VNC Vulnerability affecting four most popular open source application
What is a VNC?
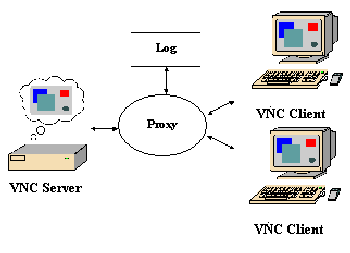
A virtual network (VNC) is a desktop sharing application that relies on a remote frame buffer protocol to remotely control another computer. While sharing the desktop through VNC, it transmits keyboard and mouse events from one system to another over the network based on-screen updates. It is platform independent desktop sharing application. VNC consists of client server and communication protocol.
VNC server is the program used to share the screen allowing client to take the control. VNC client is used for watching, controlling, and interacting with the server. Server is generally controlled by the client.
VNC protocol makes use of remote frame buffer protocol and sends the graphic passed from the server to the client and commands passed by the client to the server.
VNC Vulnerability
Four of the widely used open source VNC were tested by Kaspersky namely:
- LibVNC
- UltraVNC
- TightVNC1.x
- TurboVNC
The results of testing showed that 37 new vulnerabilities (memory corruption vulnerability) were found. Out of which only 1 was found in TurboVNC followed by TightVNC with 4 vulnerabilities, 10 vulnerabilities were found in LibVNC and 22 were found in UltraVNC. The bug is due to incorrect memory usage which causes application to malfunction and denial of service is also possible, in more dangerous cases attackers gain unauthorized access to information and even can execute a malware into victim’s system. The client application is more vulnerable as it receives more data and data decoding is done and if there are errors in programming the attacker can gain access. Some exploitable server-side bugs, including a stack buffer overflow flaw in the TurboVNC server that makes it possible to achieve remote code execution on the server.
Recommendations
Kaspersky has now reported the issues to the concerned application developers and patches have been released for three products as the fourth TightVNC version 1 is no longer available. Also, special care has to be taken to not use untrusted and untested VNC servers as most vulnerabilities are present in these servers only. Also, VNC servers should be protected with strong and complex passwords.
The users using the above three open source VNC software should update the applications for latest security patches and TightVNC version users should upgrade to TightVNC version 2 which has been released.



