IoT Security : A big concern For The Experts !!
What is IoT ?
The Internet of things (IoT) is the network of devices such as vehicles, and home appliances that contain electronics, software, sensors, actuators, and connectivity which allows these things to connect, interact and exchange data.
The IoT involves extending Internet connectivity beyond standard devices, such as desktops, laptops, smartphones and tablets, to any range of traditionally dumb or non-internet-enabled physical devices and everyday objects. Embedded with technology, these devices can communicate and interact over the Internet, and they can be remotely monitored and controlled.
What makes IOT devices more vulnerable ?
IoT devices run on low power and less computing resource capability, due to this they cannot afford to have complex security protocols. Hence, it becomes an easy target for intruders.
IOT elements that are vulnerable to attacks:
- Firmware
- Hardware devices
- Web application in IOT
- Mobile applications in IOT
- Wireless communications
Firmware
Firmware is a kind of software that is written to a hardware device in order to control user applications and various system functions. The firmware contains low level programming code that enables software to access hardware functions. Devices that run firmware are known as embedded systems which have limited hardware resources, such as storage capabilities as well as memory. Examples of embedded devices that run firmware are smartphones, traffic lights, connected vehicles, some types of computers, drones, and cable set-top boxes.
Exploiting the Firmware
Obtaining firmware
In order to start reviewing firmware contents, we first have to get hold of a firmware binary file.
Ways to get the Firmware
- Download from the vendor’s website.
- Search it on the internet.
- Dumping firmware directly from the device
Now you have the firmware of the device, we now have to analyze the firmware binary file to find vulnerability.
Our Approach
- Reverse Engineer the firmware binary file.
- Analyze file system contents.
- Perform both Dynamic and Static analysis.
- Look for both sensitive information or vulnerabilities, and a backdoor.
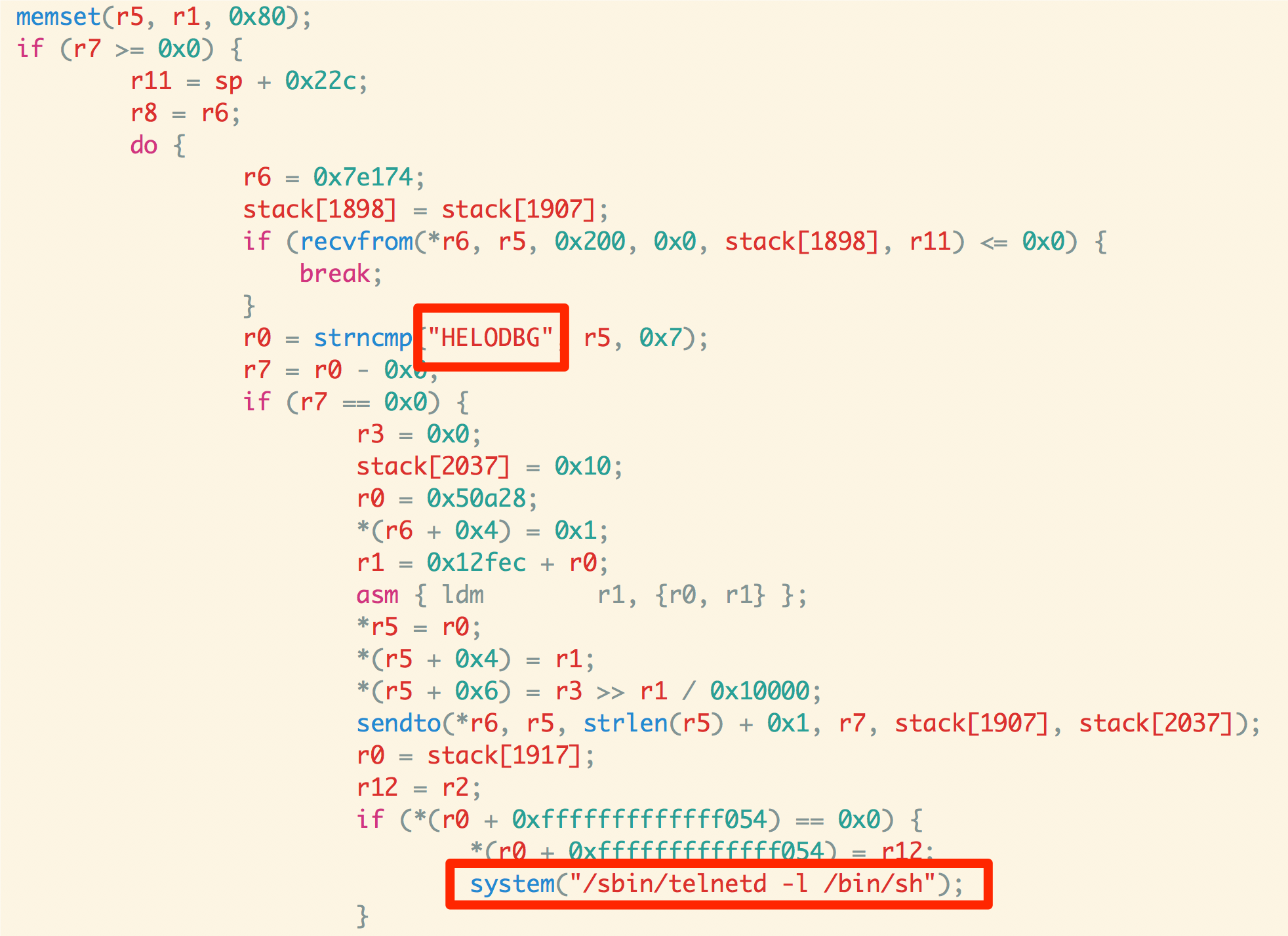 Fig: The backdoor found inside a firmware (Pseudo code)
Fig: The backdoor found inside a firmware (Pseudo code)
As we can see from the preceding screenshot, it does a strncmp for the stringHELODBG. As you will probably already know, strncmp is used for string comparison, which in this case is checking for the string which is required by the binary to launch Telnet as it is evident from the highlighted boxes.Thus, we can confidently say that the appmgr backdoor looks for the string HELODBG and as soon as receives the string, it launches Telnet with bin/sh shell.
