SolarWinds Orion backdoor leaves nearly 18,000 users vulnerable
The Orion products from SolarWinds, an enterprise monitoring software developer and vendor fell prey to one of the most consequential supply chain attacks which left almost 18,000 top-level customers vulnerable.
The company has over 300,000 customers around the world, including all of US military and almost all of the fortune-500 companies.
As per the company’s acknowledgement the affected versions are 2019.4. HF 5 and 2020.2 only.The company officials received an alert that their Microsoft Office email and productivity accounts were vitiated.
What Happened?
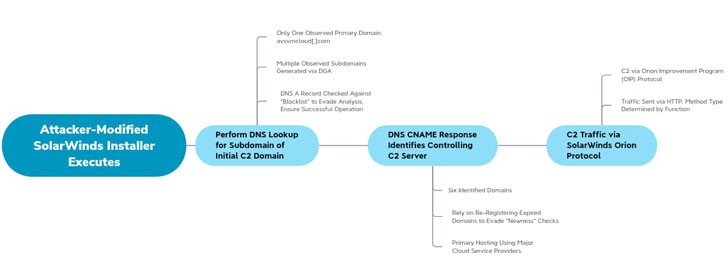
FireEye, a cybersecurity firm informed that it caught a 9 month long global intrusion campaign that has been targeting private as well as public entities that sneak malicious code into the genuine software updates of the Orion product range of SolarWinds. This enabled the threat actors to break into the companies via their network and install a backdoor called Sunburst. The malicious backdoor (“SolarWinds.Orion.Core.BusinessLayer.dll”) uses the domains avsvmcloud.com to connect to a remote access network to prepare possible second-stage payloads, move laterally in the organization’s network and vitiated or steal the data, according to Microsoft.
Who was affected?
Direct result of a rogue SolarWinds update led to the breaching of the US Department of Homeland Security and the departments of Commerce and Treasury.
The actual damage that is caused by this security incident is worldwide. The suspected perpetrators of this incident are a collected affiliate of hackers backed by the Russian intelligence, APT29.
The presence of the Orion products everywhere and the 9-month long campaign make the Sunburst backdoor a large-scale attack with multiple industries and network operators as its victims.
For its part, SolarWinds is expected to issue a second hotfix very soon that replaces the vulnerable component and adds several extra security enhancements.
Remediation:
We recommend the following fixes with immediate effect:
- Recover the instance of SolarWinds’ Orion that was previously installed on the system before the breach.
- Promptly install the second hot-fix of Orion software as soon as SolarWinds releases it.
- It is imperative that a continuous monitoring of network traffic is conducted and a surveillance of what the hosts are communicating over the network.
- The passwords and user authentication details of all the affected segments of the system and network need to be reset and reissued.
- The device on which the backdoor as affected should be recovered and restored to an old restore point before the installation of the vulnerable version of the Orion software/s.



