Android Malware Steals Banking Passwords, Private Data and Keystrokes
A new mobile banking malware has been discovered that can steal banking information, personal data and implant keystrokes on victims’ Android devices.
The Malware named “EventBot” primarily abusing the Android’s Accessibility feature and steal the financial apps data, SMS messages and read the incoming SMS to bypass the 2FA.
It has different version (0.0.0.1, 0.0.0.2, and 0.3.0.1 and 0.4.0.1) and the each version has different bots functionality.
It is capable of targeting over 200 different financial apps, including banking, money transfer services, and crypto-currency wallets such as Paypal Business, Revolut, Barclays, CapitalOne, HSBC, Santander, TransferWise, and Coinbase.
The malware has real potential to become the next big mobile malware, as it is under constant iterative improvements, abuses a critical operating system feature, and targets financial applications.
EventBot Infection Process
In the initial stage, Attackers masquerade the malware as a legitimate application with several Icons and uploaded into the rogue APK stores and other shady websites.

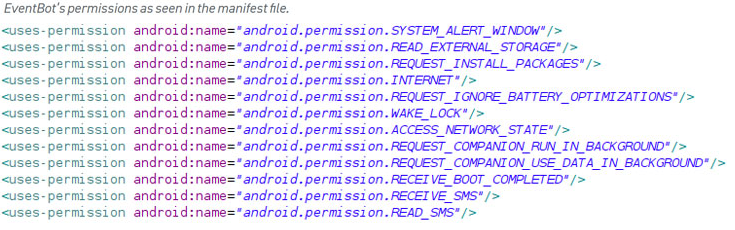
Once the malicious module got installed, it requests a following permission in the victim’s devices.
Later it prompts users to grant permission to the accessibility services. Once it gained the access, the malware has gained an ability to operate as a keylogger and access the notification about the other installed apps.
Data Gathering List
- Getting a list of all installed applications: Once EventBot is installed on the target machine, it lists all the applications on the target machine and sends them to the C2.
- Device information:EventBot queries for device information like OS, model, etc, and also sends that to the C2.
- Data encryption: In the initial version of EventBot, the data being exfiltrated is encrypted using Base64 and RC4.
- SMS grabbing:EventBot has the ability to parse SMS messages by using the targeted device’s SDK version to parse them correctly.
Recommendations:
It is recommended to follow the below best practices:
- Keep your mobile device up-to-date with the latest software updates from legitimate sources.
- Keep Google Play Protect on and use mobile threat detection solutions for enhanced security.
- Do not download mobile apps from unofficial or unauthorized sources.
- When in doubt, check the APK signature and hash in sources like VirusTotalbefore installing it on your device.



