Twitch Suffers Massive 125GB Data and Source Code Leak Due to Server Misconfiguration
Introduction
Twitch is an American video live streaming service that focuses on video game live streaming, including broadcasts of esports competitions. Twitch is the top game-streaming site, with an average viewership of 2.5 million people at any given time. It has 7 million creators who stream each month, with a total audience of over 30 million per day. Last year, the service says, people watched over 1 trillion minutes of content.
What happened?
Twitch, Amazon’s incredibly popular game streaming service, has apparently been the target of a massive hacking operation that includes the system’s source code, user data (including payouts ), and plans for an unreleased digital store due to Server Misconfiguration.
“Server Misconfiguration attacks exploit configuration weaknesses found in web servers and application servers. Many servers come with unnecessary default and sample files, including applications, configuration files, scripts, and web pages.”
The Amazon-owned assistance said it is “performing with urgency to comprehend the extent of this,” incorporating the details was uncovered “owing to a mistake in a Twitch server configuration change that was subsequently accessed by a malicious third party.”
An anonymous post on the 4chan message board released a 125GB torrent with the data, which the hackers claim is the entirety of Twitch’s code and history. Twitch confirmed the leak in a tweet.
The hackers claim that the leaked data includes
- The entirety of Twitch’s source code with commit history “going back to its early beginnings”
- Proprietary software development kits and internal AWS services used by Twitch
- An unreleased Steam competitor, codenamed Vapor, from Amazon Game Studios
- Information on other Twitch properties like IGDB and CurseForge
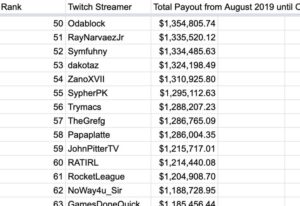
- Creator revenue reports from 2019 to 2021
- Mobile, desktop and console Twitch clients, and
- Cache of internal “red teaming” tools designed to improve security
While personal information like creator payments is included, this initial leak doesn’t appear to include passwords, addresses, or email accounts of Twitch users. Instead, the leaker appears to have focused on sharing Twitch’s own company tools and information, rather than code that would include personal accounts.
Recommendation
For User’s
- The users must take necessary actions as their data could be abused by attackers to take over user accounts and perform fraudulent transactions.
- As a conservative measure, the users can change the password to their compromised account, as well as for any other account for which they use the same password.
- It is recommended to enable 2FA (Two-Factor Authentication) for more security.
For Organization
Here are a few steps to take in response to a breach:
1) Identify the Source AND Extent of the Breach: The first thing to do is to identify the source and extent of the breach so that organization can address it ASAP. Ideally, organization should have intrusion detection and/or prevention systems (IDS and IPS) in place that can automatically log such security events.
2) Alert Organization Breach Task Force and Address the Breach ASAP: Organization should have a team of IT personnel in business who are tasked with handling emergencies such as data breaches. Gather this breach task force so they can address the breach as soon as possible.
3) Test Organization Security Fix: Immediately after implanting a short-term security fix to prevent further access to Organization data, test the fix as thoroughly as Organization can to make sure the attacker cannot use the same method to attack again.
4) Inform the Authorities and ALL Affected Customers: Once organization have a fix in place and have made sure it will work, contact the authorities and reach out to any customers that may have been affected by the breach. Federal authorities may be able to provide with crucial instructions for complying with post-breach regulatory standards for industry.
5) Prepare for Post-Breach Cleanup and Damage Control: A data breach can have severe impacts well after the initial breach has been “resolved.” There is often a loss of consumer confidence after a breach, and restoring the public’s trust in business can be difficult.



