
What is a Web Application Penetration Testing?
Web Application VAPT is a security testing method for security loop holes or vulnerabilities in web applications and corporate websites. Due to these vulnerabilities, websites are left open for exploitation. Nowadays, companies are moving their most condemnatory business and applications processes on the web. There is no denying on the fact that today, web apps are considered as vulnerability’s major point in the organizations.
The result of web application holes is a theft of plenty of credit cards, paramount reputational and financial damage for a lot of enterprises, and also the compromise of several browsing machines that visited those websites which were attacked by hackers. To avoid a scenario like this, WAPT maintains complete security and that is the major reason why it holds utmost importance for an organization. Web Application Penetration Testing is designed for detecting security vulnerabilities within the web-based apps.
In the times of intense competition, safety and security of your critical and sensitive businesses data are highly relevant. Unlike the other penetration testing, it also evaluates the risk that is related to a third-party app. Now, this makes it the best option for searching the web-based app’s security vulnerability that has previously been deployed as well as running. Penetration test carried under it is performed by manual and tool-based testing procedure.

Applicability
Web applications are computer programs that execute precise functions directly through a web browser, wherein the web browser is the client for the web application. They differ from traditional desktop applications that require software installation to run.
Essentially, web application security addresses the issues surrounding the security of web applications and services such as APIs and websites. They ensure that your information system is secure enough to protect valuable data and maintain operability.
Security is a vital consideration during all stages of the application development lifecycle, particularly when it is developed to address critical business data and resources. CyberSRC Web Application Penetration Testing will improve and ensure secure web application development by implementing security techniques and checkpoints from the first stages of the software development lifecycle (SDLC).
What are the Risks?
External facing Web Applications used by businesses are available to all via the public Internet. Their complexity and availability have made them an ideal target for attackers and there have been many publicized data breaches that have been caused by insecure web applications.
Protecting these applications from new threats is a constant challenge, especially for developers who are not aware of the security and who are working towards a performance deadline.

How Can Our Web Application Penetration Testing Service Help?
Pentest People can help alleviate the risks associated with IT Security issues by performing regular web app security of your public facing or internal Web Applications to identify the issues and to give you an ability to remediate these before an attacker would exploit.
Pentest People have a professional Web Application Security Testing services that can be used to identify vulnerabilities that exist on your web applications. Pentest People have a wealth of knowledge in the area of Web Application Security Testing and their testers have created and contributed to many open source web application security projects.
This Web Application testing can be performed remotely for external facing web applications or internally at your premises if the application is an internal application. The service would be delivered
Objective
Understand the web application security issues you face through a very thorough assessment from a qualified security consultant.
- Identify Security Vulnerabilities within your Web Applications allowing you to proactively remediate any issues that arise.
- Improve your security posture, allowing you to reduce the threat of a cyber-attack occurring against your business
- Comply with various regulatory bodies who mandate regular Web Application Testing be performed within your infrastructure
- Be able to prove to your supply chain that you are taking the necessary precautions to ensure your strong security posture.
- Be able to focus efforts on important security issues by identifying the high-risk items identified in the Web Application report
Approach
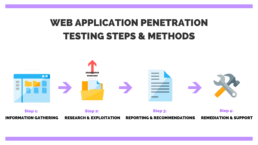

Information Gathering
The penetration tester of a WAPT provider locates publicly-accessible information related to the client and finds out ways which can be exploited for getting into systems. The tester employs tools like port scanners for completely understanding the software systems in a network. With the use of this information, tester pinpoints different findings’ probable impact on the client.
Vulnerability Detection
Testers of the right online WAPT provider understands the response of a target app to several intrusion attacks. Static as well as dynamic analysis is used in this situation. The former method is used to check whether the application code is behaving in the exact way it should be while running or not and the latter one involves its inspection in the running condition.

Report and Analysis
The test’s result is consolidated and compiled into the report that briefs the sensitive data accessed and particular vulnerabilities exploited etc. This report is analyzed by security personnel to create strong safety solutions.

Retesting the Vulnerability
———————————————————————-
———————————————————————————
Why CyberSRC®?
Established in January 2018, CyberSRC Consultancy offers the full machination of cyber security services ranging from threat intelligence, VMS to general advisory services in areas pertaining to Cyber security such as vulnerability attacks, compliance, and cyber security regulations, and laws. We are into system audits such as ISNP Audits, NBFC Audits, UCB Audits, PPI Audits, and SEBI Audits. We provide our solutions with better accountability. We are a certified assurance firm. We are an ISO 27001 certified organization, backed by a very diverse and dynamic team which have a combined experience.
