Cyberpunk 2077 is delivering Ransom ware into Androids
Kaspersky Lab’s Tatyana Shishkova discovered a new Android malware with ransom ware has been going around Android devices in the name of beta version of Cyberpunk 2077 game.
Background:
Cyberpunk 2077 is the most anticipated game that has ever been. After a period of time, the game was released for Windows OS, Sony’s PlayStation and Microsoft‘s Xbox consoles, a beta version of the game surfaced that had been designed for devices running Android. Interestingly, there is no word about an android version from the developers of the game.
About the ‘Beta’ version:
The beta version of the game is available to download for free from a website bearing the address ‘cyberpunk2077mobile[.]com’. The website bears no similarities to the official website of Cyberpunk 2077. It looks like a web page version of the Google Play application store, with good detailing to fool an innocent eye.
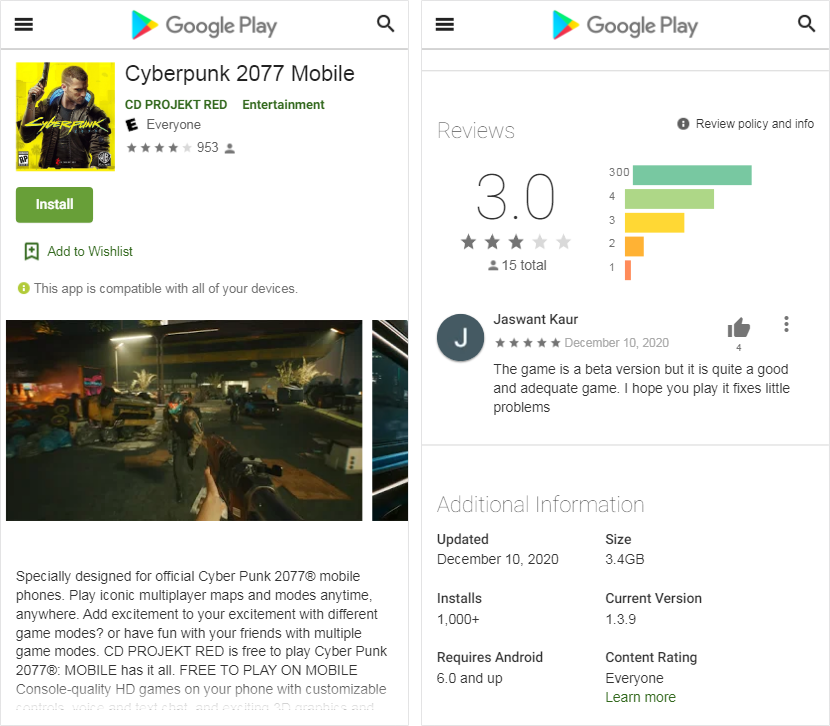
The website shows the download count to be a 1000 (at the time of writing this article) and there were some reviews of users saying that even though it has bugs it is “good and adequate” for a beta version. The webpage lists the size of the downloadable to be 3.4GB, while the file that’s actually downloaded on the device is less than 3MB.
What Happens?
After the download completes, the file of the fake beta version of the game, user are prompted to give it some permissions, all of which are required to run the game. Even if a single permission is denied the game will not run.
Once users grant those permissions, they won’t see the game installed instead there will be a ransom demand on the screen.
