious activities. The scale and reach of this campaign emphasize the urgent need for robust mobile security measures and increased vigilance among users to safeguard their personal information against such pervasive threats.
Geographical Distribution
Victims have been detected in 113 countries, with the highest numbers in:
- India
- Russia
- Brazil
- Mexico
- United States
- Ukraine
- Spain
- Turkey
Attack Methodology
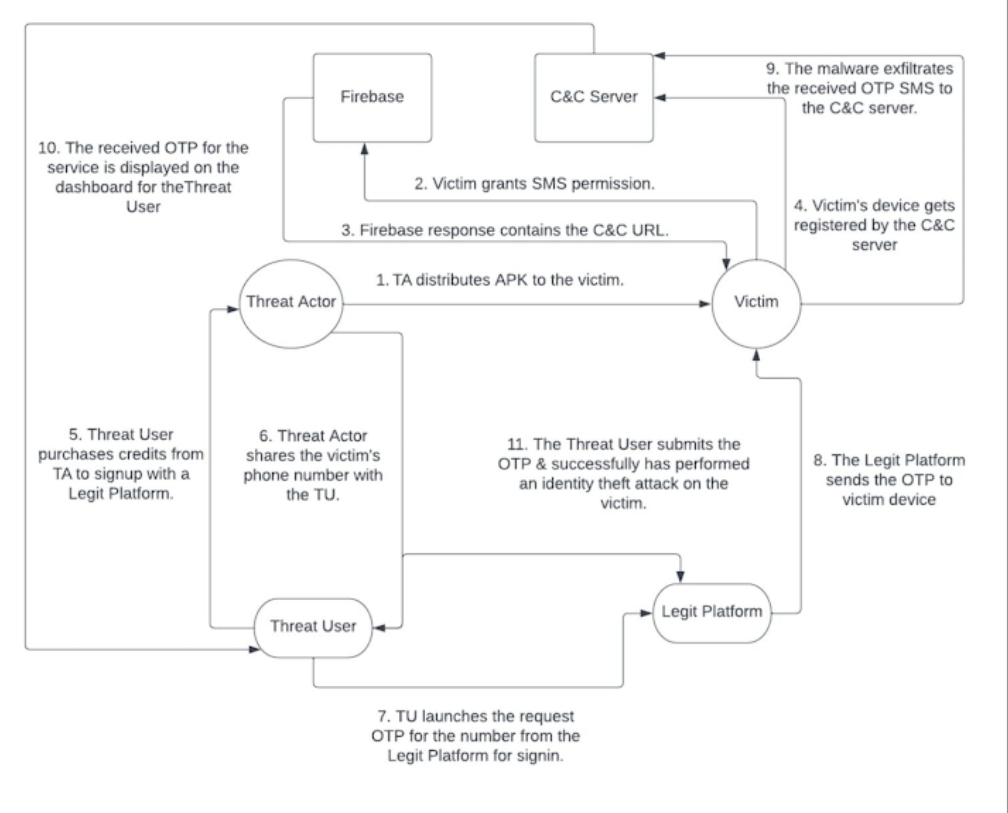
Initial Infection Vector
The attack begins with the installation of a malicious app. Victims are tricked into installing these apps via deceptive ads mimicking Google Play Store listings or through one of the 2,600 Telegram bots pretending to be legitimate services like Microsoft Word.
Permissions and Communication with C2 Servers
Once installed, the app requests permission to access incoming SMS messages. Upon granting this permission, the app reaches out to one of the 13 command-and-control (C2) servers to transmit stolen SMS messages.
Malicious Activities
The primary focus of the malware is to intercept OTPs used for online account verification. The malware continuously monitors new incoming SMS messages, remaining hidden on the victim’s device. It is suspected that the phone numbers associated with infected devices are being used to register for various online accounts by harvesting OTPs required for two-factor authentication (2FA).
Commercialization of the Stolen Data
The threat actors behind this operation are believed to be accepting various payment methods, including cryptocurrency, to fuel a service called Fast SMS (fastsms[.]su). This service allows customers to purchase access to virtual phone numbers.
Related Findings and Previous Reports
Trend Micro Report
In early 2022, Trend Micro reported on a similar financially motivated service that created a botnet of Android devices. This botnet was used to register disposable accounts in bulk or create phone-verified accounts for fraud and other criminal activities.
Google Play Protect
A Google spokesperson stated that Android users are automatically protected against known versions of this malware via Google Play Protect, which is enabled by default on devices with Google Play Services.
Abuse of Telegram for Malicious Activities
Propagation and C2 Communication
This campaign underscores the ongoing misuse of Telegram, a widely-used messaging app with over 950 million monthly active users. Cybercriminals are leveraging Telegram for multiple malicious activities, including the dissemination of malware and facilitating command-and-control (C2) communications. By exploiting Telegram’s vast user base and its robust, encrypted communication features, attackers can efficiently propagate harmful software and maintain control over compromised devices without detection. The platform’s widespread popularity and perceived security make it an attractive tool for malicious actors to coordinate their campaigns and evade traditional security measures. This trend highlights the need for heightened awareness and improved security protocols to address the exploitation of legitimate communication platforms like Telegram in cybercriminal activities.
Recent Findings by Positive Technologies
Positive Technologies disclosed two SMS stealer families, SMS Webpro and NotifySmsStealer, targeting Android users in Bangladesh, India, and Indonesia. These malware strains siphon messages to a Telegram bot controlled by threat actors. Other stealer malware strains masquerade as TrueCaller and ICICI Bank apps, exfiltrating users’ photos, device information, and notifications via Telegram.
Additional Malware Leveraging Telegram
Another malware, TgRAT, a remote access trojan for Windows, has recently been updated to include a Linux variant. TgRAT can download files, take screenshots, and run commands remotely. According to Doctor Web, Telegram’s popularity and routine traffic make it an easy vector for delivering malware and stealing confidential information.
Remediation Steps
- Enable Google Play Protect: Ensure Google Play Protect is enabled on your device for automatic malware protection.
- Install Apps from Trusted Sources: Only download apps from reputable sources such as the Google Play Store.
- Check App Permissions: Regularly review app permissions and revoke any unnecessary access, particularly for SMS messages.
- Use Security Software: Install reliable mobile security software to detect and prevent malware infections.
- Update Device Software: Keep your device’s operating system and apps up to date with the latest security patches.
- Be Wary of Phishing: Avoid clicking on suspicious links in messages or ads, especially those mimicking legitimate services.
- Educate Users: Raise awareness about the risks of downloading apps from unknown sources and the importance of cyber hygiene.



