Zloader malware exploits Microsoft’s digital signature verification
INTRODUCTION
A new malware campaign is taking advantage of vulnerability in the way Microsoft digitally signs a specific file type. As described by cyber threat intelligence firm Check Point Research, an attack using the infamous Zloader banking malware aims to steal account credentials and other private data and has already infected 2,170 unique machines that downloaded the malicious DLL file involved in the exploit. Most of the victims are in the US and Canada, but the campaign has hit more than 100 other countries, including India, Germany, Russia and the UK.
Zloader Banking Malware’s Severity
The new banking malware has already affected around 2,100 people in different countries. The majority of the victims are in the United States, India, and Canada. As of the moment, CPR said they see the malicious campaign in around 111 countries. When Zloader was first discovered, malicious actors were using it to exploit Trojan viruses to steal banking credentials.
Because of this, it was closely connected to other ransomware models. On the other hand, Check Point Research works using legitimate remote management software called Atera.
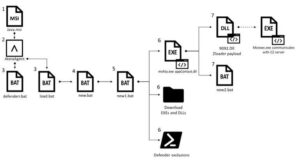
Infection Chain
The campaign begins by installing the Atera remote monitoring and management software on a target machine. A legitimate remote tool used by IT professionals, Atera’s product offers a free 30-day trial for new users, an option the attackers are likely using to gain the initial access. Once the product is installed, the operators have full control of the system to run scripts and upload or download files.
In the next phase, the attackers download and run two malicious files, one of which is designed to disable certain protections in Windows Defender and the other to load the rest of the malware. From there, a script runs an executable file, and that’s where the operators exploit a hole in Microsoft’s signature verification.
A malicious script is run using a file called appContast.dll, which points to a legitimate Windows system file called AppResolver.dll as the source. Upon analysis, Check Point discovered that this file is signed by Microsoft with a valid signature. Despite that digital signature, the malware is able to append a script to this file to carry out the attack. This is because the operators were able to append data to the signature section of the file without changing the validity of the signature itself.
Microsoft E-Signature Verification’s Flaws
CPR’s security experts confirmed three vulnerabilities in Microsoft’s e-signature verification tool that are being exploited by the new banking malware.
These include the following:
- CVE-2020-1599
- CVE-2013-3900
- CVE-2012-0151
Microsoft explained that updates to fix these flaws were already released. However, they are not installed by default. This means that consumers who will not download the updates manually will certainly be affected by the new computer virus.
Safety Tips:
- Apply Microsoft’s update for strict Authenticode verification. It is not applied by default.
- Do not install programs from unknown sources or sites.
- Do not press on links or open unfamiliar attachments that you get by mail.



