Hackers take advantage of Pulse secure VPN Zero-Day flaws in sophisticated worldwide campaign.
The ongoing COVID-19 crisis has led to an overnight shift to remote work culture, and VPNs have played a crucial role to make this possible. VPNs have end up as a prime target for cybercriminals during the last few months.
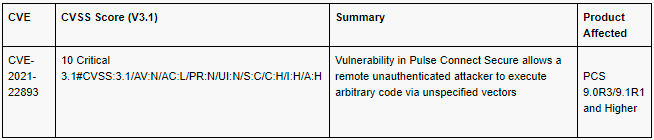
A critical zero-day security vulnerability in Pulse Secure VPN devices has been exploited by attackers from China to launch cyber-attacks against U.S. defense, finance and government targets, as well as victims in Europe, researchers said.
CVE AFFECTED:
The flaw, tracked as CVE-2021-22893, permits remote code-execution (RCE) and is getting used in the wild to gain administrator-level access to the devices, according to Ivanti research. Pulse secure stated that the 0-day might be patched in early May, but in the intervening time, the organisation worked with Ivanti (its parent company) to release both mitigations and the pulse connect secure Integrity tool, to help figure out whether systems have been impacted.
Cause of the Exploit:
According to the Pulse Secure advisory, the newly observed critical security flaw is rated 10 out of 10 on the CVSS vulnerability-rating scale. It’s an authentication bypass vulnerability that could permit an unauthenticated user to carry out RCE at the Pulse connect secure gateway.
Impact:
Attackers can utilise this flaw to further compromise the PCS device, implant backdoors and compromise credentials.
Phil Richard, chief security officer at Ivanti, which acquired Pulse Secure in 2020, said:
“The new issue, discovered this month, impacted a very limited number of customers. The team worked quickly to provide mitigations directly to the limited number of impacted customers that remediates the risk to their system.”
Remediations:
- Upgrade the Pulse Connect Secure server software version to the 9.1R.11.4 which will be available in early May.
- For the time being, CVE-2021-22893 can be mitigated by downloading a workaround from Pulse Secure. The workaround will disable the following features under the PCS appliance.
- Windows File Share Browser
- Pulse Secure Collaboration
The Integrity Tool can be used to check the integrity of the running version of Pulse Connect Secure. The integrity tool can allow an administrator to verify the PCS Image installed on Virtual or Hardware Appliances. This tool checks the integrity of the complete file system and finds any additional/modified file(s).



