Hackers decrypt VoltE encryption to spy on phone calls
What is VoLTE?
As the name suggests, Voice over LTE is what happens when your carrier allows you to place a phone call over your LTE connection instead of the older legacy voice networks. Verizon Wireless, for example, traditionally used 1XRTT for all of your voice calls, relying on LTE for data. Pretty much every new phone will support VoLTE, but not every phone will let you turn it on or off.
What is the ‘ReVoltE Attack’ ?
‘ReVoLTE,’ could let remote attackers break the encryption used by VoLTE voice calls and spy on targeted phone calls. The ReVoLTE attacks exploit the reuse of the same keystream for two subsequent calls within one radio connection. This weakness is caused by an implementation flaw of the base station (eNodeB).
The attack doesn’t exploit any flaw in the Voice over LTE (VoLTE) protocol; instead, it leverages weak implementation of the LTE mobile network by most telecommunication providers in practice, allowing an attacker to eavesdrop on the encrypted phone calls made by targeted victims.
The crux of the problem is that most mobile operators often use the same keystream for two subsequent calls within one radio connection to encrypt the voice data between the phone and the same base station, i.e., mobile phone tower.
How Does the ReVoLTE Attack Work?
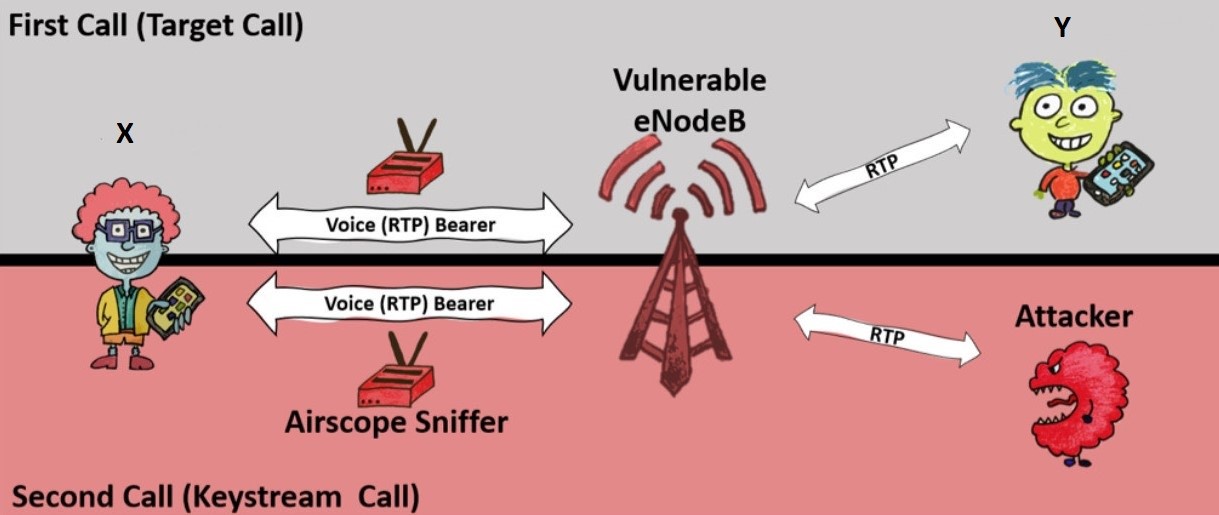
To initiate this attack, the attacker must be connected to the same base station as the victim and place a downlink sniffer to monitor and record a ‘targeted call’ made by the victim to someone else that needs to be decrypted later, as part of the first phase of ReVoLTE attack.
Once the victim hangs up the ‘targeted call,’ the attacker is required to call the victim, usually within 10 seconds immediately, which would force the vulnerable network into initiating a new call between victim and attacker on the same radio connection as used by previous targeted call.
Once connected, as part of the second phase, the attacker needs to engage the victim into a conversation and record it in plaintext, which would help the attacker later reverse compute the keystream used by the subsequent call.
However, the length of the second call should be greater than or equal to the first call in order to decrypt each frame; otherwise, it can only decrypt a part of the conversation.
Detection and Recommendations
- Open source Android app, called ‘Mobile Sentinel,’ can be used to detect whether their 4G network and base stations are vulnerable to the ReVoLTE attack or not.
- It is advised not to reuse the same keystream by base stations as it allows the attackers to decrypt the contents of VoLTE powered voice calls.
Since this flaw is in the encryption used by the telecom operators, we recommend the following phone hygiene
- Never connect your phone to public wifis or unknown networks.
- Avoid using unprotected bluetooth network and turn off your Bluetooth service when you aren’t using it.
- Regularly delete your browsing history, cookies, and cache. Removing your virtual footprint is important in minimizing the amount of data that can be harvested by prying eyes.



