Hackers Access TCP/UDP Service Using NAT/Firewall Bypass Attack
A new technique allows an attacker to bypass firewall protection and remotely access any TCP/UDP service on a victim machine. It is known as NAT Slipstreaming, which involves sending the target a link to a malicious site that, when visited, ultimately triggers the gateway to open any TCP/UDP port on the victim, resulting in restrictions.
The findings were revealed by privacy and security researcher Samy Kamkar. The technique was carried out using a NetGear Nighthawk R7000 router running Linux kernel version 2.6.36.4.
What is NAT?
It stands for Network address translation. It is the process where a network device, such as a firewall, remaps an IP address space into another by modifying network address information in the IP header of packets while they are in the process of transmission. It limits the number of public IP addresses used in an organization’s internal network and improves security by letting a single public IP address to be shared among multiple systems.
A NAT firewall works by only allowing internet traffic to pass through the gateway if a device on the private network requested it. Any unsolicited requests or data packets are discarded, preventing communication with potentially dangerous devices on the internet. If inbound internet traffic does not have a private IP address to forward to beyond the gateway, the NAT firewall knows the traffic is unsolicited and should be discarded.
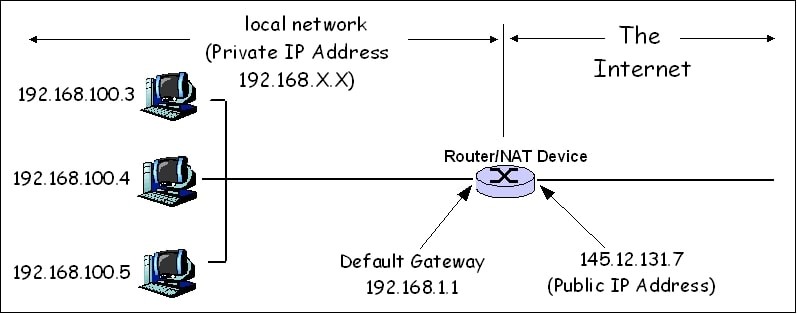
Computers and servers on the internet can only see the public IP address of the router and none of the private IP addresses of specific devices, like phones, laptops, smart TVs, internet-of-things devices, and game consoles. This is also known as IP masquerading.
NAT Slipstreaming:
NAT Slipstreaming works by taking advantage of TCP and IP packet segmentation to remotely adjust the packet boundaries and using it to create a TCP/UDP packet starting with a SIP method such as REGISTER or INVITE. Session Initiation Protocol initiate, maintain, and terminate real-time multimedia sessions for voice, video, and messaging applications. To achieve this, a large HTTP POST request is sent with an ID and a hidden web form that points to an attack server running a packet sniffer, which is used to capture the MTU size, data packet size, TCP and IP header sizes, among others, and subsequently transmitting the size data back to the victim client over a separate POST message.
NAT Slipstreaming allows an attacker to remotely access any TCP/UDP service bound to a victim machine, bypassing a victim’s network address translation (NAT) or firewall security controls in the process – providing a victim is first tricked into visiting a site under the would-be hacker’s control. It exploits the user’s browser in conjunction with the Application Level Gateway (ALG) connection tracking mechanism built into NATs, routers, and firewalls by chaining internal IP extraction via a timing attack, automated remote MTU and IP fragmentation discovery, TCP packet size massaging, TURN authentication misuse, precise packet boundary control, and protocol confusion through browser abuse.
