U.S. Police and Fusion Centers Data Leaked
296 GB of data has been stolen from US law enforcement agencies and fusion centers by a group of Hackers. The files, dubbed BlueLeaks, have been published by Distributed Denial of Secrets (DDoSecrets), a group that describes itself as a “transparency collective.” The data has been made available online on a searchable portal.
DDoSecrets, or Distributed Denial of Secrets, is a transparency collective similar to WikiLeaks, which publicly publishes data and classified information submitted by leakers and hackers while claiming the organization itself never gets involved in the exfiltration of data.
According to the hacktivist group, BlueLeaks dump includes “police and FBI reports, bulletins, guides and more,” which “provides unique insights into law enforcement and a wide array of government activities, including thousands of documents mentioning COVID19.
A quick analysis of the BlueLeaks dump shows the leaked data contains 200+ US Police Department data with more than one million files, such as scanned documents, videos, emails, audio files, and more.
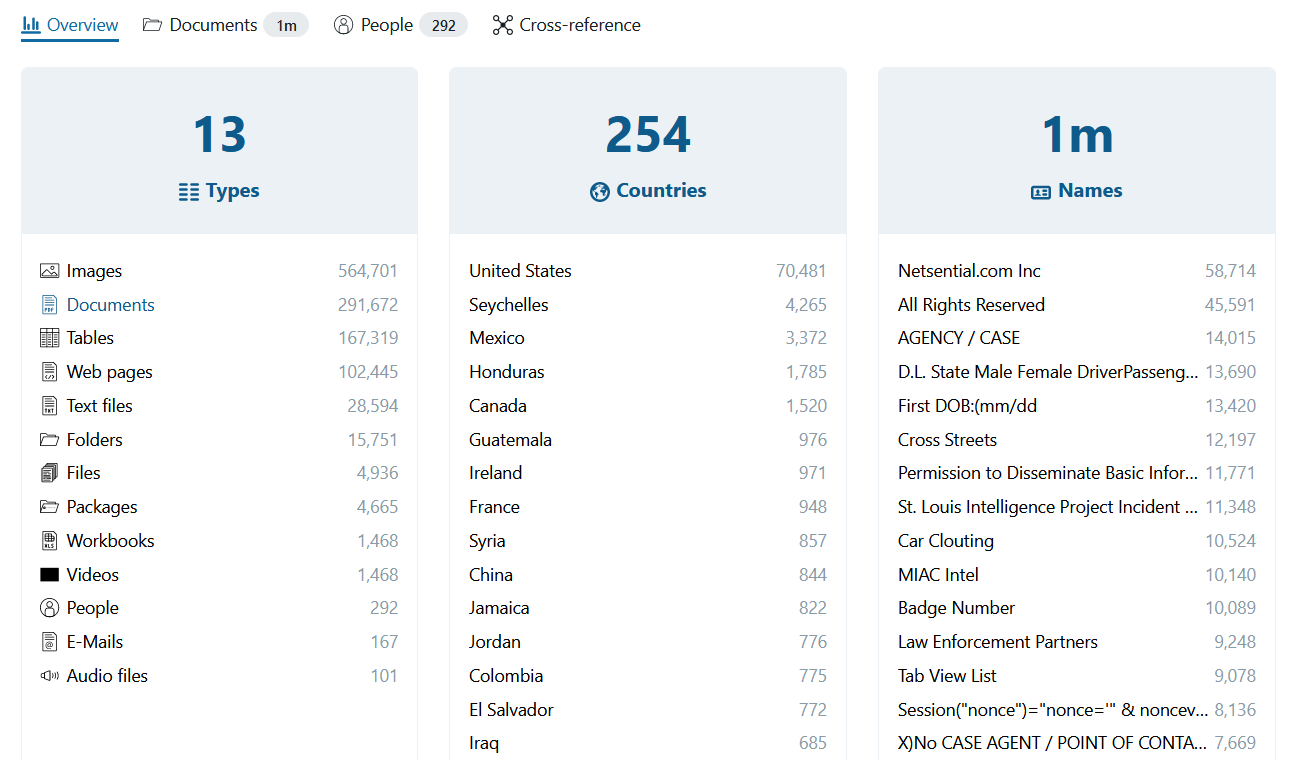
Some of the U.S. agencies listed in BlueLeaks are:
- Alabama Fusion Center
- Austin Regional Intelligence Center
- Boston Regional Intelligence Center
- Colorado Information Analysis Center
- California Narcotic Officers’ Association
- Delaware Information and Analysis Center
- FBI Houston Citizens Academy Alumni Association
- FBI National Academy Association Arkansas/Missouri Chapter
- FBI National Academy Association Michigan Chapter
- FBI National Academy Association of Texas
This massive data stems from a security breach at Houston-based web hosting company ‘Netsential Inc,’ where the webserver for National Fusion Center Association (NFCA) is hosted. Netsential confirmed that a threat actor had leveraged a compromised Netsential customer user account and the web platform’s upload feature and exfiltrated other Netsential customer data, including several U.S. police agencies, including Fusion Centers.
Netsential is the same web hosting company that was previously abused by attackers to infect targeted victims with ransomware by sending spoofed spear-phishing emails disguised as NFCA.
Third Party Data Evaluation to prevent Breach
Security experts say that the government needs to be more careful in relying on third-parties to have access and control over data – particularly sensitive data.
- “The BlueLeaks hack is the latest example of malicious actors targeting third-party vendors to access sensitive government data,” Mike Rieme, global chief security architect at Pulse Secure said via email, “Despite the fact that poor security practices among contractors often result in larger breaches like this one, which included data from over 200 law enforcement agencies, reliance on third-party entities to manage data and digital services continues to grow in the government sector.”
- The hack sheds light on police departments, particularly as protests continue to spread across the globe in the wake of George Floyd’s death. Various Twitter users, for their part, said they scoured the data reportedly uncovered by BlueLeaks, including reports that point to the FBI’s monitoring of social media activity related to the Black Lives Matter protests.
- Another (supposed) hack of the Minneapolis police department, perpetrated at the hands of the Anonymous hacktivist group, made headlines earlier in June – though security experts like Troy Hunt were quick to call the “breach” fake.
Recommendations
Companies must ensure that data is adequately protected to prevent loss or theft. It is possible to minimize the risk of data breaches by following a number of best practices:
- Organizations should be careful in relying on third-parties to have access and control over data – particularly sensitive data.
- Patching and updating software as soon as Security Updates are available
- ENCRYPTION and Data Backup for sensitive data.
- Upgrading when software is no longer supported by the manufacturer.
- Enforcing BYOD security policies.
- Enforcing strong credentials and multi-factor authentication.
- Educating employees on best security practices and ways to avoid socially engineered attacks.



