Rocke Group’s Malware (Pro-Ocean)
Introduction
Pro-Ocean is a known previous years vulnerability and now it is targeting Apache ActiveMQ (CVE-2016-3088), Oracle WebLogic (CVE-2017-10271) and Redis (unsecure instances). In this case the malware runs in Tencent Cloud or Alibaba Cloud, it will use the exact code of the previous malware to uninstall monitoring agents to avoid detection. Once installed, the malware kills any process that uses the CPU heavily, so that it’s able to use 100% of the CPU.
Terms
- UPX: It’s portable, extendable, high-performance executable packer for several executable formats.
- XMRig: The XMRig CPU Miner is a legitimate crypto currency mining program that is used to mine for crypto currency using a computer’s CPU. This program is also commonly used by malware developers to mine coins on an infected computer without the owner’s permission.
- HashFish: HashFish Miner is the mining software that can select/auto select certain cryptos ( XMR, ETH, ZEC, etc.,)to mine and users can get payment to their own wallet in bitcoin.
How the Malware Works
Steps:
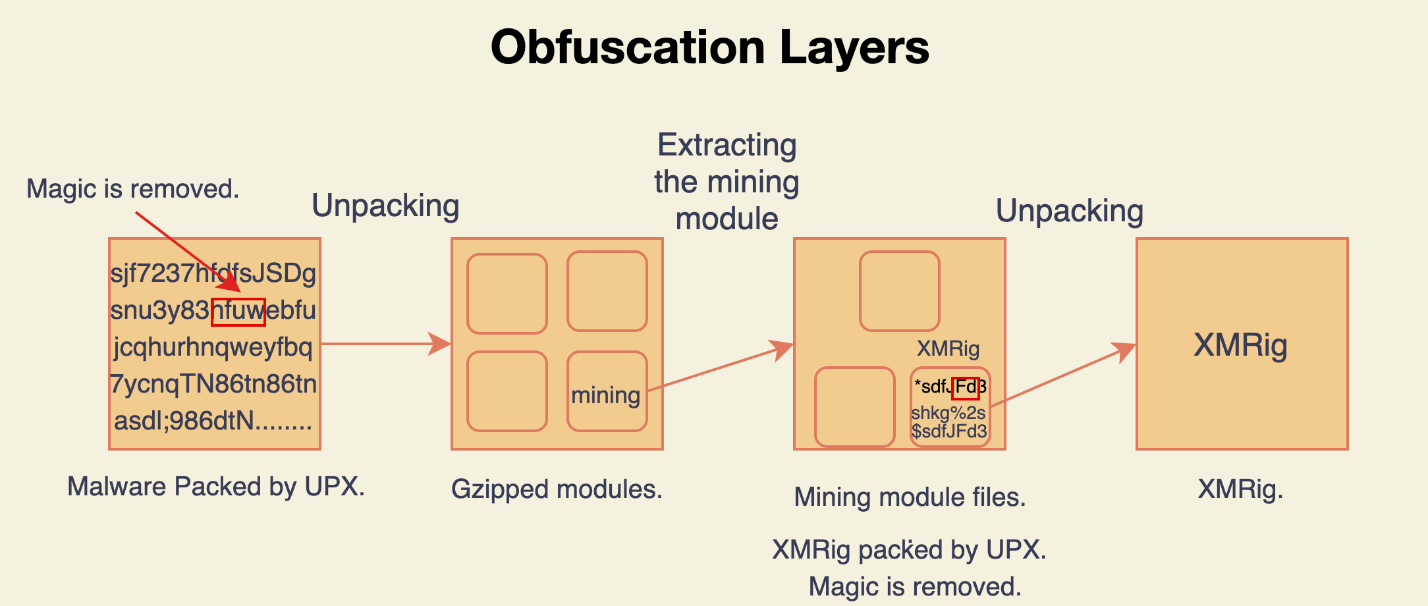
- UPX packed the binary file it means that the actual malware is compressed inside the binary and is extracted and executed during the binary execution.
- The UPX magic string has been deleted from the binary, and therefore, static analysis tools cannot identify this binary as UPX and unpack it. (as Shown in below figure)
- The modules are zipped inside the unpacked binary.
- The XMRig binary is inside one of the zipped modules and is also packed by UPX and does not have the UPX magic string.
Affected CVE:
- CVE-2016-3088: The Fileserver web application in Apache Active MQ 5.x before 5.14.0 allows remote attackers to upload and execute arbitrary files via an HTTP PUT followed by an HTTP MOVE request.
