“WhisperGate Malware” targeting Microsoft Windows In Ukraine
Microsoft’s security experts said on January 22nd that they have discovered evidence of a new harmful malware operation called “WhisperGate” that was targeting Ukrainian government, non-profit, and IT organizations. This comes as geopolitical tensions between Ukraine and Russia are heating up.
The malware is disguised as ransomware but, if activated by the attacker, would render the infected computer system inoperable. Tom Burt, corporate vice president of customer security and trust at Microsoft, said, adding the intrusions were aimed at government agencies that provide critical executive branch or emergency response functions.
This month, researchers have discovered “strategic parallels” between wiper malware and the NotPetya malware that was unleashed on Ukraine’s infrastructure and elsewhere in 2017. Windows stumbled onto the malware, aptly titled “WhisperGate,” in late January. The company claimed it had witnessed a disruptive cyber operation aimed against the nation’s government, non-profits, and information technology firms.
The Malware Attack Process
With no apparent technique or method similarities with other previously known organizations, the computer giant, which discovered the malware for the first time on January 13, attributed the attacks to an emerging threat cluster designated “DEV-0586.” The malware was identified on dozens of affected systems, and the investigation is expected to uncover more as time goes on.
The WhisperGate infection chain is fashioned as a multi-stage process that first downloads a payload that wipes the master boot record (MBR), then downloads a malicious DLL file hosted on a Discord server, which drops and executes another wiper payload that irrevocably destroys files by overwriting their content with fixed data on the infected hosts.
According to the Microsoft Threat Intelligence Center (MSTIC) and Microsoft Digital Security Unit (DSU), the assault chain is a two-stage procedure that comprises—
The first step involves:
Overwriting the Master Boot Record (MBR)—the first sector of any hard disc that identifies where the operating system is located on the disc so that it can be loaded into a computer’s RAM—on a victim’s system will display a fake ransom note urging the target to pay an amount of $10,000 to a bitcoin wallet
The malware sits in many working locations, including C:\PerfLogs, C:\ProgramData, C:\, and C:\temp, and is commonly titled stage1.exe. In the reported incursions, the malware runs through Impacket, a publicly known feature typically exploited by threat actors for lateral movement and execution.
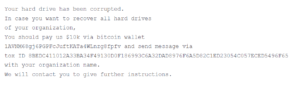
Consistent behavior with what MSTIC has seen from cybercriminals using ransomware includes:
- Payloads for ransomware are generally tailored to the specifics of the victim. In this example, the same ransom payload was discovered on many victims.
- Virtually all ransomware encrypts the contents of files on the filesystem. The malware in this situation overwrites the MBR with no means for recovery.
- Explicit payment amounts and cryptocurrency wallet addresses are rarely provided in recent criminal ransom letters, but were given by DEV-0586. The same Bitcoin wallet address has been discovered throughout all the DEV-0586 invasions, and at the time of research, the sole activity was a minor payment on January 14.
- Only a Tox ID, an identification for use with the Tox encrypted messaging system, is often used as a means of communication. Typically, there are websites with support forums or several channels of communication (including email) to make it easier for the victim to effectively establish contact.
- For the most part, criminal ransom letters advise their victims to transmit a unique ID number to the assailants whenever they communicate with them. This is a critical phase of the process where the custom ID is mapped on the backend of the ransomware operation to a victim-specific decryption key. The ransom note in this scenario does not include a special ID.
The second step involves:
After retrieving the malware from a Discord channel, this application overwrites all 189 file extensions with a predetermined number of 0xCC bytes and renames each one with an apparently random four-byte extension. This is the second stage of the infection process.
Stage2.exe is a downloader for harmful file-corrupting malware. When stage2.exe is run, it downloads the next stage of malware from a Discord channel that has been hardcoded into the downloader itself. The next step of malware is best defined as a corruptor of files that causes harm. Once performed in memory, the corrupter locates files in particular folders on the system with one of the following hardcoded file extensions:

The findings come a week after roughly 80 Ukrainian government agencies’ websites were defaced, with the Ukrainian intelligence agencies confirming that the twin incidents are part of a wave of malicious activities targeting their critical infrastructure, while also noting that the attacks leveraged the recently disclosed Log4j vulnerabilities to gain access to some of the compromised systems.
Remediation Actions
Detectors for this type of behavior are now being developed and implemented by the MSTIC and Microsoft security teams, respectively. However, the malware known as WhisperGate (such as DoS: Win32/WhisperGate.A!dha) may now be detected on all Windows systems, whether they are in the cloud or on-premises, by Microsoft Defender Antivirus and Microsoft Defender for Endpoint. Security measures like those listed below can help limit the risks:
- Use the accompanying indications of compromise to research whether they exist in your environment and assess it for potential incursion.
- Review all authentication activity for remote access infrastructure, with a special focus on accounts set up with single factor authentication, to check validity and examine any abnormal behavior.
- Secure all remote connections by enabling multifactor authentication (MFA) to prevent credentials from being hacked. The use of password-less solutions such as Microsoft Authenticator, which does not require a password to access an account, is strongly recommended by Microsoft.
- Prevent MBR/VBR modifications by turning on Microsoft Defender for Endpoint’s Controlled Folder Access (CFA).



