Daxin Malware : New Espionage Backdoor
Daxin is a type of Backdoor which is developed with the goal of cyberespionage. According to Cyber Security and Infrastructure Security Agency (CISA), “Daxin malware is a highly sophisticated rootkit backdoor with complex, stealthy command-and-control (C2) functionality that enabled remote actors to communicate with secured devices not connected directly to the internet. Daxin appears to be optimized for use against hardened targets, allowing the actors to deeply burrow into targeted networks & exfiltrate data without raising suspicions”.
In current research by Symantec Threat hunter team, they found a highly sophisticated piece of malware which is being used by Chinese-linked threat actors. After thorough analysis they find out that the malware appears to be used in a long-running cyberespionage campaign against some selective governments & other critical infrastructure targets.
Technical Overview of Daxin: –
Daxin comes in the form of Windows kernel driver which is a very rare format for malware nowadays. Its features resemble with Regin, an advanced espionage tool which is discovered by Symantec in 2014. It implements advanced communications mechanism, which provides this malware a high degree of stealth & also allow the attackers to communicate with infected computers on highly secured networks, where no direct internet connection is available.
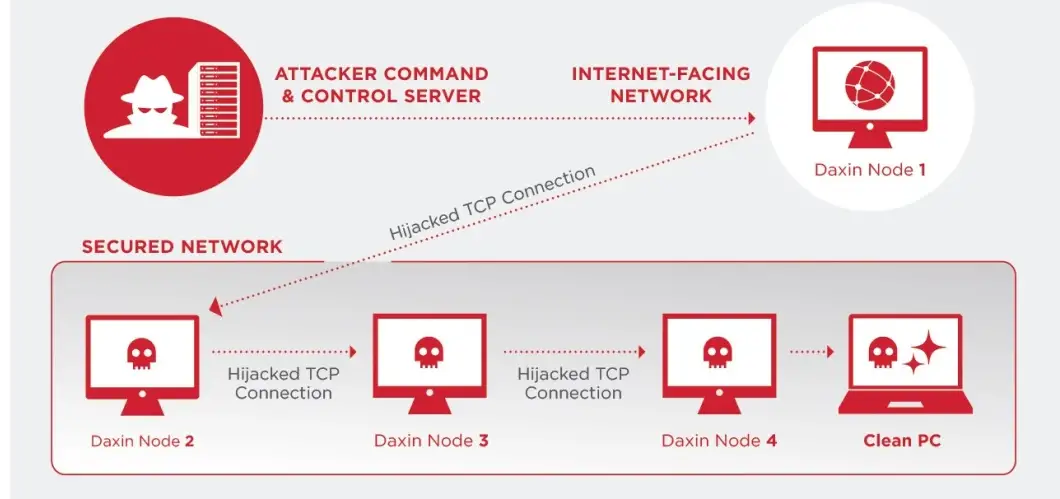
It is developed in such a way that it does not open its own network services. Instead, it uses any legitimate services which is already running on infected computers. It means this malware blend its network traffic with normal network traffic of target’s network which makes it stealthier.
It is capable of relaying its communications across the network of infected computers present within the attacked organization. This feature is used by attacker in selecting an arbitrary path across infected computer & then sending a command which gives instruction to establish requested connectivity between them.
It also features network tunneling which allow attackers to communicate with legitimate services present on victim’s network which can be reached from any infected computer.
Detail Analysis of Daxin: –
It is a backdoor which allows attacker to perform a lot of operations on victim machine like reading and writing arbitrary files, start arbitrary process & interact with them. Its main ability is stealth & communication capabilities.
It communicates by hijacking legitimate TCP/IP connections. In order to do so, it monitors all incoming TCP connections for any specific pattern. When it detects any pattern then it disconnects the legitimate user and takes over the connection. It then performs custom key exchange with remote peer. Malware can be both initiator and target of key exchange. After successfully exchanging the key, it opens an encrypted communication channel for receiving commands and sending responses. By using this hijacked TCP connection, it provides a high degree of stealth to the malware communications & also helps in establishing connectivity on networks with strict firewall rules.
Daxin built-in functionality can increase by deploying some additional components on infected computer. It provides a specific mechanism by implementing a device named as \\.\TCP4. Malicious components can open this device to register themselves for communication. Each of the components can associate a 32-bit service identifier with the opened \\.\Tcp4 handle. After doing this attacker is able to communicate with selected components by specifying a matching service identified when sending message of certain type. Driver also includes some mechanism to send back any responses.