- CVE-2017-10271: Vulnerability in the Oracle Web Logic Server component of Oracle Fusion Middleware (subcomponent: WLS Security). Supported versions that are affected are 10.3.6.0.0, 12.1.3.0.0, 12.2.1.1.0 and 12.2.1.2.0. Easily exploitable vulnerability allows unauthenticated attacker with network access via T3 to compromise Oracle Web Logic Server. Successful attacks of this vulnerability can result in takeover of Oracle Web Logic Server. CVSS 3.0 Base Score 7.5 (Availability impacts). CVSS Vector: (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
The Modules using in this Malware:
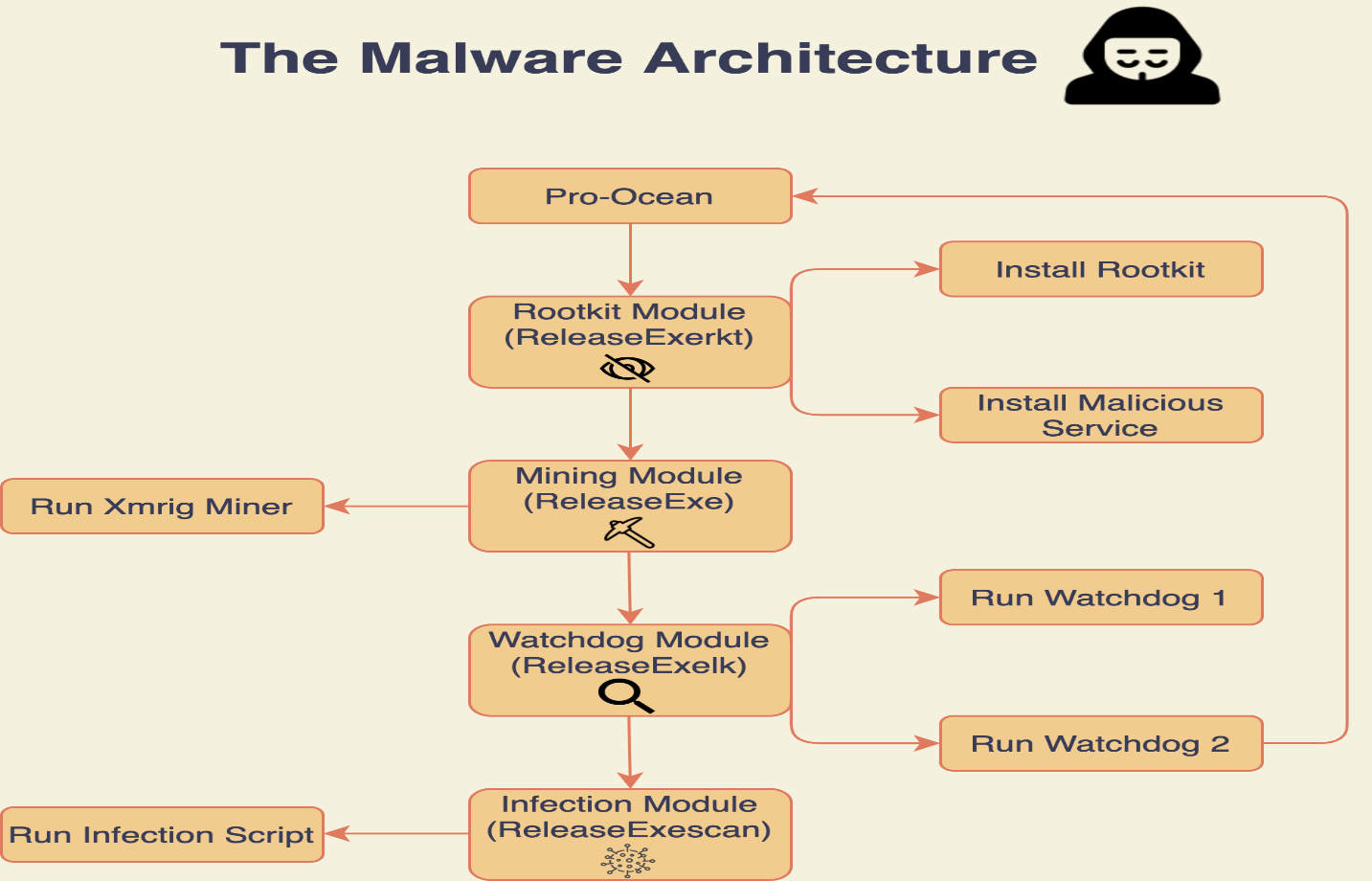
(All The Modules)
Modules:
- Mining Module: Its goal is to mine into the attacker’s wallet, and it does so by deploying an XMRig miner 5.11.1 and a JSON configuration, then starting to mine. This is a common operation for crypto jacking malware.
- Watchdog Module: This process loops forever and checks that the malware is running. If not, it runs it.
- Hiding Module: The hiding module is responsible for concealing Pro-Ocean’s malicious activity.
Installation of the Malware:
It is written in Bash. Two of the malware’s targets are Alibaba Cloud and Tencent Cloud. Below are the steps:
- Attempt to remove other malware and miners including Luoxk, XMRig, Hashfish and more. It does this by running the “grep” command searching for other processes and network connections and then terminates them if found.
- Erase all of the previous tasks to make sure that other malware will not be able to recover.
- Disable the ip tables firewall so that the malware will have full access to the internet.
- In the case that the malware runs in Tencent Cloud or Alibaba Cloud, it will use the exact code of the previous malware to uninstall monitoring agents to avoid detection.
- Look for SSH keys and attempt to use them in order to infect new machines.
Recommendations:
- Palo Alto Networks Prisma Cloud customers are protected from Pro-Ocean through the Runtime Protection and Crypto miners Detection features.
- Always use the File Filtering to Filter Out the malicious executable files from the server.
- Always use the Updated Versions of the Oracle Web Logic Servers.



