Microsoft Teams Fixes GIFs Cyber-Attack Flaw
Overview
Vulnerability occurred in Microsoft that allows attackers to initiate the attack via using GIF in their chats. The attack simply involved tricking a victim into viewing a malicious GIF image for it to work, according to researchers at CyberArk who also created a proof-of-concept (PoC) of the attack.
Even if an attacker doesn’t gather much information from a compromised Teams’ account, they could use the account to traverse throughout an organization, CyberArk cyber security researcher.
Eventually, the attacker could access all the data from your organization Teams accounts – gathering confidential information, competitive data, secrets, passwords, private information, business plans, etc.
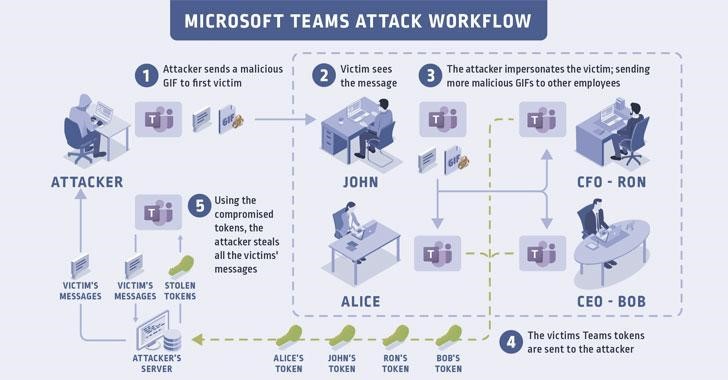
How Attack Happened
- Attacker steals “authtoken” & “skype token”
The attack involves malicious actors being able to abuse a JSON Web Token (“authtoken”) and a second “skype token”. The combination of these two tokens are used by Microsoft to allow a Teams user to see images shared with them – or by them – across different Microsoft servers and services such as SharePoint and Outlook.
The weakness is in the application programming interfaces (APIs) used to facilitate the communication between services and servers, Tsarfati said. Microsoft validates the cookie called “authtoken” and “skype token” via *.teams.microsoft.com.
The “authtoken” and “skypetoken_asm” cookie is sent to teams.microsoft.com – or any subdomain under teams.microsoft.com to authenticate GIF sender and receiver, Tsarfati wrote.
There were two insecure Microsoft subdomains which were used by the attacker for this attack “aadsync-test.teams.microsoft.com” and “data-dev.teams.microsoft.com” ripe for takeover.
“If an attacker can somehow force a user to visit the sub-domains that have been taken over, the victim’s browser will send this cookie to the attacker’s server, and the attacker (after receiving the authtoken) can create a Skype token. After doing all of this, the attacker can steal the victim’s Teams account data,” the research said.
- After accessing both “auth” and “skype” token
Now with both tokens, the access token (authtoken) and the Skype token, an attacker will be able to make APIs calls/actions through Teams API interfaces – letting you send messages, read messages, create groups, add new users or remove users from groups, change permissions in groups,” researchers wrote.
This attack takes only the target to view a malicious GIF sent by the rogue team user.
“The reason that Teams sets the ‘authtoken’ cookie is to authenticate the user for loading images in domains across Teams and Skype,” explained the researcher.
“When the victim opens this message, the victim’s browser will try to load the image and will send the authtoken cookie to the compromised sub-domain.”
This allows the attacker to get their hands on the victim’s “authtoken” and ultimately provides a pathway to access the victim’s Microsoft Teams data.
Every account that could have been impacted by this vulnerability could also have been a spreading point to all other company accounts. The vulnerability can also be sent to groups (a.k.a Teams), which makes it even easier for an attacker to get control over users faster and with fewer steps.
Flaw Rectified
Researchers said they worked with Microsoft Security Research Center after finding the account takeover vulnerability on March 23. They said Microsoft quickly deleted the misconfigured DNS records of the two subdomains, which mitigated the problem.
Microsoft neutralized the threat, updating misconfigured DNS records.
As the attack was initiated by sending a GIF to a Microsoft team member and it represents a phishing attack.
Recommendations for Phishing
It is recommended to adopt the following best practices against:
- Do not follow URL links from untrusted sources or emails such as spam emails to avoid being redirected to malicious websites by malicious links looking seemingly legitimate.
- Open email attachment with extreme care. Always check the attachment’s extension. Never open attachment with “pif”, “exe”, “bat”, “.vbs” extension.
- Always be wary when giving off sensitive personal or account information.
- Always ensure that your computer is applied with the latest security patches and anti-malware software with an updated definition file to reduce the chance of being affected by fraudulent emails or websites riding on software vulnerabilities.



