All Wi-Fi devices impacted by the latest Frag-Attacks vulnerabilities
All Wi-Fi devices including computers, smartphones, and smart devices are affected by a newly discovered Wi-Fi security vulnerabilities collectively known as Frag-Attacks (Fragmentation and Aggregation attacks).
The discovered vulnerabilities affect all modern security protocols of Wi-Fi, including the latest WPA3 (Wi-Fi Protected Access 3) specification. Even the original security protocol of Wi-Fi, called WEP (Wired Equivalent Privacy), is affected. Most of the design flaws have been part of Wi-Fi since its release in 1997.
Cause of the Flaw:
Three of these vulnerabilities are Wi-Fi 802.11 standard design flaws in the frame aggregation and frame fragmentation functionalities affecting most devices, while others are programming mistakes in Wi-Fi products.
Frame aggregation permits multiple smaller MSDU (MAC Service Data Units) or MPDUs (MAC Protocol Data Units) to be grouped together into a single frame, lowering the amount of overhead that is necessary for each individual frame. Certain devices accept plaintext aggregated frames that appear like handshake messages. An adversary can exploit this by sending an aggregated frame whose initials resembles a handshake message and whose other sub-frame carries the packet that the adversary desires to inject.
Frame fragmentation attacks are a type of computer security attack based on how the internet Protocol (IP) requires data to be transmitted and processed. In particular, it invokes IP fragmentation, a technique used to partition messages (the service data unit (SDU); usually a packet) from one layer of a network into multiple smaller payloads that could fit within the lower layer’s protocol data unit (PDU).
Certain Wi-Fi devices accept any unencrypted frame even if connected to a protected Wi-Fi network. This indicates the attacker doesn’t have to do something special to carry out this attack.
The threat actors who abuse these design and implementation flaws must be in the Wi-Fi range of targeted devices in order to steal sensitive user data and execute malicious code following successful exploitation, potentially leading to full device takeover.
AFFECTED CVES:
Frag-Attacks CVEs associated with Wi-Fi design flaws include:
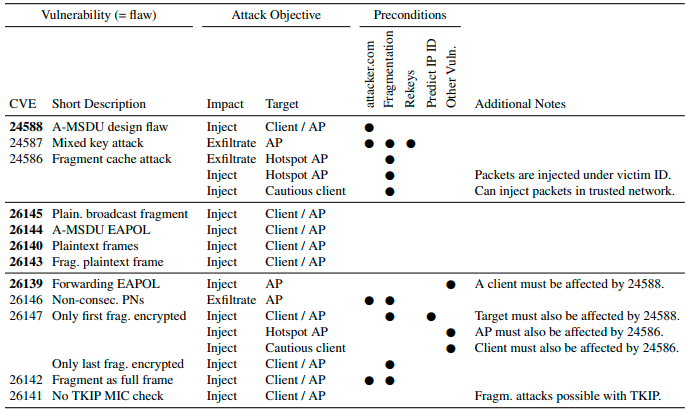
CVE-2020-24588: aggregation attack in which the device accepts non-SPP (Signalling and Payload Protected) A-MSDU (Aggregate MAC Service Data Unit) frames.
CVE-2020-24587: mixed key attack (reassembling fragments encrypted under different keys).
CVE-2020-24586: fragment cache attack (not clearing fragments from memory when (re)connecting to a network).
The CVEs assigned for Wi-Fi implementation vulnerabilities include:
CVE-2020-26145: Accepting plaintext broadcast fragments as full frames (in an encrypted network).
CVE-2020-26144: Accepting plaintext A-MSDU frames that start with an RFC1042 header with Ether Type EAPOL (Extensible Authentication Protocol over LAN) in an encrypted network.
CVE-2020-26140: Accepting plaintext data frames in a protected network.
CVE-2020-26143: Accepting fragmented plaintext data frames in a protected network.
Other implementation flaws discovered by Vanhoef include:
CVE-2020-26139: Forwarding EAPOL frames even though the sender is not yet authenticated (should only affect APs (Access Points)).
CVE-2020-26146: Reassembling encrypted fragments with non-consecutive packet numbers.
CVE-2020-26147: Reassembling mixed encrypted/plaintext fragments.
CVE-2020-26142: Processing fragmented frames as full frames.
CVE-2020-26141: Not verifying the TKIP (Temporal Key Integrity Protocol) MIC (Message Integrity Code) of fragmented frames.
Frag-Attacks Overview
Impact:
A bad actor can take advantage of these flaws to inject arbitrary network packets, intercept and ex-filtrate user information, launch denial-of-service attacks, and probably decrypt packets in WPA or WPA2 networks.
The design flaws are difficult to abuse as it requires user interaction or is only possible when using uncommon network settings.
But the programming mistakes behind some of the Frag-Attacks vulnerabilities are trivial to exploit and would allow attackers to abuse unpatched Wi-Fi products with ease.
Security researcher Mathy Vanhoef (New York University Abu Dhabi), who discovered the Frag-Attacks bugs stated that tests indicate that every Wi-Fi product is affected by at least one vulnerability and that most products are affected by several vulnerabilities.
Recommendations:
- According to the Industry Consortium for advancement of security on the internet (ICASI), vendors are already developing patches for their product to mitigate the Frag-Attacks bugs. Cisco Systems, HPE/Aruba Networks, Juniper Networks, Sierra Wireless, and Microsoft have already published Frag-Attacks security updates and advisories.
- The Wi-Fi Alliance stated that there is no evidence of the vulnerabilities being used against Wi-Fi users maliciously, and these issues can be mitigated through routine device updates that enable detection of suspect transmissions. The users are recommended to ensure that they have installed the latest updates from device manufacturers.
- For those users whose device vendor has not yet released security updates, can still mitigate some of the attacks. This can be done by ensuring that all websites and online services you visit use Hypertext Transfer Protocol Secure (HTTPS) protocol. Additionally, users can disable fragmentation, pairwise rekeys, and dynamic fragmentation in Wi-Fi 6 (802.11ax) devices.
An open-source tool to determine if access points and Wi-Fi clients on your network are affected by the Frag-Attacks flaws is also available on GitHub.