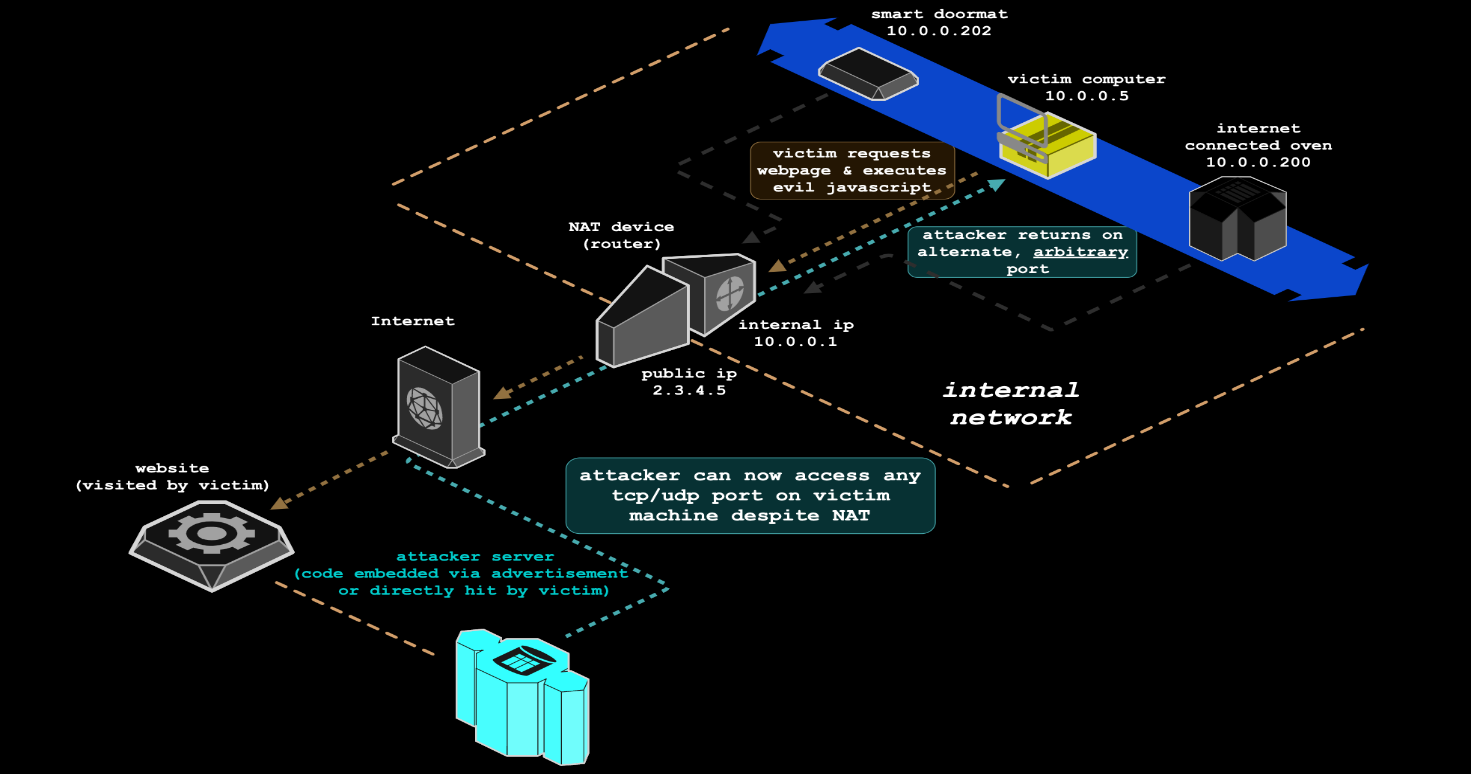
Just as the packets reach the attack server and it’s determined that the SIP packet isn’t rewritten with the public IP address, an automatic message is sent back to the client, asking it to adjust its packet size to a new boundary based on the data previously gleaned from the sniffer. Armed with the right packet boundary, the NAT is deceived into thinking, “this is a legitimate SIP registration and from a SIP client on the victim’s machine,” eventually causing the NAT to open up the port in the original packet sent by the victim.
Recommendations:
- Using Multiple Firewall Solutions at Different Levels: Use multiple firewalls when creating a defense that segments your network and apps, consider solutions so the same exploits and vulnerabilities won’t work against all of your network firewalls.
- Stay on Top of Security Patches/Updates: Many attacks leverage known vulnerabilities in popular software and security tools. By applying security patches to your hacker protection software, you can keep cybercriminals out more easily.
- Set Strong Password Policies and Multifactor Authentication: Hijacked user accounts are a common tool for attackers to bypass firewall security tools. So, making it harder to steal and use account credentials can help limit the risk of a breach. Setting strong password policies (8+ characters long, use case-sensitive letters, adding special characters, etc.) and applying multifactor authentication can help prevent account hijacking.
Regularly Running Penetration Tests: Penetration testing can help identify previously unknown security vulnerabilities in the apps and firewalls that your organization uses. Some common measures include applying custom patches to software code and firewall rules or replacing the vulnerable solution with something that is better protected.



