Mozi IoT Botnet Now Also Targets Netgear, Huawei, and ZTE Network Gateways
Introduction
The Mozi Botnet is a botnet targeting IoT devices. In September 2019, 71% of the botnet was located in China. In March, it jumped to 81%. The botnet was first discovered near the end of 2019 and is currently active. Similar to the Mirai botnet, it targets consumer routers via security vulnerabilities and shell injections. It uses peer to peer technology to spread infectious code to new hosts.
The Mozi botnet is comprised of nodes that utilize a distributed hash table (DHT) for communication, similar to the code used by IoT Reaper and Hajime. These nodes also host the Mozi. m and Mozi. a malware binary files, passed during the compromise of new hosts, on a randomly chosen port.
Mozi, a peer-to-peer (P2P) botnet known to target IoT devices, has new capabilities that enable persistence with network gateways manufactured by Netgear, Huawei, and ZTE, according to new findings. I got it.
An IBM X-Force analysis published in September 2020 noted that Mozi accounted for nearly 90% of the observed IoT network traffic from October 2019 through June 2020, indicating that threat actors are increasingly taking advantage of the expanding attack surface offered by IoT devices. In a separate investigation released last month, Elastic Security Intelligence and Analytics Team found that at least 24 countries have been targeted to date, with Bulgaria and India leading the pack.
What’s more, Mozi has been upgraded to support new commands that enable the malware to hijack HTTP sessions and carry out DNS spoofing so as to redirect traffic to an attacker-controlled domain.
How it works
Mozi is a peer-to-peer (P2P) botnet that uses a BitTorrent-like network to infect IoT devices such as network gateways and digital video records (DVRs). It works by exploiting weak telnet passwords and nearly a dozen unpatched IoT vulnerabilities and it’s been used to conduct distributed denial-of-service (DDoS) attacks, data exfiltration, and command or payload execution.
Network gateways are a particularly juicy target for adversaries because they are ideal as initial access points to corporate networks. Adversaries can search the internet for vulnerable devices via scanning tools like Shodan, infect them, perform reconnaissance, and then move laterally to compromise higher value targets—including information systems and critical industrial control system (ICS) devices in the operational technology (OT) networks.
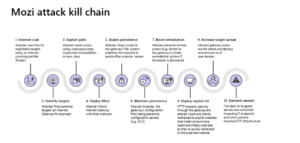
Fig:Attack flow for Mozi botnet
Impact
By infecting routers, they can perform man-in-the-middle (MITM) attacks—via HTTP hijacking and DNS spoofing—to compromise endpoints and deploy ransomware or cause safety incidents in OT facilities.
Detailing new capabilities of the Mozi IoT botnet, which recruits IoT devices to conduct distributed denial-of-service (DDoS) attacks, data exfiltration, and command or payload execution.
Recommendation
Businesses and individuals that are using impacted network gateways (Netgear, Huawei, and ZTE) should take the following steps immediately to ensure they are resistant to the attacks described in this blog:
- Ensure all passwords used on the device are created using strong password best practices.
- Ensure devices are patched and up-to-date.
- To increase chances of survival the malware prevents remote access by blocking the following TCP ports:
- 23—Telnet
- 2323—Telnet alternate port
- 7547—Tr-069 port
- 35000—Tr-069 port on Netgear devices
- 50023—Management port on Huawei devices
- 58000—Unknown usage



