CVE-2021-3156: Baron Samedit
Introduction
The researchers have discovered a heap overflow vulnerability, CVE-2021-3156 also known as Baron Samedit, in sudo it allows any unprivileged user to gain root privileges on Linux without requiring a password. Even a user “nobody” can get root access to a Linux server without a password. This CVE-2021-3156 vulnerability, introduced in 2011, was fixed in the latest version, sudo 9.5p2, and was released on January 26, 2021.
Some key findings of the vulnerability
- The researcher was able to develop 3 different exploits for this vulnerability and obtained root access on Ubuntu, Debian, and Fedora using various versions of sudo
- Other OS’s and distros are probably at risk
“Beyond Trust it strongly encourages Privilege Management for Unix & Linux (PMUL) customers to run pbrun instead of sudo. Pbrun is a command in PMUL that elevates the rights of a standard user so that they can run a command as a privileged user, but without needing a root account. Sudo is a basic tool that does a similar function, but with limited capabilities.”
Sudo is a powerful utility that’s included in almost everything, if not all Unix- and Linux-based OSes. It allows users to run programs with the security privileges of another user. The vulnerability itself has been hiding in plain sight for nearly 10 years. It was introduced in July 2011 (commit 8255ed69) and affects all legacy versions from 1.8.2 to 1.8.31p2 and all stable versions from 1.9.0 to 1.9.5p1 in their default configuration.Qualys security researchers have been able to independently verify the vulnerability and develop multiple variants of exploit and obtained full root privileges on Ubuntu 20.04 (Sudo 1.8.31), Debian 10 (Sudo 1.8.27), and Fedora 33 (Sudo 1.9.2). Other operating systems and distributions are also likely to be exploitable.
Understanding the Limitations of Sudo
While sudo has its merits and use cases, larger and more complex organizations will be familiar with its many limitations. For instance:
- Sudo does not provide efficient centralized administration and management
- Sudo does not have advanced reporting and analytics for a comprehensive audit trail
- Sudo is complex to manage in large enterprises
- Sudo does not provide centralized identity and group management
More Issues
The researcher Baron Samedit discovered more steps in the previous version of SUDO to produce the vulnerability:
- Executing sudo in “shell” mode (shell -c command)
- Using the sudoedit command with the options -s (MODE_SHELL flag) or -i (MODE_SHELL and MODE_LOGIN_SHELL flags)
- It’s possible to escape special characters in the command’s arguments using a backslash at the end.
A bug in the sudo code, related to the sudoedit command, permits to avoid the escape characters and overflow the heap-based buffer through a command-line argument that ends with a single backslash character.
Remediations
- Use pbrun, rather than sudo
- Upgrade to the latest version of sudo v1.9.5p2.
- Follow the technical advisories provided by your OS vendor
- Consider using BeyondTrustPrivelege Management for Unix & Linux to elevate privileges across your estate, instead of sudo.
- Delete sudo and sudoedit binaries from your Linux servers, if you are not using sudo.
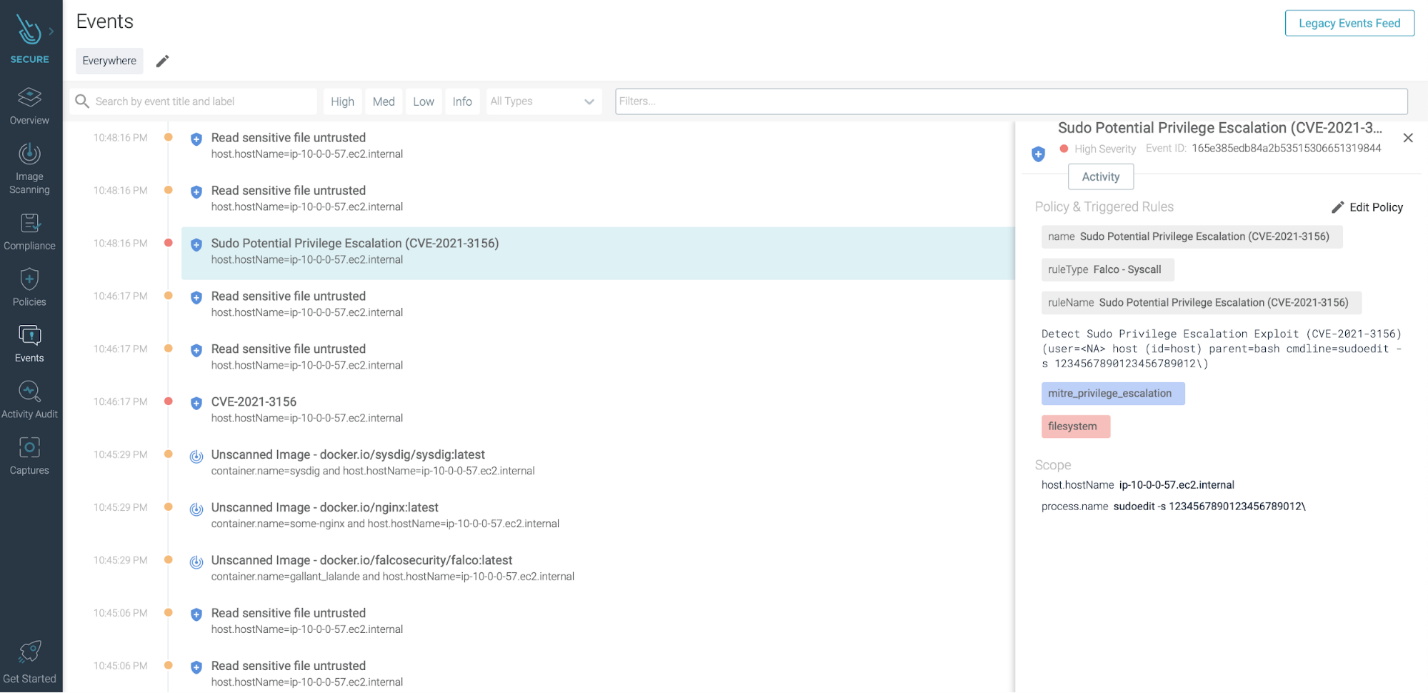
- Detection CVE-2021-3156 using Falco(If you cannot patch your systems immediately, you can detect and potentially prevent the attack) as shown in below figure: