Phishing messages: Target Steal GitHub Credential
A Sawfish phishing campaign is recently designed by GitHub SIRT to steal GitHub login credentials and time-based one-time password (TOTP) codes.
The attack comes through a Github message that claims the target’s account has experienced unauthorized activity. A handy link to rectify the situation is included where the alterations can be viewed. The link, redirects to a phishing website that mimics the GitHub login page. Here the victim’s credentials are harvested.
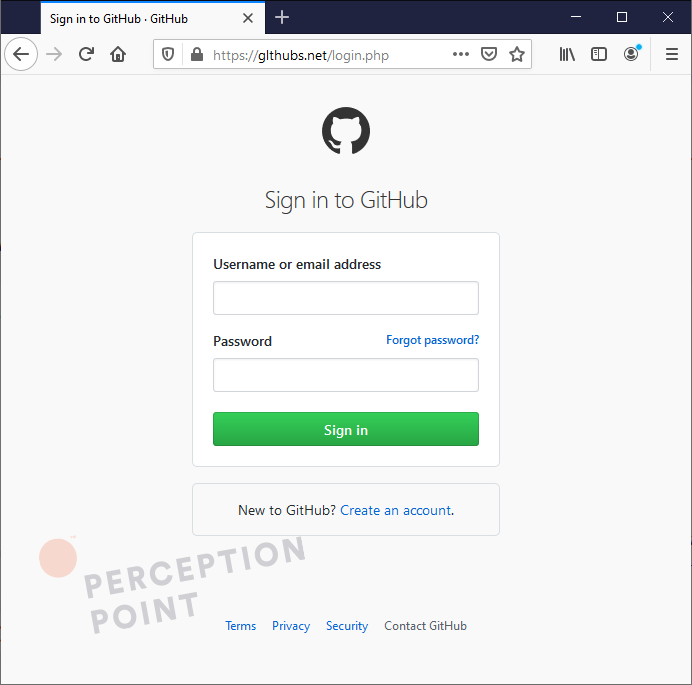
For those using TOTP two-factor authentication the malicious site takes and sends the codes in real-time to the attacker allowing the GitHub account to be instantly accessed. This access is also used to grab and download repositories’ contents.
According to GitHub SIRT, this access is used to grab and download repositories contents.
The Accounts that are protected by hardware security keys are not vulnerable to this attack.
GitHub SIRT listed six TTPs (tactics, techniques and Procedures) being used by the threat actors behind the campaign:
- The phishing email is sourced from authorized domains, using compromised email servers or stolen API credentials for legitimate bulk email providers.
- Use of URL-shortening services to conceal the true destination of the malicious link.
- Use of PHP-based redirectors on compromised websites to redirect the victimfrom a less suspicious-looking URL to another malicious one.
- The attacker immediately downloads private repository contents accessible to the compromised user.
- If an attacker successfully steals account credentials, they may quickly create GitHub personal access tokens or authorize OAuth applications on the account in order to protect access in the event that the user changes their password.
- Targets currently-active GitHub users across many companies in the tech sector.
Recommendations:
It is recommended that:
- Switch from TOTP two-factor authentication to a hardware key or WebAuthn two-factor authentication.
- If any user believes they have clicked on a fraudulent message they should immediately reset their login credentials.



