Researchers Warn Iranian Users of Extensive Smishing Campaigns
INTRODUCTION
Attackers use socially engineered SMS messages & malware to compromise 10s of 1,000s of devices & drain user bank accounts.
They are impersonating the Iranian Govt. in a widespread SMS phishing campaign that is defrauding 1,000s of Android users by installing malware on their devices that can steal their credit card data & take money from financial accounts.
The cybersecurity firm said it uncovered several hundred different phishing Android applications that masqueraded as:
- Device tracking apps
- Iranian banks
- Dating apps
- Shopping sites
- Cryptocurrency exchanges
- Government-related services
PHISHING CAMPAIGN
The attacker send’s the phishing message and in many cases, it’s a message from an electronic judicial notification system that notifies the victim that a new complaint was opened against them. The seriousness of such an issue might explain why the campaign has gone viral. When official government messages are involved, most citizens blindly trust and clicking on the links.
The link from the SMS leads to a phishing site which looks identically an official government site. The user is notified of the complaint filed against them, and personal information is requested in order to proceed to the electronic system and avoid visiting the offline branch due to COVID limitations.
The victim is redirected to a page to download a malicious .apk file. Once installed, the Android application shows a fake login page. It also notifies the victim that they need to pay a fee to proceed. It is only a small amount (20,000, or sometimes 50,000 Iranian Rials – around $1), which reduces the suspicion and makes the operation look more legitimate.
After entering the details, the victim is redirected to a payment page. Similar to most phishing pages, after credit card data is submitted the site shows a “payment error” message, but the money is already gone.
Data collected by attackers may include:
- Personal information
- Contact numbers
- SMS Messages
- Credit card details
- national identity number
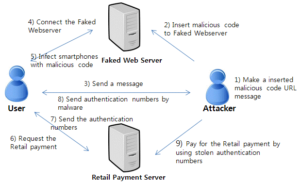
These Android backdoor capabilities include:
- SMS stealing: After the installation of the fake app, all the victim’s SMS messages are uploaded to the attacker’s server.
- Hiding to maintain persistence: After taking the credit card the information is sent to the attacker, the application automatically hide its icon, making it challenging for the victim to control or uninstall the app.
- Bypass 2FA: Having access to both the credit card details and SMS on the victim’s device, the attackers can precede with unauthorized withdrawals from the victim’s bank accounts, hijacking the 2FA authentication like one-time password.
- Botnet Capabilities: The malware can communicate with the C&C server via Firebase Cloud Messaging, it allows the attacker to execute additional commands on the victim’s device, such as stealing contacts and sending SMS messages.
- Wormability: The app can send SMS messages to a list of potential victims, using a custom message and a list of phone numbers both retrieved from the C&C server.
Here’s the tip for individuals to avoid Smishing attacks:
- Don’t click on any link or call any number received from an unknown person.
- Be wary of unsolicited SMS that claims to be from reputable organizations, such as banks, credit card firms, etc.
- Don’t follow any instruction that encourages you urgently to visit their website or call a number to update or verify your account.
- Don’t provide your personal information, such as username, bank account, and other codes.
- Don’t respond to text messages that ask for your four-digit code or online banking password.
- Don’t click on any link provided in a text message, instead, use a trusted browser to access online banking through your bank’s website.
- Contact your bank immediately if you mistakenly respond to a Smishing message.
- Always check the last number code of your bank account and credit card with the numbers you have received in a text message.



