KrOOK Vulnerability Let’s Attacker Decrypt Wifi Packets
A serious vulnerability in Wi-Fi chips has been discovered that affects billions of devices worldwide, according to researchers. It allows attackers to eavesdrop on Wi-Fi communications.
According to researcher at ESET, The bug (CVE-2019-15126) stems from the use of an all-zero encryption key in chips made by Broadcom and Cypress, which results in data decryption. This breaks the WPA2-Personal and WPA2-Enterprise security protocols.
The vulnerable chips are found in smartphones, tablets and laptops (using Broadcom silicon) and in IoT gadgets (Cypress chips), including several generations of products from Amazon (Echo, Kindle), Apple (iPhone, iPad, MacBook), Google (Nexus), Samsung (Galaxy), Raspberry (Pi 3), Xiaomi (RedMi). ESET also found the bug to be present in access points (APs) and routers by Asus and Huawei. In all, more than a billion devices are affected, researchers estimated.
What is Krook and How does it work ?
Kr00k is just a bug, like many other bugs that are being discovered on a daily basis in the software that we all use. The difference is that Kr00k impacts the encryption used to secure data packets sent over a WiFi connection.
- Typically, these packets are encrypted with a unique key that depends on the user’s WiFi password. However, this key gets reset to an all-zero value during a process called “disassociation.” Disassociation is something that occurs naturally in a WiFi connection. It refers to a temporary disconnection that usually happens due to a low WiFi signal.
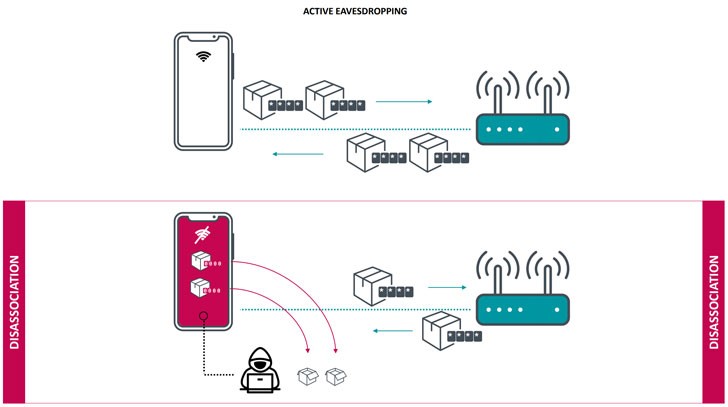
- WiFi devices enter into disassociated states many times a day, and they’re automatically configured to re-connect to the previously used network when this happens.This attack scenario allows hackers to actively intercept and decrypt WiFi packets, normally considered to be secure.
- Therefore, an attacker in near proximity to vulnerable devices can use this flaw to repeatedly trigger disassociations by sending de-authentication packets over the air to capture more data frames, “potentially containing sensitive data, including DNS, ARP, ICMP, HTTP, TCP, and TLS packets.”
This vulnerability doesn’t affect modern devices using WPA3 protocol, the latest Wi-Fi security standard.
The vulnerability does not reside in the Wi-Fi encryption protocol; instead, it exists in the way vulnerable chips implemented the encryption.
It doesn’t let attackers know your Wi-Fi password, and also changing it wouldn’t help you patch the issue.
What should you do?
– Wi-Fi users should immediately update their Wi-Fi-enabled devices as soon as a software update is made available. Wi-Fi-enabled devices are anything that connects to the Internet — from laptops, tablets, and smartphones to other smart devices such as wearables and home appliances.
– Users can check if they received Kr00k patches by checking their device OS/firmware changelogs for fixes against CVE-2019-15126, which is the unique ID assigned to track this bug.
– Apple has already released patches for its users, some should have issued advisory or security patches at the time of publication, and other vendors are still testing the issue against their devices.