How to prevent firmware from being exploited ?
- Hardening embedded frameworks.
- Securing firmware updates.
- Follow the best practices.
Mobile Application in iot
In the IoT space, mobile applications are similar to the web application models previously discussed. Although discussing specific details about security models for mobile device platforms is beyond the scope of this book, having a foundational knowledge of mobile application development models will help with testing when moving forward.
Exploiting the mobile application
In IOT the devices are controlled through a mobile application from where users can setup personal configuration and check the connected systems.
To implement it, the owner sends a command for synchronization with the hub. At that moment, all settings are packed in the config.jar file, which the hub then downloads and implements.
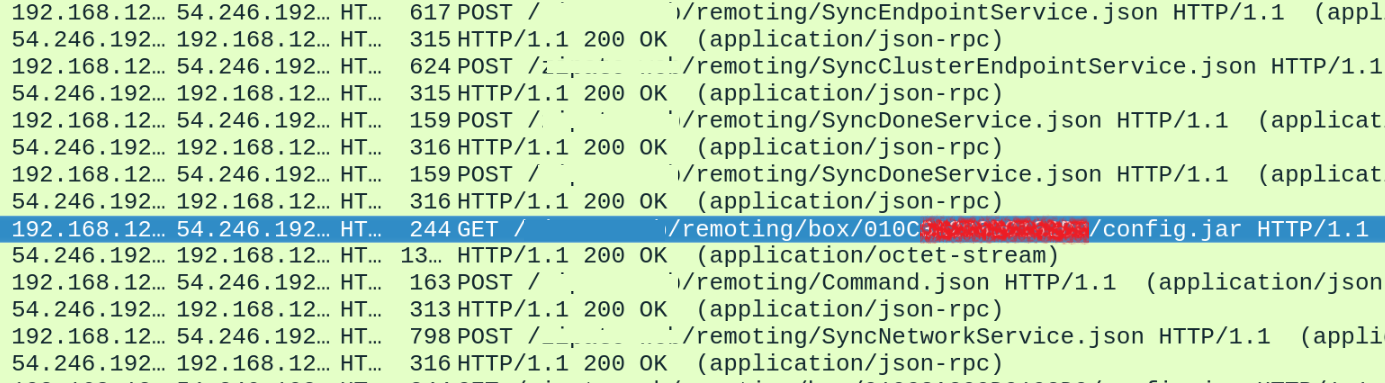
But as we can see, the config.jar file is sent through HTTP and the device’s serial number is used as the device identifier. So, hackers can send the same request with an arbitrary serial number, and download an archive.
Some might think that serial numbers are very unique, but developers prove otherwise: serial numbers are not very well protected and can be brute-forced with a byte selection approach. To check the serial number, remote attackers can send a specially crafted request, and depending on the server’s reply, will receive information if the device is already registered in the system.
Moreover, our initial research has shown that users, without even realizing it, put themselves at risk by publishing their tech reviews online or posting photos of a hub in social networks and openly presenting devices’ serial numbers. And the security consequences will not be long in coming.
While analyzing the config.jar file archive, we found that it contains login and password details – all the necessary data to access a user’s account through the web-interface. Although the password is encrypted in the archive, it can be broken by hash decryption with the help of publicly available tools and open-sourced password databases. Importantly, during the initial registration of a user account in the system, there are no password complexity requirements (length, special characters, etc.). This makes password extraction easier.
As a result, we gained access to a user’s smart home with all the settings and sensor information being available for any changes and manipulations. The IP address is also listed there.
It is also possible that there might be other personal sensitive information in the archive, given the fact that users often upload their phone numbers into the system to receive alerts and notifications.
Thus, the few steps involved with generating and sending the right requests to the server can provide remote attackers with the possibility of downloading data to access the user’s web interface account, which doesn’t have any additional security layers, such as 2FA (Two Factor Authentication). As a result, attackers can take control over someone’s home and turn off the lights or water, or, even worse, open the doors. So, one day, someone’s smart life could be turned into a complete nightmare.
Conclusion
The best solution for securing an IOT environment is by patching and fixing the vulnerabilities where it is required. And you can only fix if you know the best practices for mitigating these ATTACKS.
Our services of Vulnerability Assessment & Penetration Testing (VAPT) shall help you protect your critical business assets from external & internal cyber threats. Our in-house experienced security expert team will scan, identify, analyze vulnerabilities and provide remediation support as per industry best practices.
Contact us at: [email protected] for more information.



