Coronavirus Used in Spam, Malware, and Malicious Domains
If there’s one thing certain during a pandemic, it’s that hackers will use it for their own gain.
Don’t be too surprised. Every time there’s a major news story, a world event or even regular national events like tax preparation season, hackers jump at the chance to take advantage of the uptick in chatter to launch attacks against unsuspecting victims.
As it turns out, the COVID-19 pandemic isn’t any different. Several cybersecurity firms are reporting an uptick in attacks against a range of targets, all using the ongoing COVID-19 pandemic as a hook to hoodwink their victims into running malware. It comes as large portions of the globe are on lockdown amid the outbreak of the coronavirus strain.
FireEye said it has seen an uptick in targeted spearphishing campaigns from hackers in China, North Korea and Russia, to deliver malware.
But researchers say that attackers aren’t just using the coronavirus as a cover for spreading malware.
Email security firm Agari told TechCrunch that it has evidence of what appears to be the first case of a coronavirus-themed business email compromise attack, designed to trick businesses into turning over money.
New threat with an Old Malware Component
The latest threat, designed to steal information from unwitting victims, was first spotted by MalwareHunterTeam last week and has now been analyzed by Shai Alfasi, a cybersecurity researcher at Reason Labs.
It involves a malware identified as AZORult, an information-stealing malicious software discovered in 2016. AZORult malware collects information stored in web browsers, particularly cookies, browsing histories, user IDs, passwords, and even cryptocurrency keys. With these data drawn from browsers, it is possible for cybercriminals to steal credit card numbers, login credentials, and various other sensitive information.
AZORult is reportedly discussed in Russian underground forums as a tool for gathering sensitive data from computers. It comes with a variant that is capable of generating a hidden administrator account in infected computers to enable connections via the remote desktop protocol (RDP).
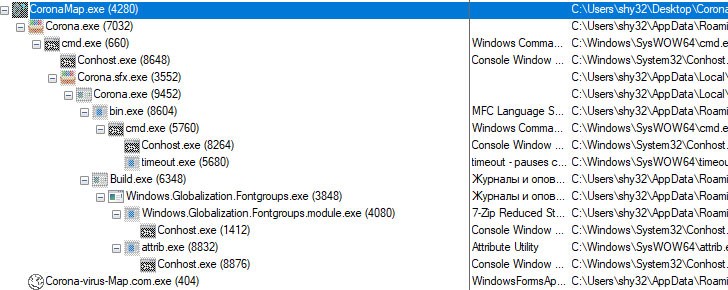
How to Identify the Malware
Executing the Corona-virus-Map.com.exe results in the creation of duplicates of the Corona-virus-Map.com.exe file and multiple Corona.exe, Bin.exe, Build.exe, and Windows.Globalization.Fontgroups.exe files
Detection and Prevention
- The key to removing and stopping the opportunistic “coronavirus map” malware is to have the right malware protection system. It will be challenging to detect it manually, let alone remove the infection without the right software tool.
- Alfasi suggests Reason Antivirus software as the solution to fix infected devices and prevent further attacks. He is affiliated with Reason Security, after all. Reason is the first to find and scrutinize this new threat, so they can handle it effectively.
- Trend Micro endpoint solutions such as the Smart Protection Suites and Worry-Free™ Business Security detects and block the malware and the malicious domains it connects to.
Multilayered protection is also recommended for protecting all fronts and preventing users from accessing malicious domains that could deliver malware.



