Thunderbolt Flaws Expose Millions of PCs to Hands-On Hacking
A cybersecurity researcher recently uncovered 7 new unpatchable hardware vulnerabilities that affect all desktops and laptops sold in the past 9 years with Thunderbolt, or Thunderbolt-compatible USB-C ports.
The new attack method called Thunderspy. It takes less than five minutes to pull off with physical access to a device, and affects any PC.
On Thunderbolt-enabled Windows or Linux PCs manufactured before 2019, the technique can bypass the login screen of a sleeping or locked computer and even its hard disk encryption to gain full access to the computer’s data. And while this attack in many cases requires opening a target laptop’s case with a screwdriver, it leaves no trace of intrusion and can be pulled off in just a few minutes.
The vulnerabilities can be exploited in 9 realistic evil-maid attack scenarios, primarily to steal data or read/write all of the system memory of a locked or sleeping computer, even when drives are protected with full disk encryption.
Good news, the flaw is not linked to the network activity, and thus can’t be exploited remotely.
Thunderspy works even if you follow best security practices by locking or suspending your computer when leaving briefly. If system administrator has set up the device with Secure Boot, strong BIOS and OS account passwords, and enabled full disk encryption, still Thunderspy works.
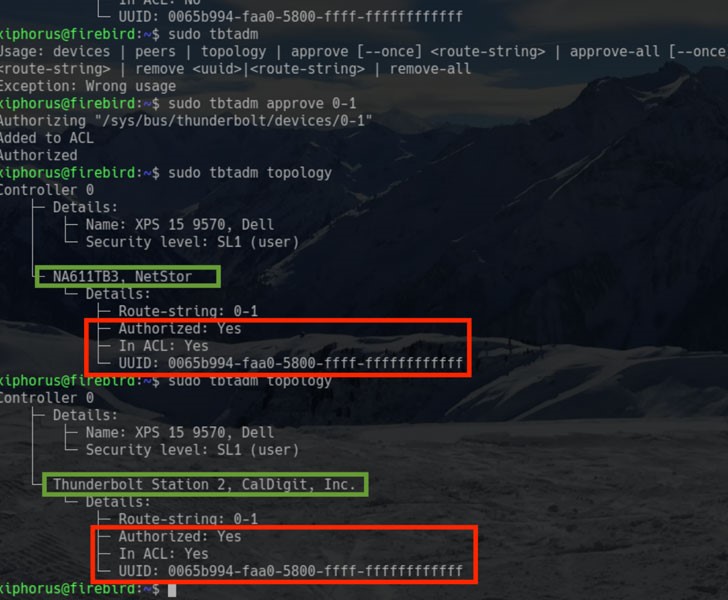
ThunderSpy Vulnerabilities
Thunderspy vulnerabilities affects Thunderbolt version 1, 2 and 3, and can be exploited to create arbitrary device identities, clone user-authorized Thunderbolt devices, and finally, obtain PCIe connectivity to perform DMA attacks.
- Inadequate firmware verification schemes
- Weak device authentication scheme
- Use of unauthenticated device metadata
- Downgrade attack using backward compatibility
- Use of unauthenticated controller configurations
- SPI flash interface deficiencies
- No Thunderbolt security on Boot Camp
By combining the first three flaws, an attacker can break the ‘security levels’ feature, and load an unauthorized malicious Thunderbolt device by forging Thunderbolt device identities.
Thunderbolt controllers store device metadata in a firmware section referred to as Device ROM, which is not cryptographically verified. From the first issue, this vulnerability enables constructing forged Thunderbolt device identities.
In addition, when combined with the second issue, forged identities may partially or fully comprise arbitrary data.
DMA based attacks let attackers compromise targeted computers just by plugging a malicious hot-plug devices such as an external network card, mouse, keyboard, printer, or storage into Thunderbolt port or the latest USB-C port.
DMA attacks are possible because Thunderbolt port works at a very low-level and with high privileged access to the computer, allowing connected peripherals to bypass operating system security policies and directly read/write system memory.
Recommendation:
- To prevent DMA attacks, Intel introduced some countermeasures. One is ‘security levels’ that prevents devices from connecting without user authorization and other is ‘cryptographic authentication of connections’ that prevent devices from spoofing user-authorized devices.
- If system is affectedby Thunderspy vulnerabilities, a free and open-source tool, called Spycheck has also been released.
- Always avoid leaving your devices unattended or power off the system completely, or at least consider using hibernation instead of sleep mode.
- Avoid leaving your Thunderbolt peripherals unattended or lending them to anybody.
- According to Ruytenberg, some latest systems available in market since 2019 include Kernel DMA protection that partially mitigates Thunderspy vulnerabilities.