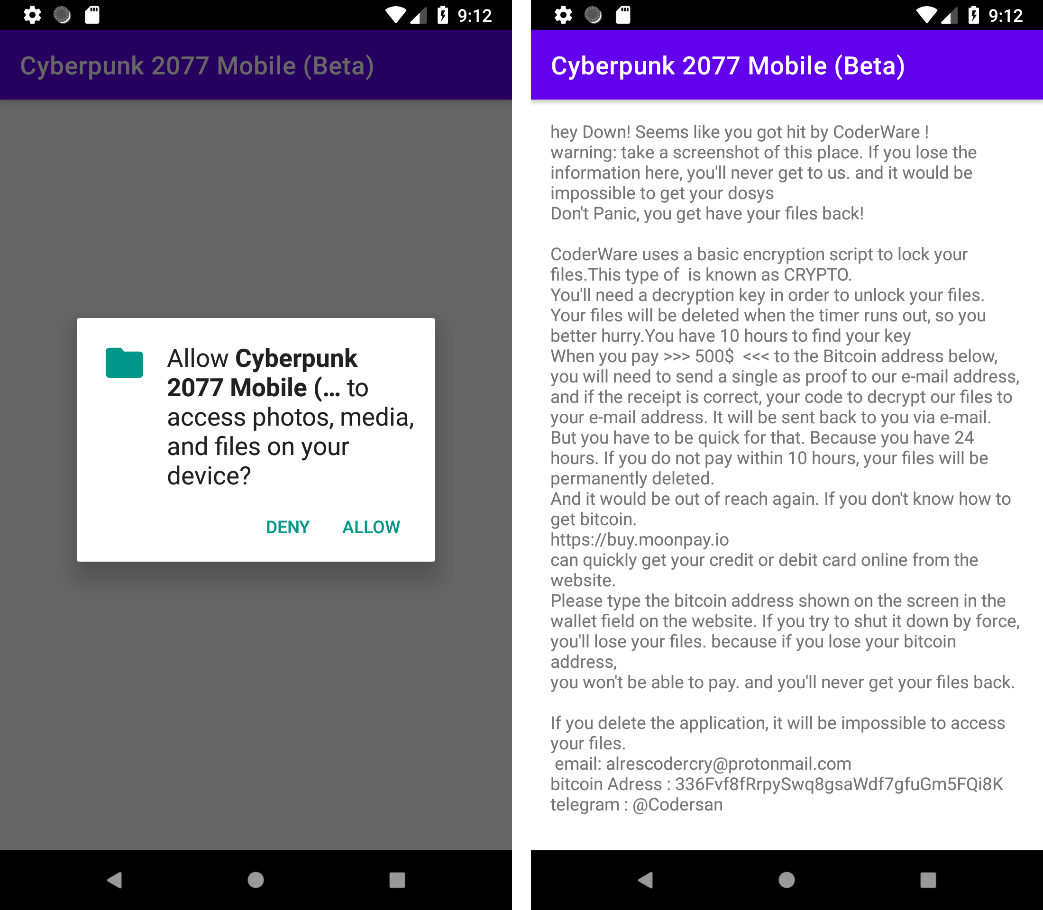
The message is in improper English, it informs the victims of the attack that all of their important and personal files that were on the device have been encrypted. In order to get their files unencrypted or access them the again the victims are demanded a ‘ransom’ of $500 in the form of Bitcoins. The threat actors further say that if the victim doesn’t pay up the ransom in time all of their data will be permanently erased. Moreover, the note also warns that any attempt to remove the ransomware will also result in a loss of victim’s data.
Is the Encryption real?
On investigation on couple of samples, it was found that what really happens to the files on the infected android devices, it is sure that the files are indeed encrypted and are assigned to an extension ‘. coderCrypt’. In addition, the malware places a README.txt file, containing the same ransom message, in each folder.
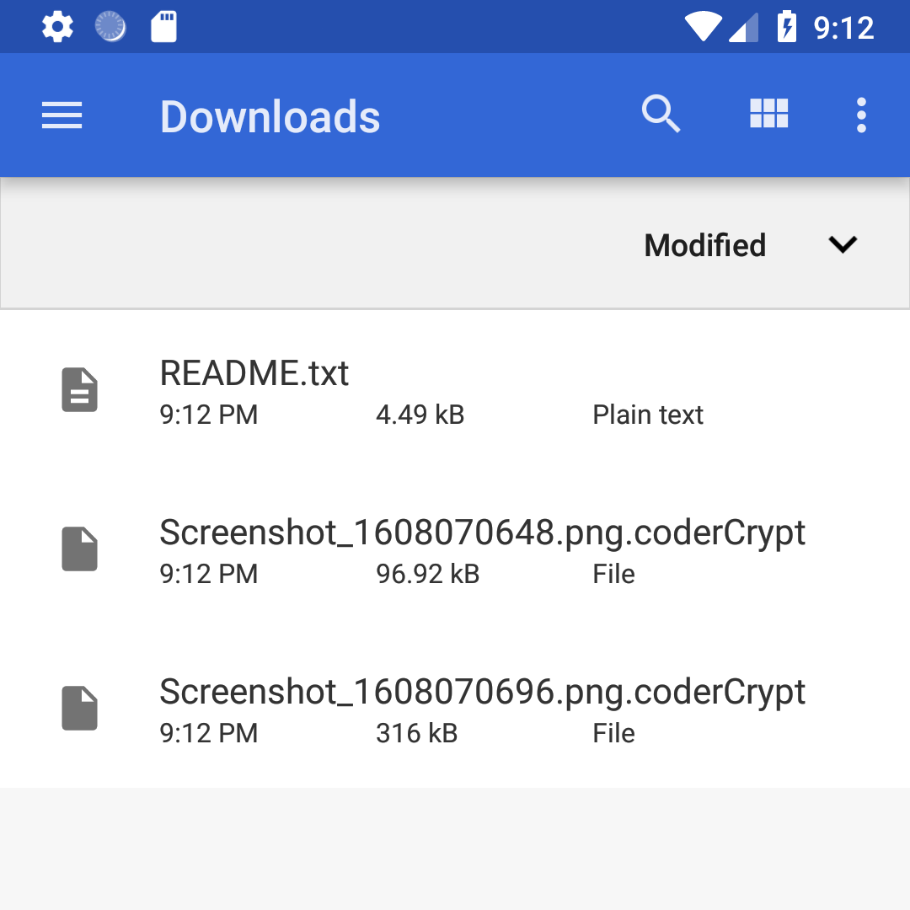
Over $7,400 in the form of bitcoins have been transferred the cybercriminals’ wallet.
Recommendation:
- Users are advised to make a backup of the encrypted files.
- Use the free decrypting tool from Kaspersky at NoMoreRansome website.
- It is highly recommended to download apps only from official stores or from the developer’s official website.
- Scan for news of beta versions, releases, and promotions on the developer’s website. If the developer has no information, or the game is not officially out yet, anything else is fake.
- Use a reliable security solution on all devices to catch malware before it can do any harm.
- Regularly back up important files to recover them promptly in case of damage or loss.



