Fundamentals of ISO 27001 Standard
ISO 27001 is an international standard published by the International Standardization Organization (ISO), and it describes how to manage information security in a company. The latest revision of this standard was published in 2013, and its full title is now ISO/IEC 27001:2013. The first revision of the standard was published in 2005, and it was developed based on the British standard BS 7799-2.
ISO 27001 can be implemented in any kind of organization, profit or non-profit, private or state-owned, small or large. It provides methodology for the implementation of information security management in an organization. It also enables companies to become certified, which means that an independent certification body has confirmed that an organization has implemented information security compliant with ISO 27001.
How does ISO 27001 work?
The primary focus of ISO 27001 is to protect the confidentiality, integrity and availability of the information in a company. This is done by finding out what potential problems could happen to the information (i.e., risk assessment), and then defining what needs to be done to prevent such problems from happening (i.e., risk mitigation or risk treatment). Therefore, the main philosophy of ISO 27001 is based on managing risks: find out where the risks are, and then systematically treat them.
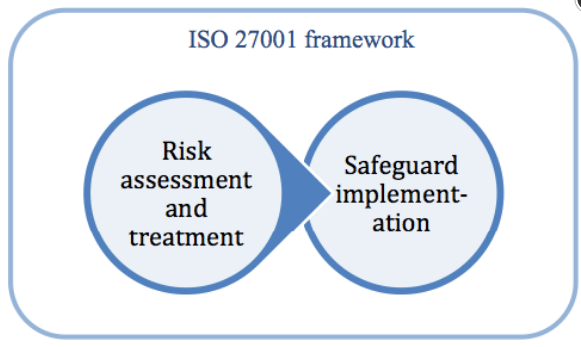
The safeguards (or controls) that are to be implemented are usually in the form of policies, procedures and technical implementation (e.g., software and equipment). However, in most cases companies already have all the hardware and software in place, but they are using them in an unsecure way – therefore, the majority of the ISO 27001 implementation will be about setting the organizational rules (i.e., writing documents) that are needed in order to prevent security breaches. Since such implementation will require multiple policies, procedures, people, assets, etc. to be managed, ISO 27001 has described how to fit all these elements together in the information security management system (ISMS).
So, managing information security is not only about IT security (i.e., firewalls, anti-virus, etc.) – it is also about managing processes, legal protection, managing human resources, physical protection, etc.
Why is ISO 27001 good for your company?
There are 4 essential business benefits that a company can achieve with the implementation of this information security standard:
- Comply with legal requirements – there are more and more laws, regulations and contractual necessities related to information security, and the good news is that most of them can be resolved by implementing ISO 27001 – this standard gives you the flawless methodology to comply with them all.
- Attain marketing advantage – if your company gets certified and your competitors do not, you may have a lead over them in the eyes of the customers who are sensitive about keeping their information safe.
- Lower costs – the main philosophy of ISO 27001 is to prevent security incidents from happening – and every incident, large or small, costs money. Therefore, by preventing them, your company will save quite a lot of money. And the best thing of all – investment in ISO 27001 is far smaller than the cost savings you’ll achieve.
- Improved organization – naturally, fast-growing companies don’t have the time to stop and define their processes and procedures – as a consequence, very often the employees do not know what needs to be done, when, and by whom. Implementation of ISO 27001 helps resolution of such situations, because it inspires companies to write down their main processes (even those that are not security-related), allowing them to reduce the lost time of their employees.
Where does information security management fit in a company?
