IoT Chipmaker Advantech Attacked by Conti Gang
Ransomware:
There are several paths ransomware can take to access a computer. One of the most common delivery systems is phishing spam. It is an attachment that comes to the victim in an email, masquerading as a file it should trust. Once it is downloaded and opened, it takes over the victim’s computer, especially if they have built-in social engineering tools that trick users into allowing administrative access. Some other, more aggressive forms of ransomware, like NotPetya, exploit security holes to infect computers without needing to trick users.
Many ransomware attackers threaten victims with permanent loss of their personal files if the ransom is not paid within a 24 hour timeframe. To enhance deception, some ransomware notifications impersonate law enforcement or government agencies and represent the extortion as a fine.
Phases of Ransomware:
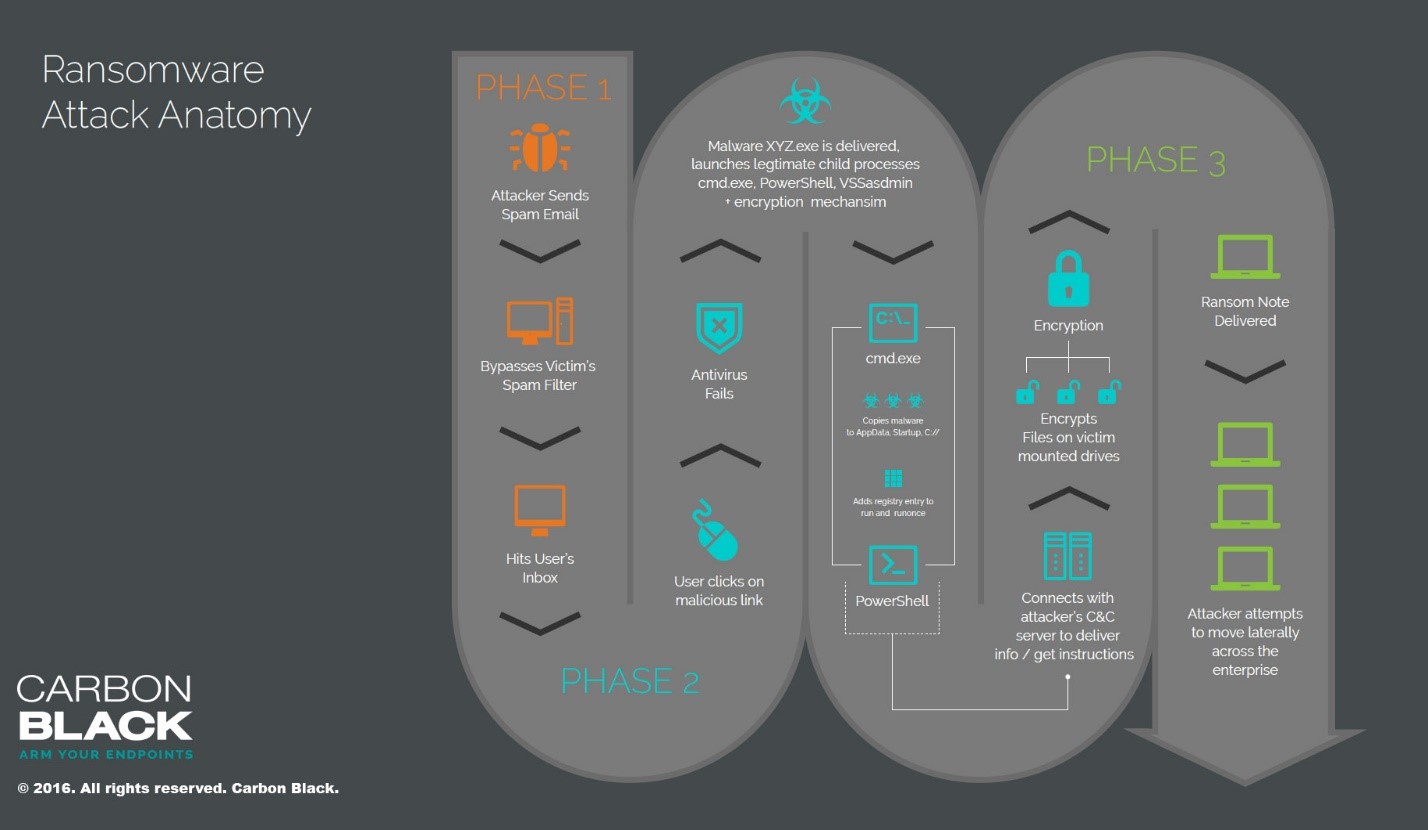
- Phase 1: Infiltration
The attacker sends a phishing email or a malicious exploit code to the user which somehow manages bypass the system’s spam filter and reaches to the user’s inbox.
- Phase 2: Execution
After receiving the phishing email when the user clicks on the malicious link some executions start processing in the backend. It manages to fail the antivirus and start running child processes which begin the process of encryption. It connects the system with the command and control server of the attacker to send them information and receive commands from them. It also performs backup hijacking i.e. deleting backup copies of the files.
- Phase 3: Ransom
After successful encryption of the user’s data, the attacker sends a message notifying them that their data has been encrypted and they have to pay some amount (usually in bitcoin) to decrypt that data.
The Attack:
After successful encryption of the user’s data, the attacker sends a message notifying them that their data has been encrypted and they have to pay some amount (usually in bitcoin) to decrypt that data.
Rising of Ransomware:
Kaspersky researchers released a report Monday that said ransomware will be one of cybersecurity’s biggest threats in the year ahead. They also pointed specifically that the single biggest factor driving up ransom prices is the leak sites. Due to successful operations and extensive media coverage, the threat actors behind targeted ransomware systematically increased the amounts of victims were expected to pay in exchange for not publishing stolen information.
Now the ransomware attack is not about the data encryption only, it is also now about the disclosure of the confidential information gathered from any organization. And now It is up to the organizations to shore up their defenses in preparation for the next inevitable ransomware attack.
Remediation:
- Do not pay the ransom as it encourages and funds these attackers, and even if the ransom is paid, there is no guarantee that you will be able to regain access to your files.
- Restore any impacted files from a known good backup as it is the fastest way to regain access to your data.
- Do not provide personal information when answering an email, unsolicited phone call, text message, or instant message.
- Contact your IT department if you or your coworkers receive suspicious calls.
- Maintaining a strong firewall and keep your security software up to date.
- Inbound e-mails should be scanned for known threats and should block any attachment types that could pose a threat.
Make sure you use a trustworthy Virtual Private Network (VPN) when accessing public Wi-Fi like Norton Secure VPN.



