Vulnerabilities Reported in Cisco VPN Routers
Cisco has rolled out fixes for multiple critical vulnerabilities in the web-based management interface of Small Business routers that could potentially allow an unauthenticated, remote attacker to execute arbitrary code as the root user on an affected device.
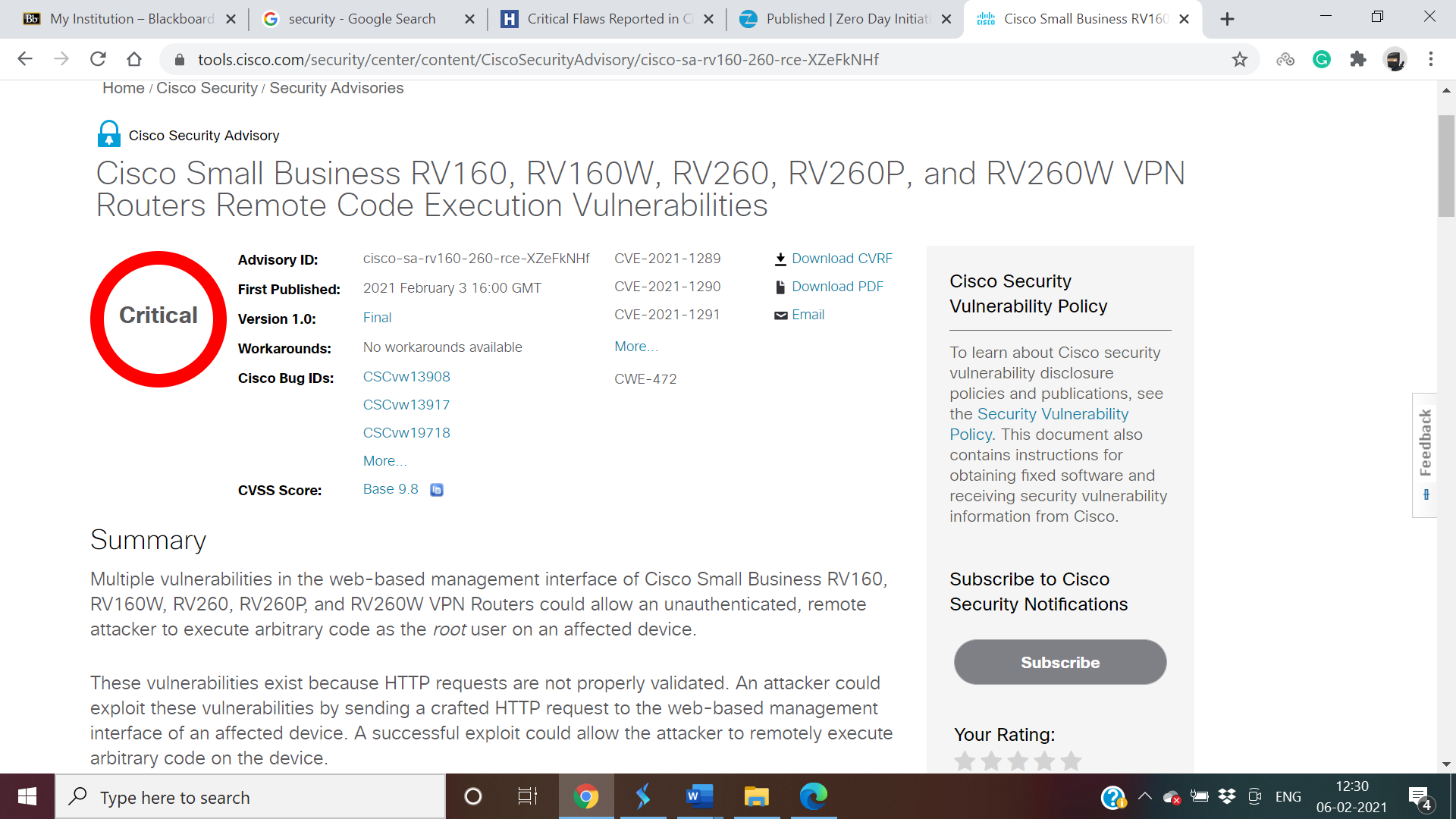
Affected CVEs
- CVE-2021-1289 through CVE-2021-1295 (CVSS score 9.8) — impact RV160, RV160W, RV260, RV260P, and RV260W VPN routers running a firmware release earlier than Release 1.0.01.02.
- CVE-2021-1296 and CVE-2021-1297affect the same set of VPN routers that could have made it possible for an adversary to overwrite arbitrary files on the vulnerable system.
- CVE-2021-1314 through CVE-2021-1318 in web-based interface of small business routers.
- CVE-2021-1319 through CVE-2021-1348 impact RV160, RV160W, RV260, RV260P, and RV260W VPN routers.
How the exploitations work
- All the nine security issues were reported to the networking equipment maker by security researcher Takeshi Shiomitsu, who has previously uncovered similar critical flawsin RV110W, RV130W, and RV215W . Routers that could be leveraged for remote code execution (RCE) attacks.
- CVE-2021-1289, CVE-2021-1290, CVE-2021-1291, CVE-2021-1292, CVE-2021-1293, CVE-2021-1294, and CVE-2021-1295are a result of improper validation of HTTP requests, allowing an attacker to craft a specially-crafted HTTP request to the web-based management interface and achieve RCE.
- CVE-2021-1296 and CVE-2021-1297are due to insufficient input validation, permitting an attacker to exploit these flaws using the web-based management interface to upload a file to a location that they should not have access to.
- Separately, another set of five glitches(CVE-2021-1314 through CVE-2021-1318) in the web-based management interface of Small Business RV016, RV042, RV042G, RV082, RV320, and RV325 routers could have granted an attacker the ability to inject arbitrary commands on the routers that are executed with root privileges.
- Cisco also addressed 30 additional vulnerabilities(CVE-2021-1319 through CVE-2021-1348), affecting the same set of products, that could allow an authenticated, remote attacker to execute arbitrary code and even cause a denial-of-service condition.
Affected Products
1. Vulnerable Products
These vulnerabilities affect the following Cisco Small Business Routers, if they are running a firmware earlier than Release 1.0.01.02:
- RV160 VPN Router
- RV160W Wireless-AC VPN Router
- RV260 VPN Router
- RV260P VPN Router with POE
- RV260W Wireless-AC VPN Router
2. Products Confirmed Not Vulnerable
Only products listed in the Vulnerable Products section of the advisory published by Cisco are known to be affected by these vulnerabilities.
Cisco has confirmed that these vulnerabilities do not affect the following Cisco products:
- RV340 Dual WAN Gigabit VPN Router
- RV340W Dual WAN Gigabit Wireless-AC VPN Router
- RV345 Dual WAN Gigabit VPN Router
- RV345P Dual WAN Gigabit POE VPN Router
Remedies:
- Cisco fixed these vulnerabilities in firmware releases 1.0.01.02 and later for Cisco RV160, RV160W, RV260, RV260P, and RV260W Routers.
- To download the updated fixed software from the Software Center on Cisco.com, do the following:
- Click Browse all.
- Choose Routers> Small Business Routers > Small Business RV Series Routers.
- Choose the appropriate router.
- Choose Small Business Router Firmware.
Choose a release from the left pane of the product p



