CloudFlare CDNJS Bugs Can Lead to Widespread Supply-chain Attacks
A supply chain attack is a type of cyber attack that target’s organizations by focusing on weaker links in an organization’s supply chain. By targeting a weak point in a supply chain, a cyber attack may be more likely to succeed with attackers taking advantage of the trust that organizations may have in third-party vendors.
Critical bug discovered in Cloudflare CDNJS which could have led to supply-chain attacks. Web infrastructure and website security company Cloudflare last month fixed a critical vulnerability in its CDNJS library that’s used by 12.7% of all websites on the internet.
CDNJS is a free and open-source content delivery network(CDN) that serves about 4041 JavaScript and CSS libraries.
Ryotak (security researcher) who was discovered and reported this vulnerability to the company on April 6, 2021. The company stated that no evidence of wild exploitation of this issue.
“While this vulnerability could be exploited without any special skills, it could impact many websites,” security researcher said.
Impact’s by this attack:
The issue could have allowed attacker to execute arbitrary commands in the CDNJS library update server which could have resulted in a complete compromise.
The vulnerability functions by publishing packages to Cloudflare’s CDNJS using GitHub and npm, using it to trigger a path transversal vulnerability, and ultimately trick the server into executing arbitrary code, thus achieving remote code execution.
The security researcher (Ryotak) had discovered that arbitrary code could be executed after the threat actor performs path traversal from the .tgz file that is published to npm and then overwriting the script which is executed regularly on the server.
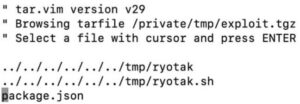
The goal of the attack is to infect all the system by malicious package. The CDNJS library update server for publishing a new version package to the repository, In the process of copying the contents of the malicious package into a regularly executed script file hosted on the server, thereby gaining arbitrary code execution.
Recommendations to protect against supply chain attacks(By Microsoft):
- Deploy strong code integrity policies to allow only authorized apps to
- Use endpoint detection and response solutions that can automatically detect and remediate suspicious
- Maintain a highly secure build and update infrastructure.
- Build secure software updaters as part of the software development
- Develop an incident response process for supply chain



