Process Doppelganging Attack
A team of security researchers has discovered a new malware evasion technique that could help malware authors defeat most of the modern antivirus solutions and forensic tools. Process Doppelganging is an approach which abuses Windows NTFS Transactions and an outdated implementation of Windows process loader, which was originally designed for Windows XP but is currently being used in all the latest version of Windows. The attack is done by making fishy things look like legitimate Windows process which can easily bypass security products. The malware can eventually lead to ransom files, monitor keystrokes, or steal confidential information.
What is Windows NTFS?
Windows Transactional NTFS (TxF) was introduced in Vista as a method to perform safe file operations. To ensure data integrity, TxF enables only one transacted handle to write to a file at a given time. Until the write handle transaction is terminated, all other handles are isolated from the writer and may only read the committed version of the file that existed at the time the handle was opened. To avoid corruption, TxF performs an automatic rollback if the system or application fails during a write transaction.
NTFS Transaction is a feature of Windows that brings the concept of atomic transactions to the NTFS file system, allowing files and directories to be created, modified, renamed, and deleted atomically.
Vulnerability: Hackers leverage TxF to a perform a file-less variation of Process Injection called Process Doppelganging. It involves replacing the memory of a legitimate process, enabling the unwanted execution of malicious code that may evade defenses and detection. Process Doppelganging’s use of TxF also avoids the use of highly-monitored API functions such as NtUnmapViewOfSection, VirtualProtectEx, and SetThreadContext.
Process Doppelganging is implemented in 4 steps:
- Transact – Create a TxF transaction using a legitimate executable then overwrite the file with malicious code. These changes will be isolated and only visible within the context of the transaction.
- Load – Create a shared section of memory and load the malicious executable.
- Rollback – Undo changes to original executable, effectively removing malicious code from the file system.
- Animate – Create a process from the tainted section of memory and initiate execution.
Affected Versions: this attack works on all modern versions of Microsoft Windows operating system, starting from Windows Vista to the latest version of Windows 10.
Process Doppelganging Evades Detection from Most Antiviruses:
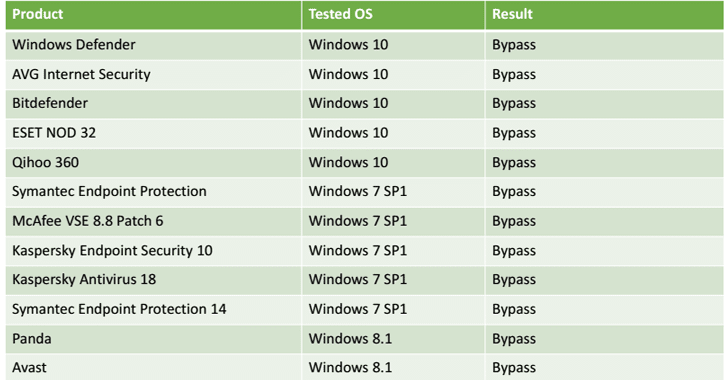
Similar to this, enSilo researchers have also disclosed a 17-year-old programming error in Microsoft Windows kernel that prevented security software from detecting malware at runtime when loaded into system memory. Process Doppelganging works on even the latest version of Windows 10, except Windows 10 Redstone and Fall Creators Update.
But due to a different bug in Windows 10 Redstone and Fall Creators Update, using Process Doppelganging caused BSOD (blue screen of death), which crashes users’ computers.
Later, the crash bug was patched by Microsoft in the coming updates, allowing Process Doppelganging to run on the latest versions of Windows 10.



