
What is a Wireless Security Assessment?
These vulnerabilities can be induced because of misconfigured wireless access point, vulnerabilities in the Wireless Access point’s firmware or the encryption and authentication methods for example WPA or WPA2.

Applicability
In a world where malicious intruders are always probing networks in search of weaknesses to exploit, you cannot afford to ignore any vulnerability, misconfiguration, or weak security control in your network eco-system. The security problem is further compounded by the increased use of remote access to networks via wireless technologies which have opened more opportunities for malicious intruders.
The convenience and ease of access to networks brought about by wireless communication have also made it easier for hackers to penetrate your information security system. An organization that doesn’t have a secure wireless system configuration will not detect, prevent, or control unauthorized network access. You need to conduct a wireless security assessment to determine the strength and efficiency of your wireless security settings and configurations.
Our CyberSRC wireless security assessment service is designed to address all the security challenges faced by businesses and organizations that rely on wireless technology in communication, financial transactions, and other business operations. Wireless technologies pose a significant threat to your IT infrastructure because their signals reach beyond outside physical boundaries and can be difficult to control. Without proper configuration and with weak security protocols, wireless connections are not only easy to access but they allow unauthorized eavesdropping too.
Objective

A Wireless Security Assessment will pinpoint vulnerable access points
A Wireless Security Assessment will highlight insufficient authentication, segregation and encryption
A Wireless Security Assessment provides best practice validation for your security set-up

PATROLLING YOUR ENTIRE PERIMETER
Wireless networks are an undoubted benefit for modern businesses but they also increase the number of access points through which an attacker can break into your systems. A Wireless Security Assessment will:
- Identify all your access points and assess their vulnerability
- Check the strength of your encryption security and user authentication
- Test the efficacy of your data segregation

WHY DO I NEED A WIRELESS SECURITY ASSESSMENT?
When you use a wireless network it enables your physical security controls to be bypassed and access gain to your systems. This can be through overlooked access points, such as a smaller office site, which is nevertheless connected to your servers, or an attacker sitting outside your office with a laptop or holed up in a nearby building with a powerful antenna. A Wireless Security Test will alert you to their presence, or potential presence.

HOW TO DISCOVER CRITICAL WIRELESS NETWORK SECURITY VULNERABILITIES IN AN OPTIMIZED BUDGET ?
Wireless networks ease the connectivity within the organization and increase the flexibility of working for the employees. This also increases the security risk associated with the wireless network which serve as a potential attack surface.
Wireless security assessment helps identify vulnerabilities and security risks in the wireless network. Our Security Consultants test for different vulnerabilities and perform different test cases to identify vulnerabilities in the wireless network. These vulnerabilities can be induced because of misconfigured wireless access point, vulnerabilities in the Wireless Access point’s firmware or the encryption and authentication methods for example WPA or WPA2.
- Avoiding Compromised Corporate Data: Security breaches are expensive and can cost an organization millions of dollars due to viruses, worms, Trojan horses, and illegal activities. Wireless penetration testing can help you avoid these traps by identifying risks before there is a security break.
- Evaluating Vulnerabilities: Wireless penetration testing can provide information on exploitable threats by enabling you to perform an audit. You can identify the most critical threats for an organization and prevent attacks before they actually happen. Keeping your organization’s systems and software up to date greatly reduces security risks.
- Setting Regulations and Policies: Wireless penetration testing helps organizations address security threats by settings rules or policies to protect their employees. Making sure that the sales department only has access to the sales information is key. You definitely don’t want your users snooping in on someone else’s files.

Thorough Analysis
Evaluate the entire code layout of the application including areas that wouldn’t be analyzed in an application security test such as entry points for different inputs, internal interfaces and integrations, data handling and validation logic, and the use of external API’s and frameworks.

Overcome Testing Limitations
Uncover vulnerabilities and detect attack surfaces that automated
code scans miss using security code reviews to detect weak
algorithms, identify design flaws, find insecure configurations and
spot insecure coding practices.

Meet Compliance Standards
Satisfy industry regulations and compliance standards including PCI
DSS standards.

Provide Solutions
Secure sensitive data storage and suggest precise solutions
customized for your developers with code level suggestions that
include more exhaustive checks to find all instances of common
vulnerabilities.
Approach
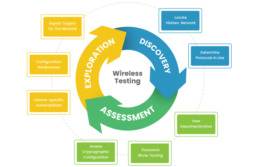
The wireless testing methodology primarily consists of 3 main steps. This majorly includes the strategy to penetrate the wireless network. This approach is a blend of password compound and sniffing technique for identifying the insecure wireless network.

Discovery:
Wireless Penetration Testing locates the hidden network within the system. This makes it possible to establish more intelligence regarding the protocols that are put to use.

Assessment:
Now during the actual assessment of the wireless network, validation or de-authentication of the user is executed. This enables to further brute-force the password for the access of the system. This further helps the testers to gain access to the cryptographic configuration of the wireless network.

Exploration:
The third step of exploration is inclusive of vendor specific vulnerabilities, configuration weaknesses and exploitation of the targets on the network.
With the step by step analysis and through work on the network, the team tries to perform the wireless network testing to mitigate it off any found issues and vulnerabilities.
WIRELESS SECURITY ASSESSMENT TEST CASES
- Default Credentials
- Eavesdropping on Traffic and Traffic Capturing
- Authentication and Authorization Vulnerabilities
- Weak Protocols
- Wireless Access Point Firmware Vulnerabilities
- SSID Beaconing and Checking for Hidden and Fake Wireless Networks
- Wireless Network Segregation
- Misconfigurations
- Brute Force Attack
- Evil Twin Attack
Why CyberSRC®?
Established in January 2018, CyberSRC Consultancy offers the full machination of cyber security services ranging from threat intelligence, VMS to general advisory services in areas pertaining to Cyber security such as vulnerability attacks, compliance, and cyber security regulations, and laws. We are into system audits such as ISNP Audits, NBFC Audits, UCB Audits, PPI Audits, and SEBI Audits. We provide our solutions with better accountability. We are a certified assurance firm. We are an ISO 27001 certified organization, backed by a very diverse and dynamic team which have a combined experience.
