Low-Risk iOS Wi-Fi Naming Bug Can Hack iPhones Remotely
The Wi-Fi network name bug, this bug was found to completely disable an iPhone’s networking functionality had remote code execution (RCE) capabilities and was silently fixed by Apple earlier this year.
The Dos (denial-of-service) vulnerability, it came to light last month. On the latest iPhone connected to a wireless access point, which has a percent sign in its name, such as “% p% s% s% s”, due to the way iOS handles the string format associated with SSID input. Triggered a crash% s% n.
All iOS versions since iOS 14.0 and prior to iOS 14.3 were found to be vulnerable to RCE variants, and Apple applied a “silent” patch to the issue in January 2021 as part of it did iOS 14.4 update. The defect has not been assigned a CVE identifier.
Impacts from this bug:
- The wifi bug completely disable an iphone’s networking
- Remote code execution (RCE) can be their by this
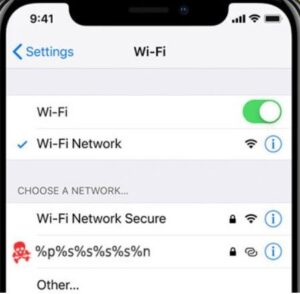
Researchers from mobile security automation firm ZecOps found that the same bug could be exploited to achieve remote code execution (RCE) on targeted devices by simply attaching the string pattern “%@” to the Wi-Fi hotspot’s name.
ZecOps nicknamed this issue “WiFi daemon “This is also a zero-click vulnerability in that it allows an attacker to infect a device without user intervention. Automatically join the Wi-Fi network Enabled.
Recommendations:
- Apple Will push patches Bugs in the iOS 14.7 update are currently available to developers and public beta
- This Issue is remediable by resetting the network settings (Settings > General > Reset > Reset Network Settings).
- It’s highly recommended that iPhone and iPad users update their devices to the latest iOS version to mitigate the risk associated with the vulnerability.



