Microsoft Patch Updates for June 2021
Lately, as a part of the June Patch, Microsoft has fixed 50 security flaws, amongst which five of them were rated critical, and the other 45 are classed as important in severity.
The following products were vulnerable to those security flaws:
- Microsoft Office
- .NET Core and Visual Studio
- Edge browser
- Windows Cryptographic Services
- SharePoint
- Outlook
- Excel
Among those issues, Microsoft has also published 6 zero-day vulnerabilities. Out of those 6 zero-day vulnerabilities, the security professionals at Microsoft have detected that certainly one of the issues is being used as a commercial exploit.
Cause of the Zero-Day Vulnerabilities:
Here is the list of all 6 zero-day vulnerabilities:-
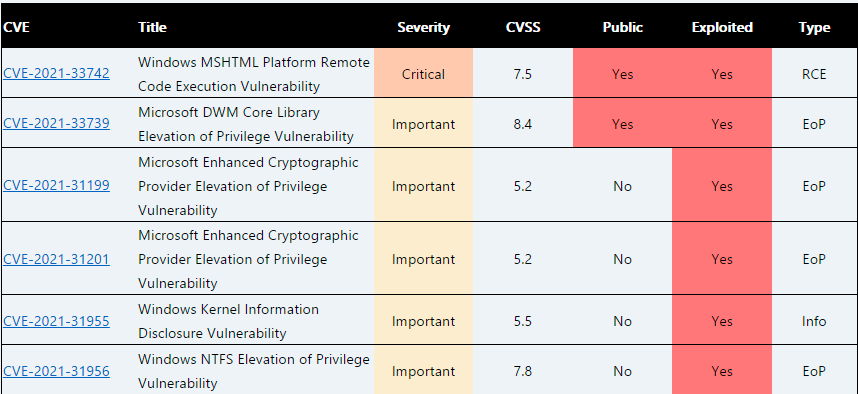
- CVE-2021-33742 (CVSS score: 7.5): This bug could allow an attacker to execute code on a target system if a user views specially crafted web content.
- CVE-2021-33739 (CVSS score: 8.4): This CVE describes a publicly disclosed and exploited vulnerability in Desktop Window Manager (DWM) Core that could lead to privilege escalation via the execution of a malicious script or executable by an authenticated user.
- CVE-2021-31199 (CVSS score: 5.2): This vulnerability is associated with the RCE vulnerability CVE-2021-28550, which was already fixed last month with the aid of the developers at Adobe.
- CVE-2021-31201 (CVSS score: 5.2): This vulnerability is also associated with the RCE vulnerability CVE-2021-28550, which was already fixed last month with the aid of the developers at Adobe.
- CVE-2021-31955 (CVSS score: 5.5): This Windows Kernel Information Disclosure could allow an attacker to read kernel memory via a user mode process via a vulnerable function call related to SuperFetch. The vulnerability in ntoskrnl.exe has been exploited in the wild.
- CVE-2021-31956 (CVSS score: 7.8): This vulnerability requires that an authenticated user execute code locally in order to exploit a heap-based buffer overflow in NTFS (ntfs.sys) that will allow for privilege escalation.
Impact of the Zero-Day Vulnerabilities:Out of the 6 Zero-day vulnerabilities, four vulnerabilities are privilege escalation flaws which suggest that hackers might have exploited these security flaws to take advantage of the elevated permissions on the affected systems as a part of the infection chain.
Moreover, the security professionals at Microsoft have asserted that the CVE-2021-33742 is an RCE vulnerability in the MSHTML factor, which is a part of the internet Explorer web browser.
While Shane Huntley, the Google analyst has claimed, that the CVE-2021-33742 is not only abused by using independent threat actors but also used by government hackers to attack targets in eastern Europe and the middle East.
Recommendations:
- Microsoft has strongly recommended all its users to put in all of the security updates straight away to protect the windows machines and avoid such security risks.
- The whole patch info for the overall list of vulnerabilities resolved, advisories, within the June 2021 Patch is present right here.
- Microsoft strongly endorsed installing these protection updates for all the windows customers to keep away from the security risk and protect the windows systems.



