Microsoft fends off a record of 2.4 Tbps DDoS attacks targeting Azure customers
Introduction
Microsoft Azure is a cloud computing service from Microsoft. Azure offers a range of software as a service (SaaS), platform as a service (PaaS) and infrastructure as a service (IaaS) options for deploying applications and services on Microsoft-managed data center infrastructure.
The Azure cloud platform has more than 200 products and cloud services which are being designed to bring new solutions to life—to solve today’s challenges and create the future. Build, run and manage applications across multiple clouds, on-premises and at the edge, with the tools and frameworks of choice.
On Monday, Microsoft cloud platform mitigated a 2.4 Tbps decentralized denial of service (DDoS) attack targeting unnamed customers in Europe in the last week of August. 2.3Tbps attack Suspended by Amazon Web Services in February 2020.
A DDoS attack essentially tries to down a website or internet service by bombarding the system with a flood of data traffic. To do so, the hacker can sometimes harness botnets, or armies of malware-infected computers, to generate the traffic.
This is 140 percent higher 1Tbps attack in 2020 It’s higher than any network volume event previously detected in Azure, “said Amir Dahan, Senior Program Manager at Azure Networking
What happened ?
The attack traffic originated from approximately 70,000 sources and from multiple countries in the Asia-Pacific region, such as Malaysia, Vietnam, Taiwan, Japan, and China, as well as from the United States. The attack vector was a UDP reflection spanning more than 10 minutes with very short-lived bursts, each ramping up in seconds to terabit volumes. In total, we monitored three main peaks, the first at 2.4 Tbps, the second at 0.55 Tbps, and the third at 1.7 Tbps.
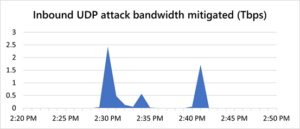
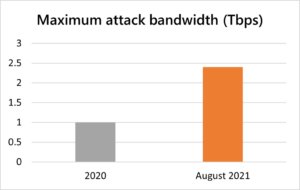
Recommendation :
It is recommended to use Azure DDoS Protection (Azure DDoS Protection Standard provides enhanced DDoS mitigation features to defend against DDoS attacks. It is automatically tuned to protect all public IP addresses in virtual networks.)
- Buy More Bandwidth:- The most basic step organization can take to make a VPS Hosting infrastructure “DDoS resistant” is to ensure that organization have enough bandwidth to handle spikes in traffic that may be caused by malicious activity.
- Build Redundancy into organization infrastructure:- To make it as hard as possible for an attacker to successfully launch a DDoS attack against the servers, make sure organization spread them across multiple data centers with a good load balancing system to distribute traffic between them.
- Configure the Network Hardware Against DDoS Attack:- There are a number of simple hardware configuration changes can take to help prevent a DDoS attack.
- Deploy Anti-DDoS Hardware and Software Modules (Azure DDoS Protection):- The servers should be protected by network firewalls and more specialized web application firewalls, and should probably use load balancers as well. Many hardware vendors now include software protection against DDoS protocol attacks such as SYN flood attacks.
- Deploy A DDoS Protection Appliance:- Many security vendors including NetScout Arbor, Fortinet, Check Point, Cisco and Radware offer appliances that sit in front of network firewalls and are designed to block DDoS attacks before they can take effect.
- Protect the DNS servers:- Don’t forget that a malicious actor may be able to bring the web servers offline by DDoSing to DNS servers. For that reason it is important that the DNS servers have redundancy, and placing them in different data centers behind load balancers is also a good idea.



