The Prometheus TDS malware service using to spread wide range of cyber attack
Introduction
Prometheus TDS is an underground service that distributes malicious files and redirects visitors to phishing and malicious sites. This service is made up of the Prometheus TDS administrative panel, in which an attacker configures the necessary parameters for a malicious campaign: downloading malicious files, and configuring restrictions on users’ geolocation, browser version, and operating system.
Prometheus TDS uses third-party infected websites that act as a middleman between the attacker’s administrative panel and the user. It should also be mentioned that the list of compromised websites is manually added by the malware campaign’s operators.
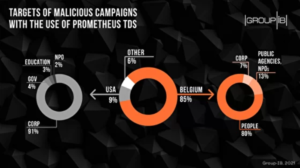
Multiple cybercriminal groups are leveraging a malware-as-a-service (MaaS) solution to distribute a wide range of malicious software distribution campaigns that result in the deployment of payloads such as Campo Loader, Hancitor, IcedID, QBot, Buer Loader, and SocGholish against individuals in Belgium as well as government agencies, companies, and corporations in the U.S.
Dubbed “Prometheus TDS” (Traffic Direction System) and available for sale on underground platforms for $250 a month since August 2020, the service is designed to distribute malware-laced Word and Excel documents and divert users to phishing and malicious sites, according to a Group-IB report shared with The Hacker News.
Impact
More than three thousand email addresses targeted in the first phase of malicious campaigns in which Prometheus TDS was used to send malicious emails. And these email addresses are said to have been singled out via malicious campaigns in which Prometheus TDS was used to send malicious emails, with banking and finance, retail, energy and mining, cybersecurity, healthcare, IT, and insurance emerging the prominent verticals targeted by the attacks.
Attack scheme using Prometheus TDS
The service is also known to employ third-party infected websites that are manually added by the campaign operator and act as an intermediary between the attacker’s admin panel and the user. To achieve this, Prometheus.Backdoor“Is uploaded to the compromised website and collects and sends back data about the victim, which determines whether to send the payload to the user or redirect it to the specified URL.
1) An HTML file that redirects the user to a compromised site on which Prometheus. Backdoor is installed.
2) A link to a web shell that redirects users to a specified URL, in this case to one of the addresses used by Prometheus TDS.
3) A link to a Google Doc containing the URL redirecting users to a malicious link.
4) The user opens the attachment or follows the link and is redirected to the Prometheus.Backdoor URL. Prometheus.Backdoor collects the available data on the user (IP address, user agent, referrer header, time zone, language data).
5) The data collected is sent to the Prometheus TDS admin panel. This admin panel then decides whether to instruct the backdoor to send a malicious file to the users and/or to redirect them to the specified URL.
Recommendation:
1) Ensure that all security updates and patches are installed.
2) Avoid on clicking suspicious links and emails.
3) Avoid suspicious websites.
4) Properly see from where the mail has come and see the URL properly before clicking.
5) Review software carefully before downloading.
6) Leverage strong, unique passwords.
7) Turn on your firewall.
8) Install an anti-virus/anti-malware software.