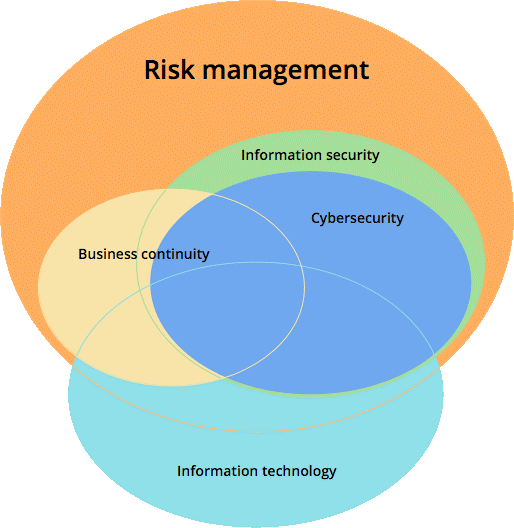
Fundamentally, information security is part of overall risk management in a company, with areas that overlap with cybersecurity, business continuity management and IT management:
What does ISO 27001 actually look like?
ISO/IEC 27001 is split into 11 sections, plus Annex A. Sections 0 to 3 are introductory (and are not mandatory for implementation), while sections 4 to 10 are mandatory – meaning that all their requirements must be implemented in an organization if it wants to be compliant with the standard. Controls from Annex A must be implemented only if declared as applicable in the Statement of Applicability.
- Section 0: Introduction – explains the purpose of ISO 27001 and its compatibility with other management standards.
- Section 1: Scope – explains that this standard is applicable to any type of organization.
- Section 2: Normative references – refers to ISO/IEC 27000 as a standard where terms and definitions are given.
- Section 3: Terms and definitions – again, refers to ISO/IEC 27000.
- Section 4: Context of the organization – this section is part of the Plan phase in the PDCA cycle and defines requirements for understanding external and internal issues, interested parties and their requirements, and defining the ISMS scope.
- Section 5: Leadership – this section is part of the Plan phase in the PDCA cycle and defines top management responsibilities, setting the roles and responsibilities, and contents of the top-level Information security policy.
- Section 6: Planning – this section is part of the Plan phase in the PDCA cycle and defines requirements for risk assessment, risk treatment, Statement of Applicability, risk treatment plan, and setting the information security objectives.
- Section 7: Support – this section is part of the Plan phase in the PDCA cycle and defines requirements for availability of resources, competences, awareness, communication, and control of documents and records.
- Section 8: Operation – this section is part of the Do phase in the PDCA cycle and defines the implementation of risk assessment and treatment, as well as controls and other processes needed to achieve information security objectives.
- Section 9: Performance evaluation – this section is part of the Check phase in the PDCA cycle and defines requirements for monitoring, measurement, analysis, evaluation, internal audit and management review.
- Section 10: Improvement – this section is part of the Act phase in the PDCA cycle and defines requirements for nonconformities, corrections, corrective actions and continual improvement.
- Annex A – this annex provides a catalogue of 114 controls (safeguards) placed in 14 sections (sections A.5 to A.18).
Related information security and other standards
- ISO/IEC 27002 provides guidelines for the implementation of controls listed in ISO 27001. ISO 27001 specifies 114 controls that can be used to reduce security risks, and ISO 27002 can be quite useful because it provides details on how to implement these controls. ISO 27002 was previously referred to as ISO/IEC 17799, and emerged from the British standard BS 7799-1.
- ISO/IEC 27004 provides guidelines for the measurement of information security – it fits well with ISO 27001 because it explains how to determine whether the ISMS has achieved its objectives.
- ISO/IEC 27005 provides guidelines for information security risk management. It is a very good supplement to ISO 27001 because it gives details on how to perform risk assessment and risk treatment, probably the most difficult stage in the implementation. ISO 27005 emerged from the British standard BS 7799-3.
- ISO 22301 defines the requirements for business continuity management systems – it fits very well with ISO 27001 because A.17 of ISO 27001 requires business continuity to be implemented; however, it doesn’t provide too many details.
- ISO 9001 defines the requirements for quality management systems – although at first glance, quality management and information security management do not have much in common, the fact is that about 25% of the ISO 27001 and ISO 9001 requirements are the same: document control, internal audit, management review, corrective actions, setting the objectives, and managing competences. This means if a company has implemented ISO 9001, it will have a much easier job implementing ISO 27001.



