Mēris botnet attacks Russia’s Yandex with 22 million RPS DDoS attacks
Introduction
Yandex N.V. is a Russian multinational corporation providing over 70 Internet-related products and services, including transportation, search and information services, e-commerce, navigation, mobile applications, and online advertising.
The firm is the largest technology company in Russia and the second largest search engine on the Internet in Russian, with a market share of over 42%. It also has the largest market share of any search engine from Europe and the Commonwealth of Independent States and is the 5th largest search engine worldwide after Google, Baidu, Bing, and Yahoo!.
What Happened?
Russian internet giant Yandex has been the target of a record decentralized denial of service (DDoS) attack by a new botnet called Mēris.
In August and September was the largest known distributed denial-of-service (DDoS) attack in the history of the internet, the company said on Thursday.
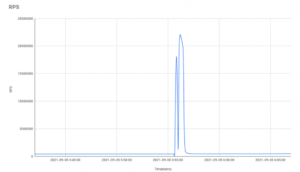
Botnets made millions of HTTP requests on the company’s Web before peaking at 21.8 million requests per second (RPS) before diminishing recent botnet-based attacks revealed last month. It is believed to have destroyed the infrastructure. Bombardment An unnamed Cloud flare customer in the financial industry with 17.2 million RPS.
The DDoS attack, in which hackers try to flood a network with unusually high volumes of data traffic in order to paralyse it when it can no longer cope with the scale of data requested, began in August and reached a record level on Sept. 5.
Mēris botnet
Mēris, which means “Plague” in the Latvian language. It seems appropriate and relatively close to Mirai in terms of pronunciation.
Specific features of Mēris botnet:
- Socks4 proxy at the affected device
- Use of HTTp pipelining (http/1.1) technique for DDoS attacks (confirmed)
- Making the DDoS attacks themselves RPS-based (confirmed)
- Open port 5678 (confirmed)
Impact
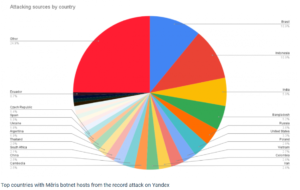
The DDoS attacks leveraged a technique called HTTP pipelining that allows a client (i.e., a web browser) to open a connection to the server and make multiple requests without waiting for each response. The malicious traffic originated from over 250,000 infected hosts, primarily network devices from Mikrotik, with evidence pointing to a spectrum of Router OS versions that have been weaponized by exploiting as-yet-unknown vulnerabilities.
Although Mikrotik uses UDP for its standard service on port 5678, an open TCP port is detected on compromised devices. This kind of disguise might be one of the reasons devices got hacked unnoticed by their owners.
Recommendation:
- Buy More Bandwidth:- The most basic step you can take to make your VPS Hosting infrastructure “DDoS resistant” is to ensure that organization have enough bandwidth to handle spikes in traffic that may be caused by malicious activity.
- Build Redundancy into organization infrastructure:- To make it as hard as possible for an attacker to successfully launch a DDoS attack against the servers, make sure organization spread them across multiple data centres with a good load balancing system to distribute traffic between them.
- Configure your Network Hardware Against DDoS Attack:- There are a number of simple hardware configuration changes can take to help prevent a DDoS attack.
- Deploy Anti-DDoS Hardware and Software Modules:- The servers should be protected by network firewalls and more specialized web application firewalls, and should probably use load balancers as well. Many hardware vendors now include software protection against DDoS protocol attacks such as SYN flood attacks.
- Deploy A DDoS Protection Appliance:- Many security vendors including NetScout Arbor, Fortinet, Check Point, Cisco and Radware offer appliances that sit in front of network firewalls and are designed to block DDoS attacks before they can take effect.
- Protect the DNS servers:- Don’t forget that a malicious actor may be able to bring your web servers offline by DDoSing your DNS servers. For that reason it is important that your DNS servers have redundancy, and placing them in different data centers behind load balancers is also a good idea.