There are also some messages which encapsulate raw network packets to be transmitted via local network adapter. It then tracks network flows, such that any response packets are captured and forwarded to remote attacker. This allows the attacker to establish connection with legitimate services which are accessible from infected machine on target’s network, where remote attacker uses network tunnels to interact with internal servers of interest.
Malware related to Daxin activity: –
| 81c7bb39100d358f8286da5e9aa838606c98dfcc263e9a82ed91cd438cb130d1 | Backdoor.Daxin (32-bit core) |
| 06a0ec9a316eb89cb041b1907918e3ad3b03842ec65f004f6fa74d57955573a4 | Backdoor.Daxin (64-bit core) |
| 0f82947b2429063734c46c34fb03b4fa31050e49c27af15283d335ea22fe0555 | Backdoor.Daxin (64-bit core) |
| 3e7724cb963ad5872af9cfb93d01abf7cd9b07f47773360ad0501592848992f4 | Backdoor.Daxin (64-bit core) |
| 447c3c5ac9679be0a85b3df46ec5ee924f4fbd8d53093125fd21de0bff1d2aad | Backdoor.Daxin (64-bit core) |
| 49c827cf48efb122a9d6fd87b426482b7496ccd4a2dbca31ebbf6b2b80c98530 | Backdoor.Daxin (64-bit core) |
| 5bc3994612624da168750455b363f2964e1861dba4f1c305df01b970ac02a7ae | Backdoor.Daxin (64-bit core) |
| 5c1585b1a1c956c7755429544f3596515dfdf928373620c51b0606a520c6245a | Backdoor.Daxin (64-bit core) |
| c0d88db11d0f529754d290ed5f4c34b4dba8c4f2e5c4148866daabeab0d25f9c | Backdoor.Trojan (32-bit core) |
| e6a7b0bc01a627a7d0ffb07faddb3a4dd96b6f5208ac26107bdaeb3ab1ec8217 | Backdoor.Trojan (32-bit core) |
File names associated with Daxin activity: –
- “ipfltdrvs.sys”
- “ndislan.sys”
- “ndislan_win2008_x64.sys”
- “ntbios.sys”
- “patrol.sys”
- “performanceaudit.sys”
- “print64.sys”
- “printsrv64.sys”
- “prv64.sys”
- “sqlwriter.sys”
- “srt.sys”
- “srt64.sys”
- “syswant.sys”
- “usbmrti.sys”
- “vncwantd.sys”
- “wantd.sys”
- “win2k8.sys”
- “wmipd.sys”
- “[CSIDL_SYSTEM]\drivers\pagefile.sys”
- “[CSIDL_SYSTEM]\spool\drivers\ntds.sys”
Malware observed during overlapping activities: –
| 705be833bd1880924c99ec9cf1bd0fcf9714ae0cec7fd184db051d49824cbbf4 | suspected Backdoor.Daxin |
| c791c007c8c97196c657ac8ba25651e7be607565ae0946742a533af697a61878 | suspected Backdoor.Daxin |
| 514d389ce87481fe1fc6549a090acf0da013b897e282ff2ef26f783bd5355a01 | Trojan.Emulov (core) |
| 1a5c23a7736b60c14dc50bf9e802db3fcd5b6c93682bc40141d6794ae96138d3 | Trojan.Emulov (dropper) |
| a0ac5f7d41e9801b531f8ca333c31021c5e064f13699dbd72f3dfd429f19bb26 | Trojan.Owprox (core) |
| aa7047a3017190c66568814eb70483bf74c1163fb4ec1c515c1de29df18e26d7 | Trojan.Owprox (dropper) |
Remediation Measures: –
To avoid such types of attacks we follow certain measures like: –
- Always be careful while downloading any documents.
- Ensure Endpoint protection and Antivirus and Anti Malware should be configured and with hardening on all end nodes.
- Opensource/Pirated Software’s execution should be prohibited.
- Web proxy should be implemented.
- Security patches need to be applied on all end devices.
- Data-Loss Prevention (DLP) need to be implemented on the end devices.
- Implementation of Web Application firewall (WAF) with strong security policy, consider using Load balancer in front of WAF for high traffic
- Configure Outbound and Inbound rules on web and application server and ports need to filtered via firewall.
- Filter the ports for any traffic coming in with parameter level IPS.
- NextGen Firewalls should be implemented with firmware and malicious signature with hardly configured with best security practices.



