Card Skimmer stealing Payment Details Of Online Shopping Websites
An online card skimmer, known as Mage cart is on the loose and infecting shopping stores powered by Shopify, BigCommerce, Zencart, and Woocommerce. This new malware can meddle with the checkout process on store websites using multiple online store management systems by injecting a malicious checkout page and steal payment information.
How does it work?
Usually, malwares are designed to skim one type of online store management system but this web-skimming malware can compromise multiple e-commerce platforms to harvest payment information of the users.
Magecart script has infected e-commerce stores hosted on major service providers like Shopify, BigCommerce, Zencart, and Woocommerce.
The malware injects a fake checkout page before the customers land on the real checkout page of the website. The payment and personal information entered on this malicious page is then intercepted using a keylogger.
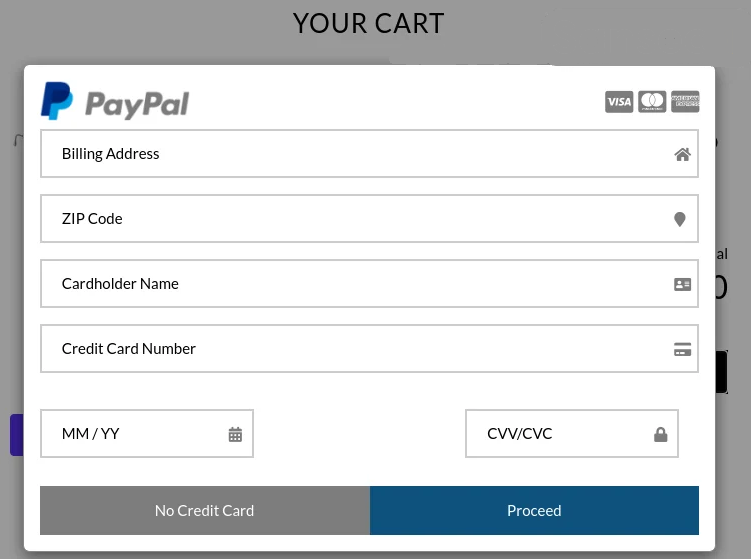
After the “Proceed” button on the fake checkout page is hit by the customer the malware injects an error page to evade detection and redirects them back to the legitimate checkout process and payment form.
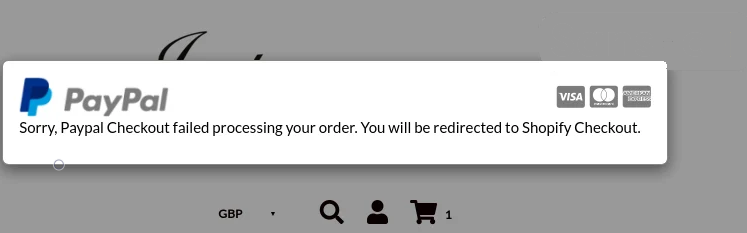
The Magecraft malware uses automatically generated domains based on a counter and encoded using base64 encoding to exhilarate data. For e.g.,zg9tywlubmftzw5ldza[.]com, zg9tywlubmftzw5ldze[.]com, and so on
How long has this been going on?
The researchers traced back the automatically generated domains which the Magecraft was using. The first domain was registered on the 31st Aug, 2020.
Remediation:
We suggest the following remediations: –
- Use anti-virus with real-time scanning for websites visited.
- Avoid shopping from unknown websites.
- Only enter sensitive information like payment details into trusted websites.
- Look for suspicious markers like glitches or wrong web addresses.
- Follow a trustworthy and prompt portal that can help keep up with all things Cyber Security.



