Amazon’s Ring Video Doorbell Lets Attackers Steal Your Wi-Fi Password
Security researchers at Bitdefender have discovered a high-severity security vulnerability in Amazon’s Ring Video Doorbell Pro devices that could allow nearby attackers to steal your Wi-Fi password and launch a variety of cyberattacks using MitM against other devices connected to the same network.
Ring Doorbells have become one of the most popular internet-connected doorbells installed in smart homes. These devices provide motion-sensing and video surveillance capabilities that allow users to see and communicate with anyone outside their door using an app — even if they’re not at home.
Vulnerability: The vulnerability stems from when the device is first configured to the local network, when the Ring smartphone app needs to send the wireless network connections to the Amazon Ring servers in the cloud. This takes place in an insecure manner that can be exploited by an attacker: not only does the device create an access point without a password, but the credentials of the network are also sent using HTTP, which means they can be exposed to snooping from nearby attackers.
To gain access to network credentials as they are transferred via an open network, the attacker needs to trick the user into believing their device is malfunctioning so that they rerun the initial authentication process that leaks the network details.
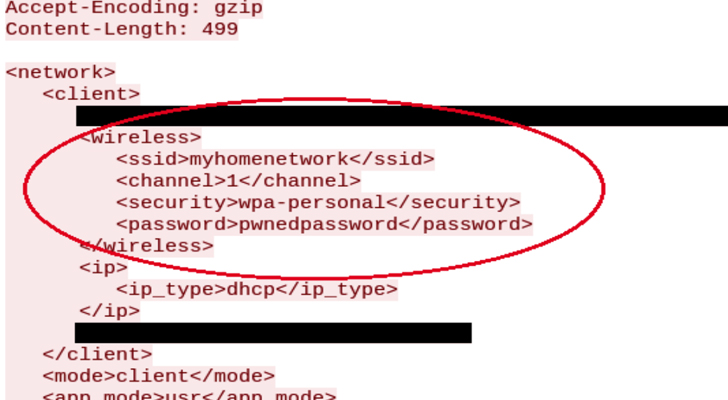
One way to do this is by sending de-authentication messages that appear to show the door is no longer connected to the internet. This leads the app to suggest that the device should be reconfigured. When the user goes through this process, the plain text credentials can be sniffed by the attacker with the aid of relatively simple open-source tools. With these credentials, the attacker could use them to connect to the router themselves — and any other devices without password protection on the network. Once the owner enters into the configuration mode to re-share Wi-Fi credentials, the attacker sniffing the traffic would capture the password in plaintext, as shown in the screenshot.
There’s also scope for accessing other IoT devices on the network and interacting with them in ways that could breach the Ring user’s privacy — such as listening to or watching IP camera footage from within the home. Once in possession of a user’s Wi-Fi password, an attacker can launch various network-based attacks, including:
- Interact with all devices within the household network
- Intercept network traffic and run man-in-the-middle attacks
- Access all local storage (NAS, for example) and subsequently access private photos, videos and other types of information
- Exploit all vulnerabilities existing in the devices connected to the local network and get full access to each device that may lead to reading emails and private conversations
- Get access to security cameras and steal video recordings.
On discovering the vulnerability, Bitdefender contacted Amazon Ring and the company has since delivered a security update.
Remediation: Ring Video Doorbell Pro users should make sure they have the latest update installed. If they are using the updated version they’re safe.



