Zero Trust Model
Zero trust is an approach which is based on the principle of “never trust, always verify”. It is designed to protect the current digital environment from successful data breaches by eliminating the traditional principle of “Trust” in organization’s network. It provides protection at the application level by implementing network segmentation and hence, preventing lateral movement.
A defined perimeter security (secure area) approach is not effective in today’s digital age. This is because:
- Many data breaches happened because hackers, once they got past the corporate firewalls, were able to move through internal systems without much resistance/restrictions.
- The perimeter itself is no longer clearly defined, because applications and data stores are on-premises and in the cloud, with users accessing them from multiple devices and locations.
Zero Trust model consists of the following approach:
- Identify “protect surface”:
Protect surface is the network’s most critical and valuable data, assets, applications and services. These need to be identified as they vary from organization to organization. Protect surface only contains organization’s most sensitive and critical information, and hence the protect surface is orders of magnitude smaller than the attack surface, and it is always knowable.
- Create Microperimeter around protect surface:
Once you determine the protect surface, create a microperimeter around it. This microperimeter moves with the protect surface, wherever it goes. You can create a microperimeter by deploying a segmentation gateway, more commonly known as a next-generation firewall, to ensure only known, allowed traffic or legitimate applications have access to the protect surface.
Implement network segregation by:
- Use the principles of least privilege and need‐to‐know. If a host, service or network doesn’t need to communicate with another host, service or network, it should not be allowed to.
- Apply technologies at more than just the network layer. Each host and network should be segmented and segregated, where possible, at the lowest level that can be practically managed.
- Separate hosts and networks based on their sensitivity or criticality to business operations. This may include using different hardware or platforms depending on different security classifications, security domains or availability/integrity requirements for certain hosts or networks.
- Identify, authenticate and authorise access by all entities to all other entities.
- Implement whitelisting of network traffic instead of blacklisting.
- Giving Access to right users:
Micro-segmentation and small perimeter to be enforced based on users, their locations and other data to determine whether to trust a user, machine or application seeking access to a particular part of the enterprise.
Access and authorization to be provide on the basis of policy on who, what, when, where, why and how. The policy created to ensure authorize access determines who can transit the microperimeter at any point in time, preventing access to your protect surface by unauthorized users and preventing the exfiltration of sensitive data.
- Monitor and Maintain:
After implementing the protect surface network segregation and implementing small secure perimeters, continue to monitor and maintain in real time, looking for things like what should be included in the protect surface, interdependencies not yet accounted for, and ways to improve policy.
Working of Zero Trust Model
A zero trust network is built upon five fundamental assertions:
- The network is always assumed to be hostile.
- External and internal threats exist on the network at all times.
- Network locality is not sufficient for deciding trust in a network.
- Every device, user, and network flow is authenticated and authorized.
- Policies must be dynamic and calculated from as many sources of data as possible.
Traditional network security architecture breaks different networks (or pieces of a single network) into zones, contained by one or more firewalls. Each zone is granted some level of trust, which determines the network resources it is permitted to reach. This model provides very strong defense-in-depth. For example, resources deemed more risky, such as web servers that face the public internet, are placed in an exclusion zone (often termed a “DMZ”), where traffic can be tightly monitored and controlled. Such an approach gives rise to an architecture that is similar to some you might have seen before, such as the one shown in Figure 1.
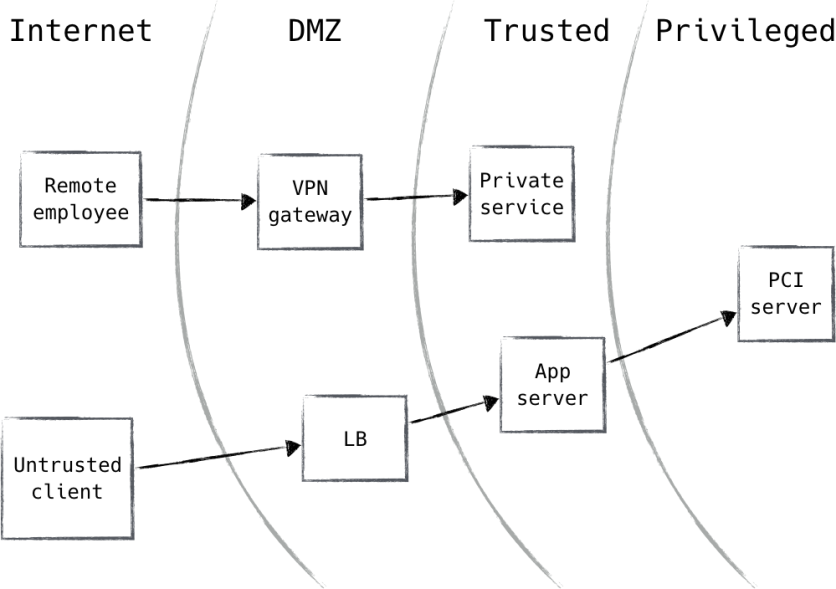
Figure 1 Traditional network security architecture
By leveraging distributed policy enforcement and applying zero trust principles the architecture can be deign as mentioned in Figure 2. The supporting system is known as the control plane, while most everything else is referred to as the data plane, which the control plane coordinates and configures. Requests for access to protected resources are first made through the control plane, where both the device and user must be authenticated and authorized. Fine-grained policy can be applied at this layer, perhaps based on role in the organization, time of day, or type of device. Access to more secure resources can additionally mandate stronger authentication.
