Android malware RANA from Iran can read your Personal messages
Android malware infamously known as RANA of Iranian origins is a Spyware suspected to be implanted in smartphones and developed by a sanctioned Iranian threat actor. Once in place the spyware can give the attackers free reins to access private messages from instant messaging apps, connect to unauthorized Wi-Fi connections and eavesdrop on phone calls.
In the month of September, sanctions were imposed on APT39 (aka Chafer, ITG07, or Remix Kitten, a threat actor backed by the Iranian Ministry, for conducting targeted attacks on Iranian dissidents, journalists, and international companies in the telecom and travel sectors.
The Federal Bureau of Investigation (FBI) acting on the sanctions, published to the public a threat analysis report describing how Rana Intelligence Computing Company uses certain tools developed by it. The FBI further investigated that there were eight separate and distinct sets of malware and spywares used by APT39, which were previously undisclosed. These malicious apps are used to conduct computer intrusion and reconnaissance activities, including an Android spyware app called “optimizer.apk” with information-stealing and remote access capabilities.
The malicious app implant is capable of stealing information and remote access functionality by sneakily gaining root access of an Android system without ever being detectable by a user. The major breaches of security is that the malware is capable of including the retrieval of HTTP, get requests from the C2 server, obtaining device data, compressing and encrypting the collected data, and sending it via HTTP, POST requests to the malicious C2 server.”
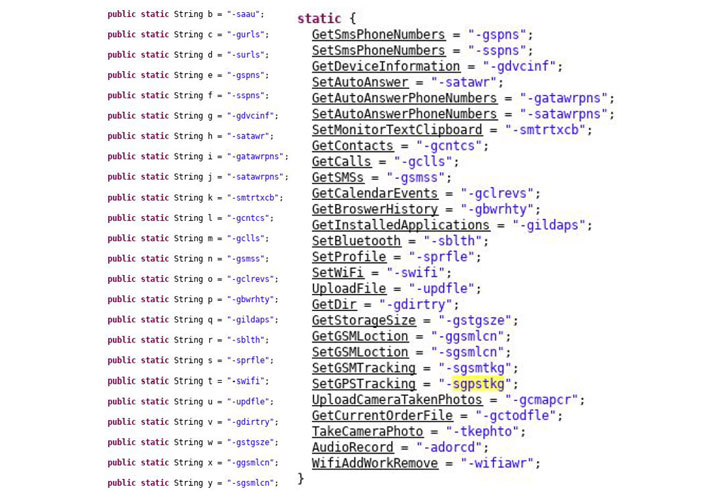
Digging deeper into the FBI report a research company analyzed a previous un-obfuscated version of RANA. Their report mentions that the spyware can:
Recordaudio
Click pictures
Auto-answer phone calls and record them
Execute malicious commands, sent in the form of innocent text messages
Access and download personal messages from instant messaging apps like WhatsApp, Instagram, Telegram and Skype.
Moreover, it can make the compromised Android system that can send the above listed data to the attackers by force-connecting to a custom Wi-Fi access point in order to stay undetected.
Mobile phones are a new honey-pot for threat actors because of their capabilities in sourcing of data like images, audio, texts, conversations, bank details, identity details, passwords and location. Since, the Android operating system maintains the biggest part of the global smartphone market share, it follows that it is also the primary target of mobile malwares and spywares.
Remediation:
The following steps can help reduce the likelihood of getting your Android system infected with RANA:
- Avoid using apps and websites which are not trusted or well-known.
- Avoid clicking on ads that pop-up on apps and websites.
- Never download or install anything from an unknown or suspicious website or pop-up.
- Install an anti-virus with browsing protection and real-time scanning for threats.



