New malware tool can steal files from airgapped PCs using USBs
The newly revealed USBCulprit malware is used by a group known as Cycldek, Conimes, or Goblin Panda and is designed for compromising air-gapped devices via USB.
Cycldek is a Chinese APT group targeting Southeast Asian nations for a long time to steal government information and state secrets.
Kaspersky revealed this week a custom-designed stealthy tool called ‘USBCulprit‘, the malware aims at extracting data with the help of USB drive from air-gapped computers and currently targeting users in 3 countries, namely Vietnam, Thailand, and Laos.
It enters the system via RTF (Rich Text Format) documents or other unknown means, performs an extensive scanning of the victim’s system, and begins to scan documents, passing them and replicating itself onto removable media.
“This tool, which we saw downloaded by RedCore implants in several instances, is capable of scanning various paths in victim machines, collecting documents with particular extensions and passing them on to USB drives when they are connected to the system. It can also selectively copy itself to a removable drive in the presence of a particular file, suggesting it can be spread laterally by having designated drives infected and the executable in them opened manually,” Kaspersky explains.
RedCore and BlueCore are terms used by Kaspersky to describe the two different styles (variants) of malware deployed by the group. Initial Infection Vector for BlueCore has been listed as “RTF documents,” whereas that for RedCore is still unknown.
Kaspersky’s report shows a comprehensive diagram of how the two variants RedCore and BlueCore actuate and share information, in the form of a well-coordinated “cluster.”
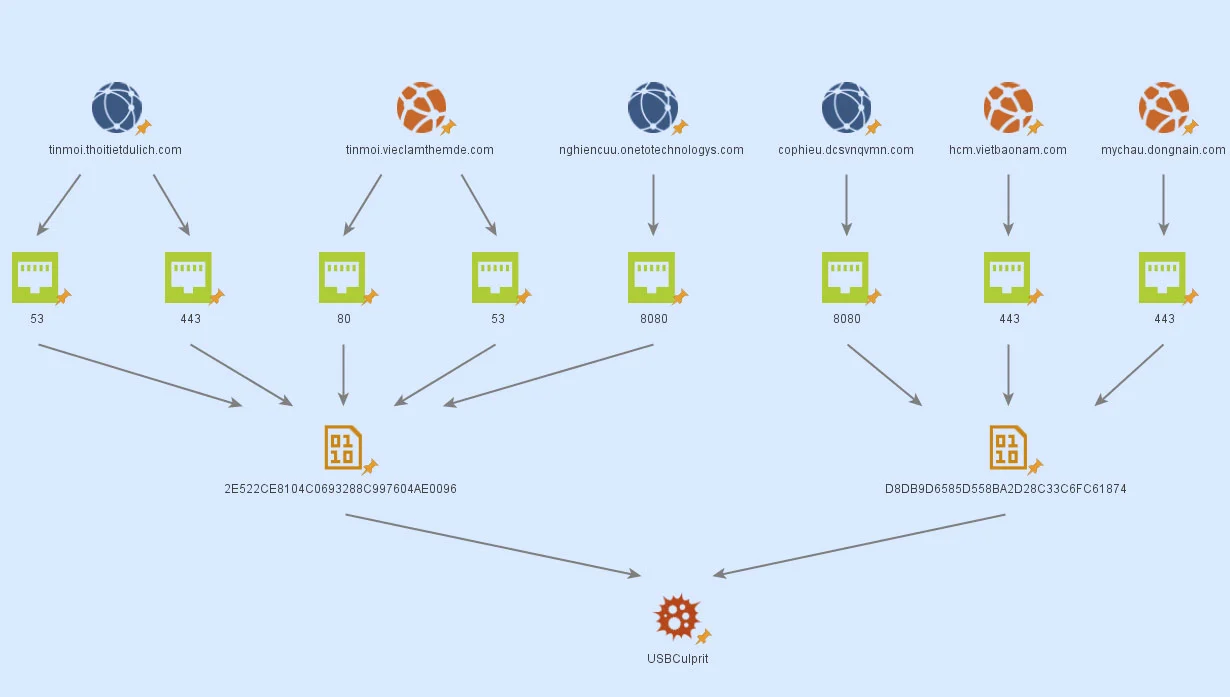
Both of these variants have been attributed to the Cycldek threat actor group.
The security firm states that the most recently observed samples seem to be from 2019 and also feature functionality that allows it to execute certain files with “a specific name” from the connected USB.
How does it work?
It works by searching the victim’s computer looking out for specific file extensions that are of interest to it (pdf;*.doc;*.wps;*docx;*ppt;*.xls;*.xlsx;*.pptx;*.rtf.). Once found, it transfers these to a connected USB drive.
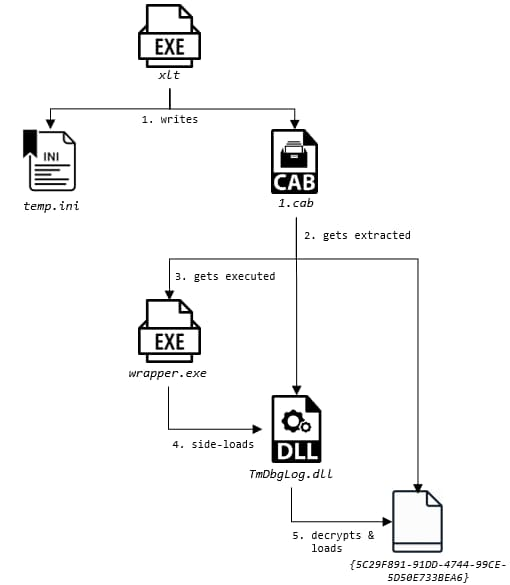
Recommendations
It is recommended to consider the following best practices:
- Keep your software up to date and make sure all recent patches are installed.
- Use Anti-Virus softwares and keep backup of your data.
- Prohibition of any electronic devices (USB, Phones etc.) in the computer areas.
- Make sure your Web browser’s security settings are high enough to detect unauthorized downloads.
- Don’t leave your data unencrypted.
- Plug unused USB slots with the USB Port Blocker.
- Turn the machine off when it is not in use (and unplug it from power) and replace standard drives with SSD.



