
What is a Mobile Application VA/PT?
Any way to avoid any of the security risk is to opt for the Mobile Application VAPT that holds the power of providing us with a definite level of confidence when it comes to security maintenance and our CyberSRC Team provides you this level of security. According to various studies, more than 80% of mobile application users have the belief that their mobile finance and health apps are perfectly secure. Preliminary aim of conducting the Mobile App penetration test is to recognize all exploitable vulnerabilities in the app or network that can potentially get exploited by the hackers.
Most of the people downloads the malicious apps and then use that malicious apps that causes the potential risk to both yourself as well as your company as the untested apps might contain security bugs which can make the data vulnerable. Mobile Application VAPT will uncover several ways and access points in which the malicious hacker can compromise the application or database for gaining unauthorized access to the confidential data.

Applicability
Mobile application security testing involves testing a mobile app in ways that a malicious user would try to attack it. Effective security testing begins with an understanding of the application’s business purpose and the types of data it handles. From there, a combination of static analysis, dynamic analysis, and penetration testing results in an efficient holistic assessment to find vulnerabilities that would be missed if the techniques were not used together effectively. The testing process includes:
- Interacting with the application and understanding how it stores, receives, and transmits data.
- Decrypting encrypted parts of the application.
- Decompiling the application and analyzing the resulting code.
- Using static analysis to pinpoint security weaknesses in the decompiled code.
- Applying the understanding gained from reverse engineering and static analysis to drive dynamic analysis and penetration testing.
- Utilizing dynamic analysis and penetration testing to evaluate the effectiveness of security controls (e.g., authentication and authorization controls) that are used within the application.
Objective
Static analysis, with its whitebox visibility, is certainly the more thorough approach and may also prove more cost-efficient with the ability to detect bugs at an early phase of the software development life cycle. Static analysis can also unearth errors that would not emerge in a dynamic test. Dynamic analysis, on the other hand, is capable of exposing a subtle flaw or vulnerability that is too complicated for static analysis alone to be revealed. A dynamic test, however, will only find defects in the part of the code that is actually executed.

Static Analysis:
Static analysis is the process of analyzing an application without actual executing the application. Static analysis will review code of an application to find known or suspicious function calls or permissions that deem malicious.

Dynamic Analysis:
Dynamic Analysis is the process of analyzing an application while executing the app in a controlled environment. Dynamic analysis will monitor network traffic and other communications to catch malicious activity. With a powerful dynamic analyzer, applications that attempt to connect out to unknown or malicious sites, or send SMS messages without authorization will be flagged as malicious and consequently be reported as threats.
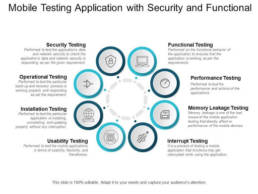
- Security Testing: Performed to test the application’s data and network security to check the application’s data and network security is responding as per the given requirement.
- Operational Testing: Performed to test the particular back-up and recovers the process is working properly and responding as per the requirement.
- Installation Testing: Performed to test particular application is installing, uninstalling, and updating properly without any interruption.
- Usability Testing: Performed to test the mobile applications in terms of usability, flexibility and friendliness.
- Functional Testing: Performed on the functional behavior of the application to ensure that the application is working as per the requirements.
- Performance Testing: Performed to test the performance and actions of the applications.
- Memory Leakage Testing: Memory leakage is one of the bad issues of the mobile application testing that directly affect on performance of the mobile devices.
- Interrupt Testing: It is a process of testing a mobile application whose functions get interrupted while using the application.
Standards for Mobile Application Penetration Testing?
In 2016, OWASP also began giving importance to Mobile Security. The mobile app developers must be familiar with the possible safety risks that the mobile application might encounter. In terms of OWASP mobile application security list, it is completely based on the data carefully collected from consultants and vendors over the period that is then analyzed as well as distilled to those 10 categories that consist most severe and common vulnerabilities in the industry.
OWASP Mobile TOP 10 2016 Vulnerabilities are –
- M1 – Improper Platform Usage
- M2 – Insecure Data Storage
- M3 – Insecure Communication
- M4 – Insecure Authentication
- M5 – Insufficient Cryptography
- M6 – Insecure Authorization
- M7 – Client Code Quality
- M8 – Code Tampering
- M9 – Reverse Engineering
- M10 – Extraneous Functionality
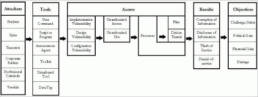
Approach

Discovery:
You can get information about an app by going through third-party libraries, search engines like Google, Yahoo, Bing, or finding the leaked source code by developer forums like GitHub, and social media etc. Having an understanding of the platform is a relevant aspect of app penetration testing. In terms of creating the threat model for an application, it gives you a better brief from an external point of view.

Assessment:
Mobile apps have a special way of assessment and all the testers should check an application pre as well as post-installation. It can be performed through static analysis without executing the app, on the decompiled or provided accompanying files and source code or dynamic analysis which takes place while an app is running on the device. You can also perform the Archive Analysis where app installation packages for the iOS and Android platform will be extracted as well as inspected for reviewing configuration files. Reverse engineering can also be attempted for converting compiled apps into human-readable source code.

Exploitation:
For demonstrating real world data violation an appropriately executed exploitation can take place fast. This includes:
- The attempt of exploiting the vulnerability
Acting upon discovered vulnerabilities for gaining sensitive information or performing malicious activities. - Privilege Escalation
Demonstration of the identified vulnerability for gaining privileges and attempting to become the superuser.

Reporting:
Creating the detailed report about discovered vulnerabilities, such as overall risk rating, the associated technical risk, and description etc.

Continuous Support
Why CyberSRC®?
Established in January 2018, CyberSRC Consultancy offers the full machination of cyber security services ranging from threat intelligence, VMS to general advisory services in areas pertaining to Cyber security such as vulnerability attacks, compliance, and cyber security regulations, and laws. We are into system audits such as ISNP Audits, NBFC Audits, UCB Audits, PPI Audits, and SEBI Audits. We provide our solutions with better accountability. We are a certified assurance firm. We are an ISO 27001 certified organization, backed by a very diverse and dynamic team which have a combined experience.
