QakBot Banking Trojan Returned With New Sneaky Tricks to Steal Your Money
According to new research, a notorious banking Trojan aimed at stealing bank account credentials and other financial information has now come back with new tricks up its sleeve to target government, military, and manufacturing sectors in the US and Europe.
QakBot Back in Business
According to a research, QakBot is financial malware known to target businesses to drain their online banking accounts. The malware features worm capabilities to self-replicate through shared drives and removable media.
It uses powerful information-stealing features to spy on users’ banking activity and eventually defraud them of large sums of money. Though well-known and familiar from previous online fraud attacks, QakBot continually evolves.
QakBot is modular, multithread malware whose various components implement online banking credential theft, a backdoor feature, SOCKS proxy, extensive anti-research capabilities and the ability to subvert antivirus (AV) tools.
QakBot’s current variant can disable security software running on the endpoint. Upon infecting a new endpoint, the malware uses rapid mutation to keep AV systems guessing. It makes minor changes to the malware file to modify it and, in other cases, recompiles the entire code to make it appear unrecognizable.
It has an active malspam campaign which infects organizations, and it manages to use a ‘third-party’ infection infrastructure like Emotet’s to spread the threat even further.
Manipulating email threads to disperse the malware
Qbot has evolved over the years from an information stealer to an adept in delivering other kinds of malware, including Prolock ransom-ware, and even remotely connect to a target’s Windows system to carry out banking transactions from the victim’s IP address. Attackers usually infect victims using phishing techniques to lure victims to websites that use exploits to inject Qbot via a dropper.
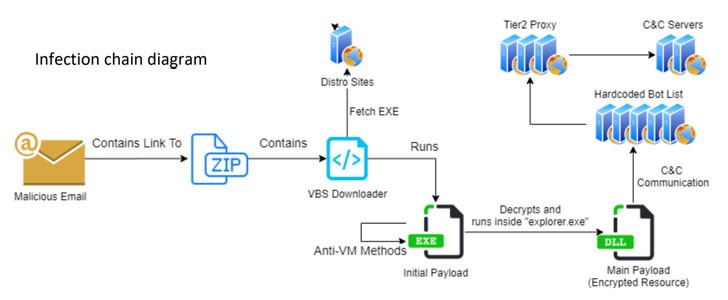
The first step begins with a specially crafted phishing email containing an attached ZIP file or a link to a ZIP file that includes a malicious Visual Basic Script (VBS), which then proceeds to download additional payloads responsible for maintaining a proper communication channel with an attacker-controlled server and executing the commands received.
The phishing emails sent to the targeted organizations, which take the form of COVID-19 lures, tax payment reminders, and job recruitments, not only includes the malicious content but is also inserted with archived email threads between the two parties to lend an air of credibility.
The conversations are gathered beforehand using an email collector module that extracts all email threads from the victim’s Outlook client and uploads them to a hardcoded remote server.
Qbot comes with an hVNC Plug-in that makes it possible to control the victim machine through a remote VNC connection. An external operator can perform bank transactions without the user’s knowledge, even while they are logged into their computer
Qbot is also equipped with a separate mechanism to recruit the compromised machines into a botnet by making use of a proxy module that allows the infected machine to be used as a control server. Aside from packing components for grabbing passwords, browser cookies, and injecting JavaScript code on banking websites, the Qbot operators released as many as 15 versions of the malware.
Recommendations
It is recommended to consider the following best practices against QakBot Infection:
- Use adaptive malware detection solutions that provide real-time insight into fraudster techniques and address the relentless evolution of the threat landscape.
- Since this malware may come through infected websites or via email attachments it is recommended to not open any email attachment that seems irrelevant, or if the sender seems suspicious/unrecognizable.
- Users can protect themselves and their organizations by practicing browsing hygiene, disabling online ads, filtering macro execution in files that come via email and observing other security best practices.
- It is suggested to keep all operating systems up to date across the organization, update frequently used programs and delete those no longer in use. Make sure domain accounts are configured with the least privilege required to perform job tasks.
- Organizations may create a random domain admin account for safety purposes and ensure that it reports directly to the security information and event management (SIEM) system upon any attempt to use it..
- Stop sharing folders that show signs of infection or set shared folders to read-only. Removing admin shares is an option that should only be used as a last resort as this can cause other issues and hinder management.
- Finally, prevent workstation-to-workstation communications where possible to force malware out of the trenches and into areas where central detection systems will pick it up quickly.