Once the control plane has decided that the request will be allowed, it dynamically configures the data plane to accept traffic from that client (and that client only). In addition, it can coordinate the details of an encrypted tunnel between the requestor and the resource. This can include temporary one-time-use credentials, keys, and ephemeral port numbers.
While some compromises can be made on the strength of these measures, the basic idea is that an authoritative source, or trusted third party, is granted the ability to authenticate, authorize, and coordinate access in real-time, based on a variety of inputs.
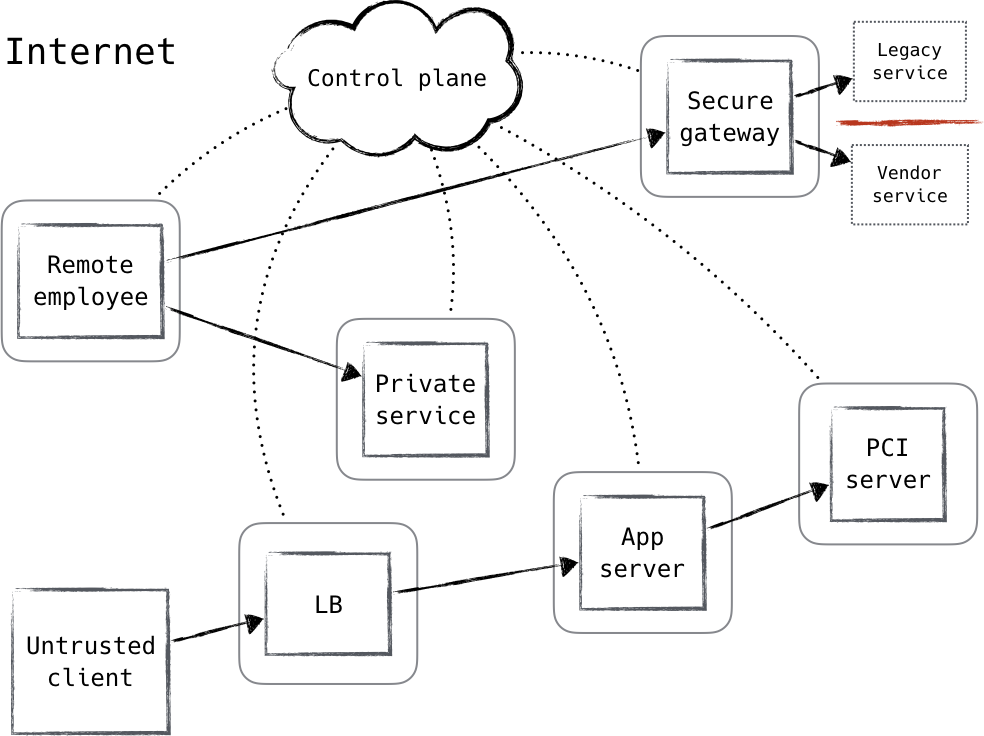
Figure 2 Zero Trust Architecture
Technologies for Implementing Zero Trust
Zero Trust draws on technologies such as:
- multifactor authentication
- IAM, orchestration
- analytics
- encryption
- scoring
- file system permissions
- Least privilege rights or least amount of access given which is required to accomplish a specific task.
Push Notification Authentication enables user authentication by sending a push notification directly to a secure application on the user’s device, alerting them that an authentication attempt is taking place. Users can view authentication details and approve or deny access, typically via a simple press of a button.
Notifications can be sent in-band or out-of-band, using any number of communications channels.
Push notifications authenticate the user by confirming that the device registered with the authentication system – typically a mobile device – is in fact in the user’s possession. If the device is compromised by an attacker, then push notifications are compromised.
Zero Trust Solutions
There are various solutions available in the market for various enterprises dependent upon size SME/LARGE, or also based on on-premise deployment or on cloud.
Types of solutions available in the market are:
- Network Security
- Data Security
- Endpoint Security
- Zero Trust Security
- API Security
- Security Analytics
- Security Policy Management
Key market players profiled in this report include Cisco Systems Inc. (US), Akamai Technologies, Inc. (US), Palo Alto Networks, Inc. (US), Symantec Corporation (US), Okta, Inc. (US), Forcepoint, LLC (US), Centrify Corporation (US), Cyxtera Technologies (US), Illumio (US), Sophos Group Plc (UK), Google LLC (US), Microsoft, Inc. (US), VMware Inc. (US), Trend Micro Incorporated (Japan), Cloudflare (US), IBM Corporation (US), Fortinet (US), Check Point Software Technologies Ltd. (US), Pulse Secure, LLC (US), and ON2IT (Netherlands). These players offer Zero Trust Security solutions to cater to the demands and needs of the market. The major growth strategies adopted by these players include partnerships, collaborations & agreements, and new product launches/product enhancements.
Why Zero Trust can be a Solution?
Over the years, networks and networking grew significantly and became more complicated. A “network” was not necessarily an on-site, hardware-based entity, and users were not necessarily sitting in a central office that could be defined by geography. Laptops then smartphones and tablets meant that employees could work from anywhere in the world. Companies began using cloud and virtual for the speed, efficiency, and cost savings they offered. Geographic location of the person or system became irrelevant.
Zero trust implementation is not location dependent, but instead id interdepend on user, device, application and service. The segregated network moves with the protected surface.
Zero trust can be applied to users, devices, hosts, and applications. What this does is ensure that malicious users or software—if they manage to get onto the network through phishing or system vulnerability—can’t continue a cyber-attack progression.



