Earth Lusca a Financially Motivated Attack on Government and Private Organization
INTRODUCTION
Earth Lusca is tracked as a sophisticated or elusive threat actor. Its aim is to target government and private organizations world- wide for financial purpose via spear-phishing and watering hole attack.
According to the security firms, the group is ready to reap the monetary profits that are safely kept by the government and other organization for other purposes. The list of its victim includes:
- Government Institution
- Educational Institution
- Religious Movements
- Pro-democracy and Human Rights Organization in Hong Kong
- COVID-19 Research Organization and
- Media also
Trend Micro researchers guess that the group operates through Winnti umbrella which is linked to China. In 2013 Kaspersky first spotted the Winnti group but the group was active since 2007.
Earth Lusca Infrastructure
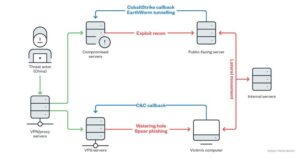
The Earth Lusca’s infrastructure is grouped into two clusters:
Virtual Private Servers: It was employed in watering hole and spear-phishing attack.
Glass-Fish Server: It is used to perform scanning for vulnerabilities in public facing server and builds traffic tunnels with the target’s network. Both cluster served as a Command and Control (C&C) server.
It is possible that the group uses cluster for diversion of security staff focusing in wrong part of the network.
Social Engineering and Vulnerability Exploitation Techniques
The group has three primary attack vectors, out of which two involves social engineering. The social engineering technique is used for spear fishing email and watering hole websites.
It has seen that Earth Lusca sending spear fishing emails containing malicious links to one of their target – a media company. These links contain files that disguised the user by showing that it would be of our interest. The user eventually downloads the file containing either a malicious LNK file or an executable- eventually leading to a Cobalt Strike loader.
In addition to spear fishing emails, it also makes use of waterhole websites – they used to set up a fake web pages copied from original websites and then inject malicious JavaScript code inside them. After that these link are send to their victims.
The third attack vector is the exploitation of vulnerabilities that exist in the public facing application such as Microsoft Exchange ProxyShell and Oracle GlassFish for its target. Once these are accomplished, now Earth Lusca is ready to perform its post-Exploitation routine that includes installation of tools such as Cobalt Strike.
How these kinds of attacks happen?
The experts believe that under the Winnti Umbrella there are several APT groups, including Winnti, PlayfullDragon, APT47, Wicked Panda, Group 72 and many more.
These groups target the organization in various industries, including the aviation, gaming, pharmaceuticals, technology, telecoms and software development industries. These attacks take place through the infected chain of the spear fishing emails. The chain leads to deploy the variety of malware such as Doremon, Shadow Pad, and Winnti and web shell like AntSword and Behinder. The group preferred to uses the Cobalt Strike due to its wide range of post-exploitation capabilities.
Remedies
The best way to keep away from these kinds of attacks is
- Avoid clicking on suspicious email/website
- Update the systems on regular basis
- Monitor the network and web traffic
By doing so we can minimize the impact or even stop an Earth Lusca attack



