Academics bypass PINs for Visa contactless payments
A team of academics has discovered a security bug that can be abused to bypass PIN codes for Visa contactless payments.
This means criminals can use stolen Visa contactless card to pay for expensive products, above the transaction limit, and without needing to enter the card’s PIN code. In reality, the attacker is actually paying with data received from a (stolen) Visa contactless card that is hidden on the attacker’s body.
How the attack works
A successful attack requires four components:
- (1+2) two Android smartphones,
- a special Android app developed by the research team,
- a Visa contactless card.
The Android app is installed on the two smartphones. It will work as a card emulator and a POS (Point-Of-Sale) emulator. The phone that emulates a POS device is put close to the stolen card, while the smartphone working as the card emulator is used to pay for goods.
The attack is that the POS emulator asks the card to make a payment, modifies transaction details, and then sends the modified data via WiFi to the second smartphone that makes a large payment without needing to provide a PIN.
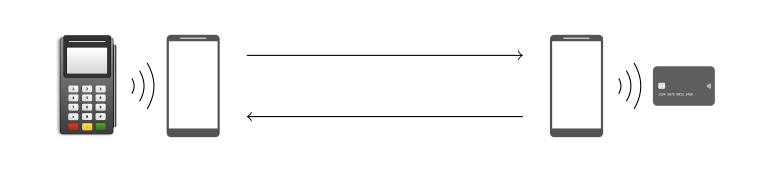
The attack is possible because of description of design flaws in the EMV standard and in Visa’s contactless protocol. It allows an attacker to alter data involved in a contactless transaction.
The attack consists of a modification of a card-sourced data object before delivering it to the terminal. These modifications are:
- PIN verification is not required
- the cardholder was verified on the consumer’s device
These modifications are carried out on the smartphone running the POS emulator, before being sent to the second smartphone, and then relayed to the actual POS device
According to researchers, app does not require root privileges or any fancy hacks to Android.
The attack is extremely stealthy and can be easily mistaken for a customer paying for products using a mobile/digital wallet installed on their smartphone.
Recommendations
It is recommended to consider the following best practices:
- It is highly advised to update your smart device
- If you are using digital wallet set strong password
- Make sure all payment related applications are installed from authorized site.
- Do not open any email regarding password modification until you requested for changes.



